How To Start a Fake Access Point (Fake WIFI)
As you might know, untrusted Wifi networks can be extremely dangerous if you happen to be connected to them. In this article I am going to show you how to create a simple yet dangerous access point. We will be using a well-known wireless card that supports monitor mode which is the Alfa AWUS036NHA USB wireless adapter, you can find it here. Or you can use any wireless adapter that supports monitor mode, Alfa AWUS036NHA is highly recommended though.
How dangerous can an access point be?
If you are in a random place and happened to be connected to an open network, it doesn’t matter what device you are connected with, your data will be visible to the person who is controlling the access point. Not only that, but the person in control can have a complete control over your device by hooking you with a malicious web page or a backdoor.
How can you control the devices that are connected to your fake access point?
There are many methods to do that. You can redirect the connected user to a specific malicious website that you also control and hook their devices. Furthermore, you can run and execute backdoors by using python MITM scripts on the connected devices. You also can replace the download files that the connected users requests on the fly without being suspicious, we will be doing that in the next article.
Lets take a look on how to start a fake AP…
STEP 1:
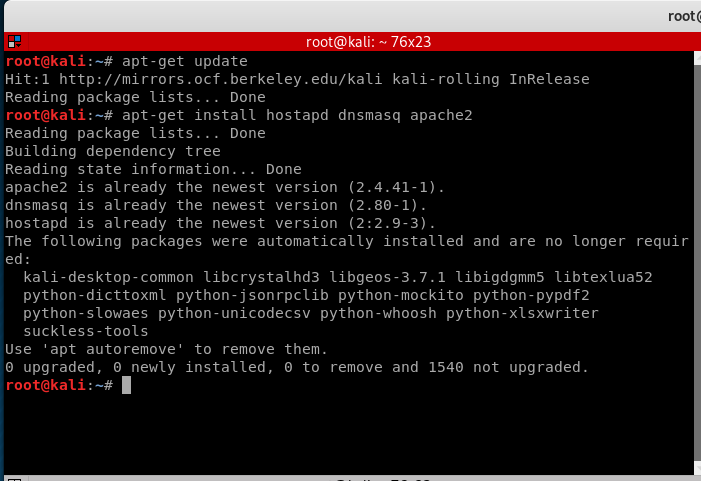
