Port Forwarding With Localtunnel (without router access)
Previously LordVordex published a post on using Servio to forward ports without router access,
Serveo.net is great for port forwarding but due to some issues the service sometimes gets temporarily disabled.
Luckily serveo.net isn’t the only port forwarding / tunnelling service available. Alternatively we can use ngrok or localtunnel for achieving the same effect.
In the following steps I will be explaining how to use localtunnel as that is my preferred one.
About Localtunnel:
Localtunnel allows you to easily share a web service on your local development machine without messing with DNS and firewall settings. It will assign you a unique publicly accessible url that will proxy all requests to your locally running webserver.
Now to make localtunnel accessible globally through any network you will first need to install nodejs on your machine, rest assured everything in here is a very simple process.
Firstly go to nodejs.org from your Kali Linux machine.
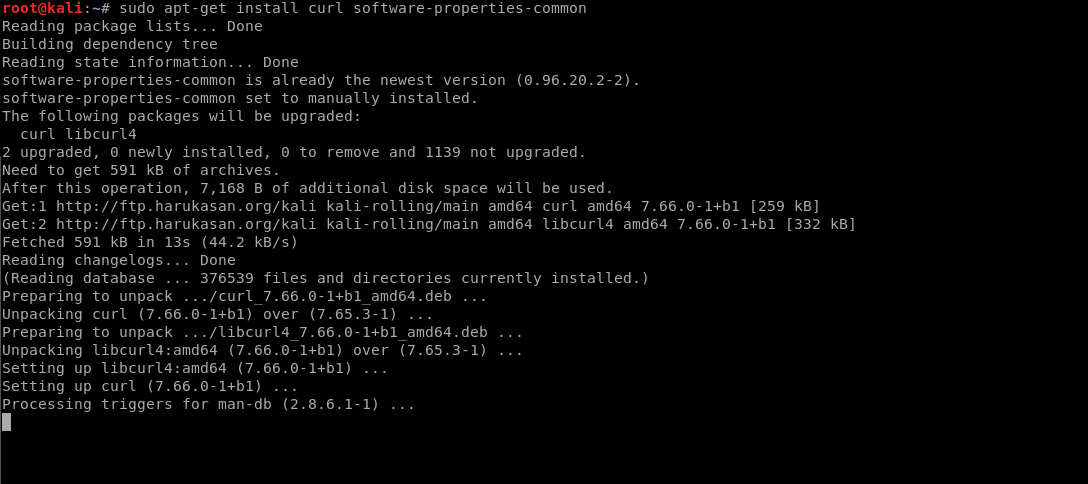
Here you will find the latest version that’s available for your operating system. Now to install nodejs on your Kali machine via packet manager open terminal and first run the following commands:
apt-get update apt-get install curl software-properties-common
The above commands will first update your software sources, and install needed software for nodejs, when its done run the following command to download the nodejs installer:
curl -sL https://deb.nodesource.com/setup_13.x | sudo bash -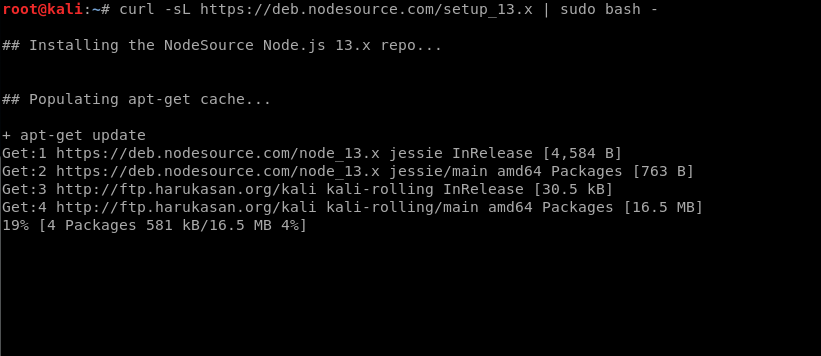
Note : you can change the ‘ 13 ‘ in the command to whichever version of nodejs you want installed. Currently the latest version is 13 so that’s what I’m using.
That’s it now you have nodejs and npm installed.
If you want to again which version of nodejs and npm you have installed you can always do so by running:
node –v npm –v
Now to Install Localtunnel globally to make it accessible anywhere run :
npm install -g localtunnel
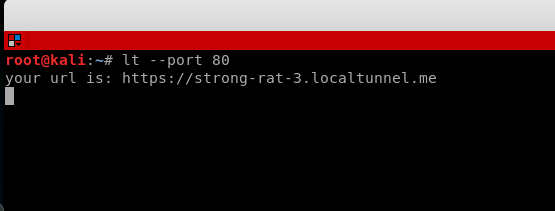
Its all done now whenever you want to Start a webserver on some local port (eg http://localhost:80) use the command line interface to request a tunnel to your local server:
lt --port 80
This will give you a url which you can open on any device in the world and it will tunnel the port to your machine. Just make sure you have your apache service running from your kali machine before accessing the link through another device.