First we will need to update Kali Linux to the latest version and install the required packages.
apt-get update apt-get install hostapd dnsmasq apache2
STEP 2:
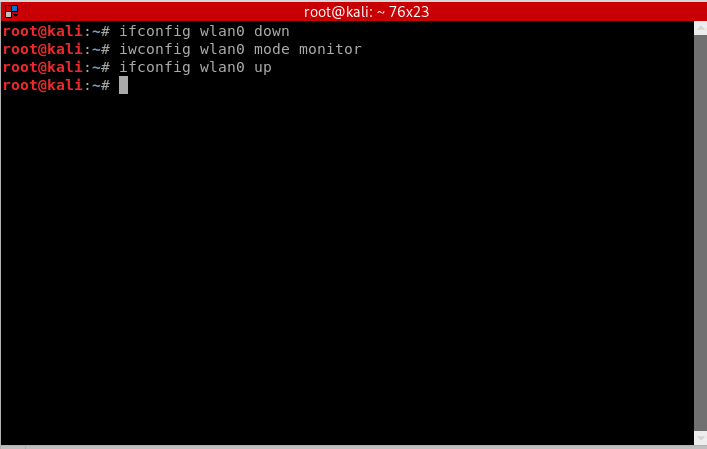
We need to put the wireless card in monitor mode to allow us to sniff the packets in and around the network. You can use this method:
ifconfig wlan0 down iwconfig wlan0 mode monitor ifconfig wlan0 up
Or if that didn’t work, you can use this method instead:
airmon-ng start wlan0
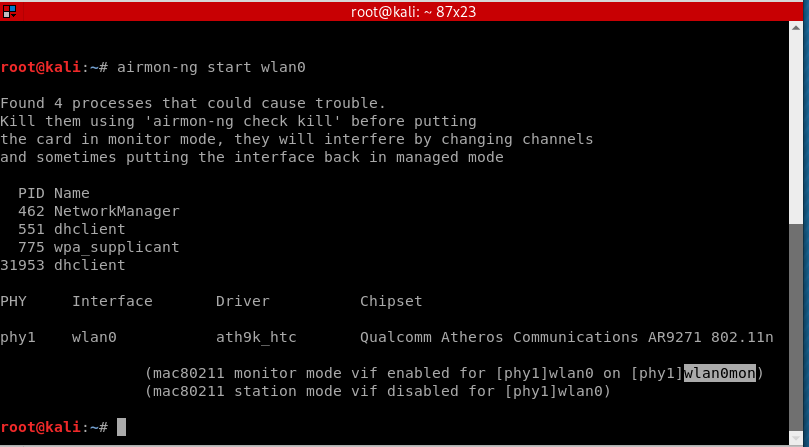
Note that the wireless adapter’s name has changed from wlan0 to wlan0mon, so we need to use the new given name which is wlan0mon.
STEP 3:
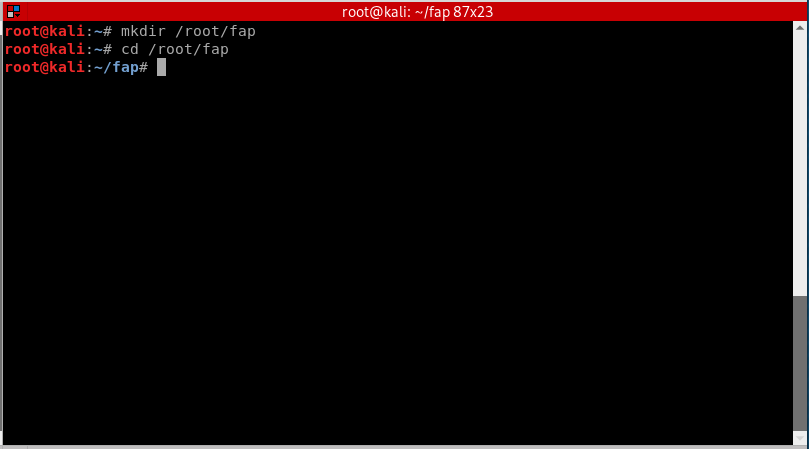
To make things organized and easier to work with, we will make a new directory in root and call it “FAP” or fake access point.
mkdir /root/fap cd /root/fap
- mkdir: command for making a new directory in linux.
- cd: command to navigate to a specific directory, in this case its fap.
STEP 4:
Once we are in /root/fap that we created, we will now setup a new hostapd configuration file and write instructions inside. Hostapd (Host access point daemon) is a software access point that lets the user to use his/her wireless adapter to broadcast several access points at the same time.
nano hostapd.conf
- nano: is a command line text editor included in most Linux installations.
- hostapd.conf: is the name of the configuration file that we created.
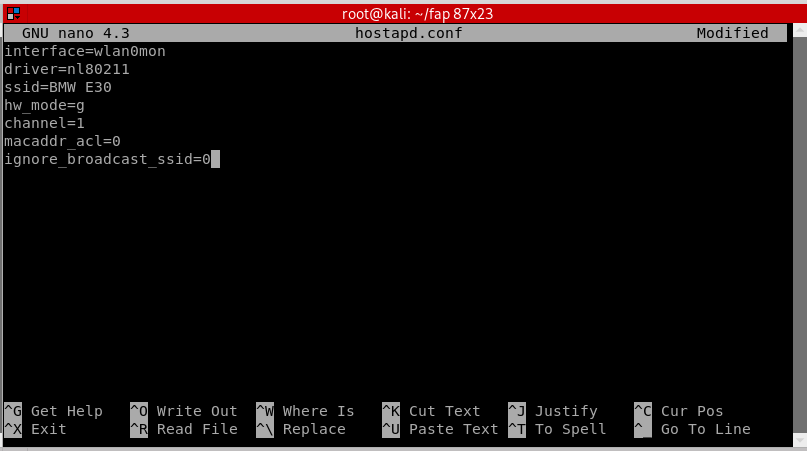
Now inside hostapd.conf, we need to setup instruction orders for it.
interface=wlan0mon driver=nl80211 ssid=[Name of the Wifi] hw_mode=g channel=[Channel number] macaddr_acl=0 ignore_broadcast_ssid=0
After writing these instructions, press CTRL+X, then Y, then ENTER. Now we are all set for hostapd.conf.
- interface: The name of the wireless adapter that we are using in monitor mode.
- driver: The supported driver for hostapd.
- ssid: The broadcasted Wifi name.
- hw_mode=g : Simply instruct it to use 2.4GHz band.
- channel: The channel number to use for the fake access point.
- macaddr_acl=0: Tells hostapd to not use MAC filtering. [macaddr_acl=1] tells it to use MAC filtering.
- ignore_broadcast_ssid=0 : To make the fake access point visible and not hidden.
STEP 5:
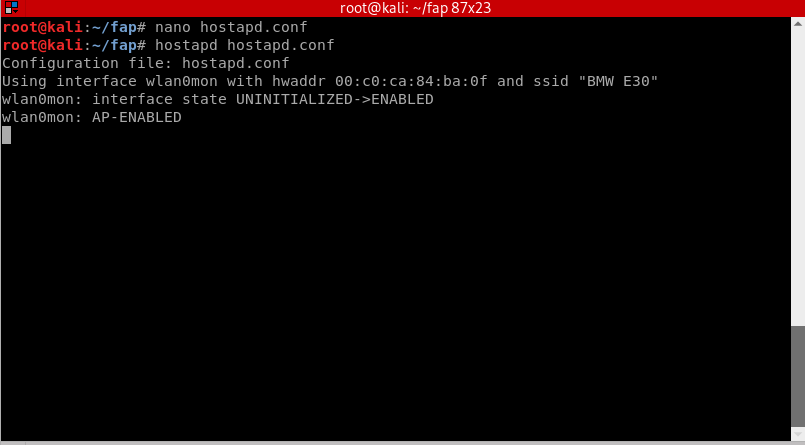
Start the fake access point by doing:
hostapd hostapd.conf
You will notice that our access point will appear as an open Wifi network. Now open a new terminal window without closing the previous one. In the new terminal window, navigate back to the fap directory by doing:
cd /root/fap
STEP 6:
We will be using dnsmasq for this step. Dnsmasq is a Dynamic Host Configuration Protocol (DHCP) server that is used to resolve dns requests from or to a machine and also acts as DHCP server to allocate IP addresses to the clients. It is fast and serves a great purpose that fits our needs. We will create a configuration file for dnsmasq and put some instructions in it, just like what we did previously with hostapd. To create the file:
nano dnsmasq.conf
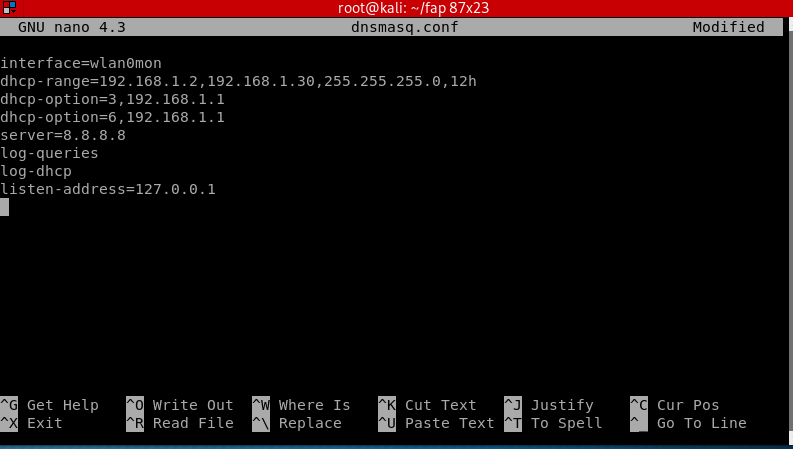
Add these instructions inside:
interface=wlan0mon dhcp-range=192.168.1.2, 192.168.1.30, 255.255.255.0, 12h dhcp-option=3, 192.168.1.1 dhcp-option=6, 192.168.1.1 server=8.8.8.8 log-queries log-dhcp listen-address=127.0.0.1
- dhcp-range: IP address range for the connected network clients. 12h is the amount of hours until the lease expires.