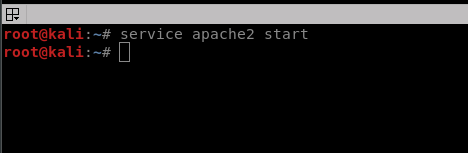
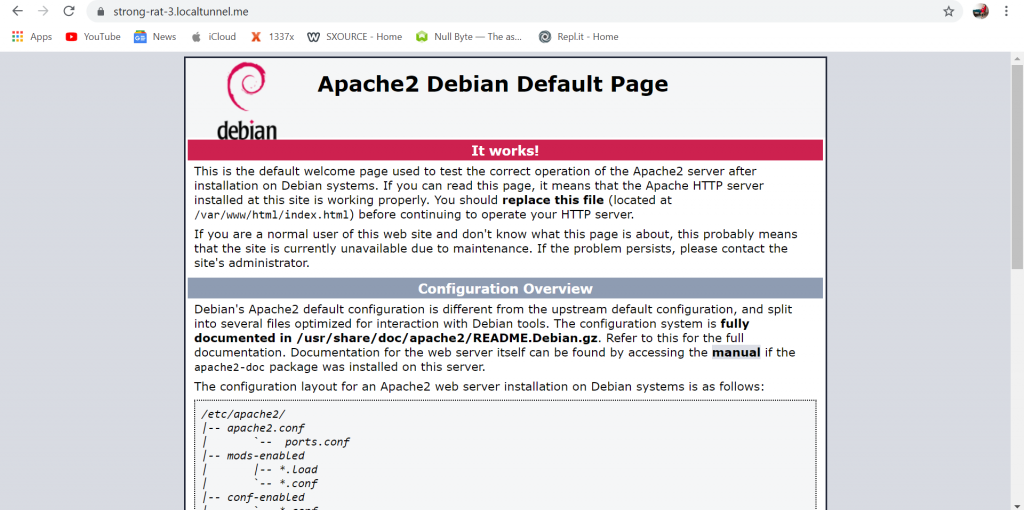
Put a /Evil Files (or whatever name with which you have saved your evil files in and it’ll open on the other device outside your network)
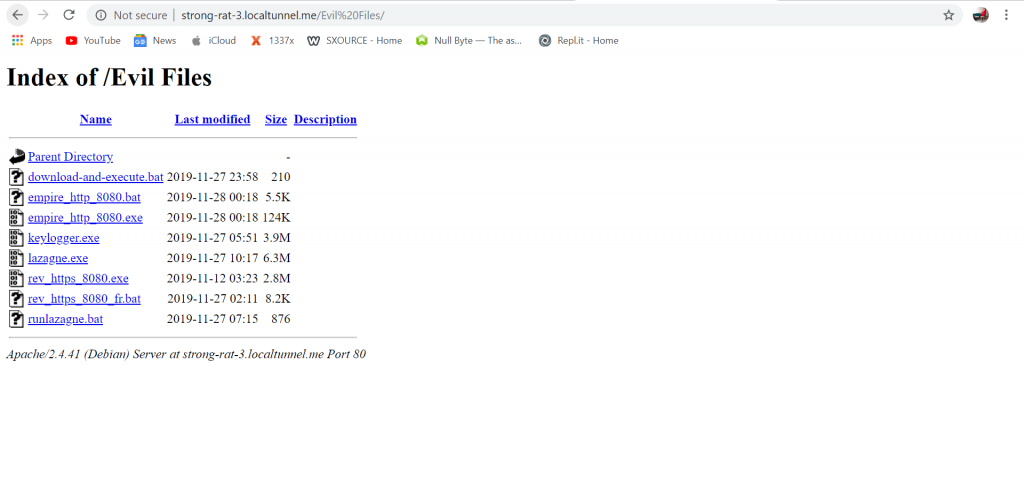
Also create your payload with the desired port and use localtunnel to tunnel that port to so that you can get a reverse connection from the target device.
Hope this helps, Happy tunnelling 🙂
Leave A Reply
You must be logged in to post a comment.




12 Comments
i use node -v it give me …. v10.17.0
i use npm -v it give me ….. 5.8.0
i use lt –port 80 … nothing happened
can you help me please
Same here
node -v gives v13.3.0
npm -v gives v6.13.1
lt –port 80 and I get nothing. not sure what i’m doing wrong. I’ve tried different ports and nothing still.
There are many services similar to localtunnel that you can use once node-is is installed. Run this command and it should work.
ssh -R 80:localhost:8080 ssh.localhost.run
It may be possible that localtunnel might be down for some time so run this command and it should work:
ssh -R 80:localhost:80 ssh.localhost.run
This service is similar to localtunnel. Let me know if you need anything else
Or you can try
ssh -R 80:localhost:8080 ssh.localhost.run
Whichever works as per your needs.
Something went wrong opening the port forward, check your SSH command output for clues!
how to stop it?
I got this while browsing from public internet.
Something went wrong opening the port forward, check your SSH command output for clues!
[email protected]: Permission denied (publickey)
It’s getting like this ,what to do??
it still shows there’s nothing here when its run
How to configure it to work with BeEF which uses port 3000?
let us suppose take my private ip address as 192.168.0.10, so what will be my Lhost and Lport in my payload and in the meterpreter session …. please help