- dhcp-option=3: Gateway IP for the networks.
- dhcp-option=6: For DNS Server followed by IP address
- server: DNS server’s address
- log-queries: Log the results of DNS queries handled by dnsmasq.
- log-dhcp: Log all the options sent to DHCP clients and the tags used to determine them.
- listen-address: Links the DHCP to the local IP address which is 127.0.0.1.
Press CTRL+X, then Y, then ENTER. Now we are all set for dnsmasq.conf.
STEP 7:
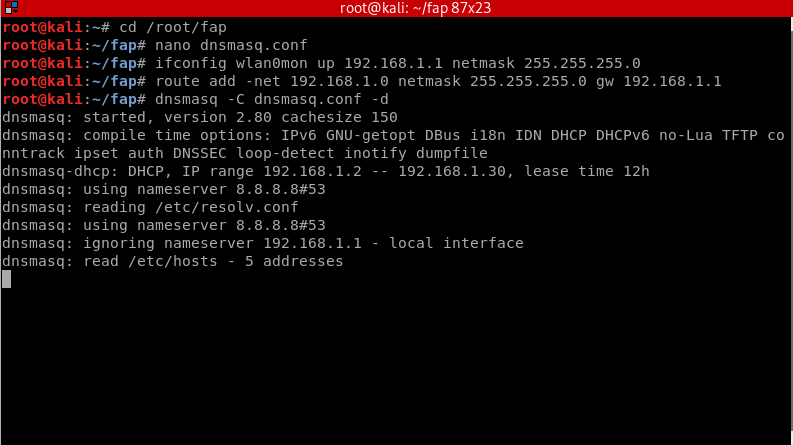
Now we need to assign the interface a network gateway and netmask and then add the routing table.
ifconfig wlan0mon up 192.168.1.1 netmask 255.255.255.0 route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.1
Start the DNS server by doing:
dnsmasq -C dnsmasq.conf -d
- dnsmasq -C: Specifies a different configuration file.
- -d : Tells it to keep the user id without changing it.
Open a new terminal window to continue with the next step.
STEP 8:
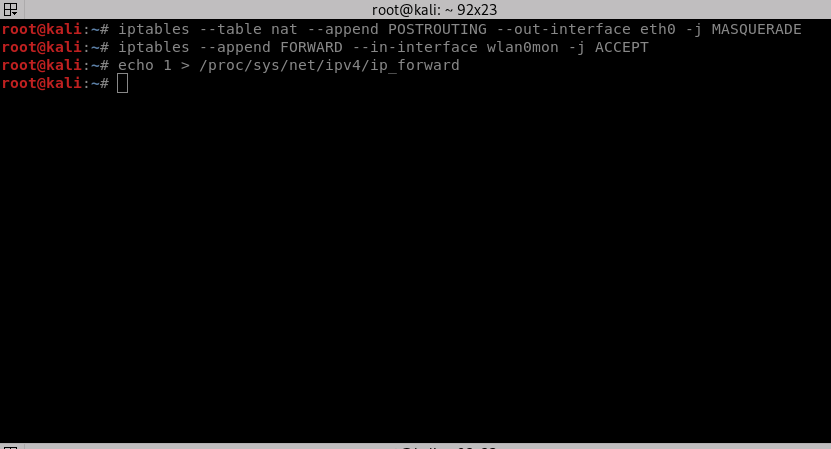
To provide the users with internet access, we need to forward traffic from eth0, the virtual wireless adapter that is connected to the internet, to wlan0mon. This will help you perform various attacks that can give you complete access to the user’s device. If you don’t want the users to have internet access, skip this step.
iptables --table nat --append POSTROUTING --out-interface eth0 -j MASQUERADE iptables --append FORWARD --in-interface wlan0mon -j ACCEPT
- First command: Interface name that is used to forward traffic from.
- Second command: Interface name to receive the packets or the interface that is being forwarded to.
Now execute this command to enable IP Forwarding:
echo 1 > /proc/sys/net/ipv4/ip_forward
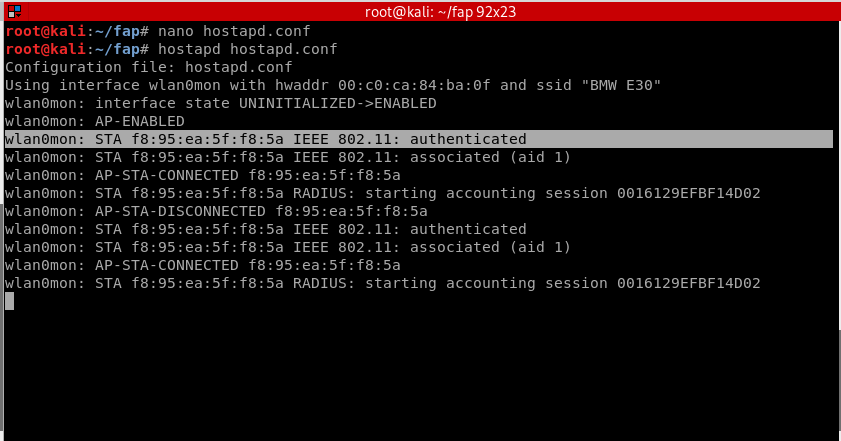
STEP 9:
Test out your fake access point by playing the victim. Connect to your network and access any website you like, you should be able to see all the packets transmitted on the fly in the terminal.
Hostapd will show the mac address as soon as a device has connected to the network.
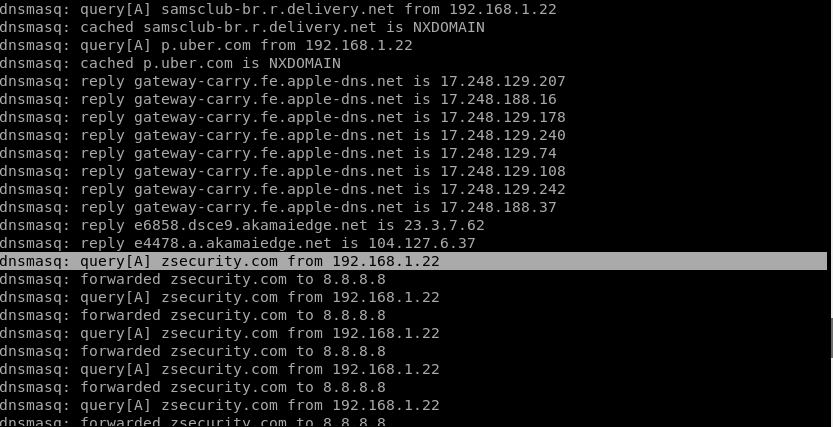
On the other terminal window where dnsmasq is running, you will find out what the device is trying to access in details. For this example, the user is accessing zsecurity.com.
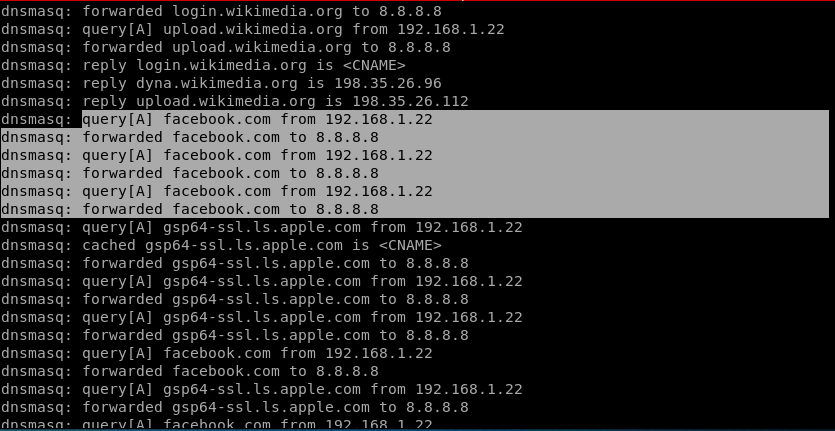
For this example, the user is accessing facebook.com and so on.
Closure:
This shows how powerful a fake access point can be. Once you got your targets connected, you will have many attacks available that could eventually control the user’s device.
Setting up a fake access point can teach you the security of the network, and how a network typically works. It will also show you what the person in control of the network can do with the connected devices. As we saw previously, you can pretty much have access to all the packets that the user’s device is requesting.
If you happen to be connected to a public and unsecure network, A simple way to solve and protect yourself is to use a reputable VPN. A VPN will decrypt the packets making it impossible for the person controlling the network from seeing what the user is accessing. ZSVPN is highly recommended as it doesn’t store any data from the user. You can download it here.
Leave A Reply
You must be logged in to post a comment.




91 Comments
My realtek adapter that I bought on this page doesn’t get renamed to wlan0mon it stays wlan0. It also doesn’t work with tools like fluxion. I will try to do it using this tutorial later and update this.
Hello there,
It doesn’t have to be renamed to “wlan0mon”. You can still use the card as “wlan0” just fine.
What issues are you facing in Fluxion? can you be more specific please.
Hey maythem i wanted to ask you about the fap. Zip files you said that you will include a link to download this file but i didn’t saw this link
Can you please help me with that
hello Mayhem Allan,
I need some help,
I am facing some issue, actually, I followed your every step as in included in your video but isn’t showing the second twin open network if I search in wifi connection, is my wifi adpater does not support these actions?
I have been using TPLINK 2.4 GHz adapter
kindly help thankyou
iwconfig wlan0 mode monitor
Error for wireless request “Set Mode” (8B06) :
SET failed on device wlan0 ; Operation not permitted.
Hello there,
What kind of network adapter are you using?
Howdy excellent tutorial btw. Iv run into one issue,
Everything else works fine but when I put in “dnsmasq -C dnsmasq.conf -d” I get a error of
“No servers found in /ect/resolve.conf, will retry”
Iv looked through the whole comment section on YouTube, and this comment section and cant find the answer to fix it. Your help would be greatly appreciated
now, it works. Thank you very much!
Glad you figured it out 🙂
My android says “Failed to obtain IP address” when trying to connect
Hello Christopher,
If you want to set it to 5 GHz, Just replace “g” with “a”
Like this: hw_mode=a
Hope this helps.
Hello,
What kind of network adapter are you using?
It is possible that it doesn’t support 5GHz mode.
Hello Christopher,
lets check a couple of things first, have you tested the fake AP using 2.4 GHz? and did it work properly?
Also, double check if your network interface is called wlan0 and not wlan0mon after you started monitor mode (by using ifconfig). And double check that the naming is the same in the hostapd.conf for “interface=”
Hello,
The issue is most likely linked with the channel you are working on.
First lets try setting up the wireless card in monitor mode using the manual method which is:
ifconfig wlan0 down
iwconfig wlan0 mode monitor
ifconfig wlan0 up
Once that is done, edit your hostapd.conf file using nano and change the channel to 36 “channel=36”
Now run hostapd and test it and let me know if the problem persists.
Hello,
Hostapd cannot create a dual-band AP (5ghz and 2ghz at the same time) even with two cards. But it can create multiple APs with the same SSID.
Sir, how to upstream the internet in the fake acess point so that user don’t get suspicious…
Hello,
Please revise step 8 and step 9.
If that didn’t answer your question please let me know.
Hello Maythem,
After connecting to my android is shows no internet access even after following step7.
Hello Riconan,
Does this issue only occur on you android device? please try with different devices and let me know.
Also can you show me the output of ifconfig please.
Hi Mythem,
when I do this commend (apt-get install hostapd dnsmasq apache2) I got this error:
Could not connect to http.kali.org:80 (192.99.200.113), connection timed out.Can you please help me?
hostapd is saying handle_probe_req: send failed and I’m unable to connect on any devices..
pls help
Hello Legend,
lets gather some information to solve this, what wireless adapter are you using?
Is this your first time running hostapd? if not, did it have issues before?
Can you copy and paste the whole hostapd output?
After step 5 the result is —-
Configuration file: hostapd.conf
Could not read interface wlan0mon flags: No such device
nl80211: Driver does not support authentication/association or connect commands
nl80211: deinit ifname=wlan0mon disabled_11b_rates=0
Could not read interface wlan0mon flags: No such device
nl80211 driver initialization failed.
wlan0mon: interface state UNINITIALIZED->DISABLED
wlan0mon: AP-DISABLED
wlan0mon: CTRL-EVENT-TERMINATING
hostapd_free_hapd_data: Interface wlan0mon wasn’t started
Hi Surya,
It seems like wlan0mon isn’t detected or the name is different.
Can you copy and paste the output of iwconfig after doing step 2 please?
Configuration file: hostapd.conf
Line 2: invalid/unknown driver ‘n180211’
1 errors found in configuration file ‘hostapd.conf’
Failed to set up interface with hostapd.conf
Failed to initialize interface
wireless adapter using PANDA PAUO6
Hi,
Could you please tell me the brand & chipset of your wireless adapter?
nl80211 driver initialization failed.
wlan1mon: interface state UNINITIALIZED->DISABLED
wlan1mon: AP-DISABLED
wlan1mon: CTRL-EVENT-TERMINATING
hostapd_free_hapd_data: Interface wlan1mon wasn’t started
bash: /proc/sys/net/ipv4/ip_forward: Permission denied
After step 5 this came up
Can you tell what’s the issue
root@kali:~/fap# hostapd hostapd.conf
Configuration file: hostapd.conf
nl80211: Could not configure driver mode
nl80211: deinit ifname=wlan0 disabled_11b_rates=0
nl80211 driver initialization failed.
wlan0: interface state UNINITIALIZED->DISABLED
wlan0: AP-DISABLED
wlan0: CTRL-EVENT-TERMINATING
hostapd_free_hapd_data: Interface wlan0 wasn’t started
Hi,
Could you please tell me what wireless adapter are you using?
good day. Please i urgently need your help. I am working on IoT devices in my home . i want to sniff packets between my mobile app and IoT devices and get wireshark to capture for me to analyze. I followed the steps in this article to create the fake access point and then connect my IoT devices. Iam having the following issues
after changing to monitor mode the usb wifi card Alfa AWUS036ACH changed back to master after running the hostapd, setting the ip, run and dnsmasq.
I noticed the ssid is not showing in under my wireless or android phone.
My set up is windows 10 with Vmware workstation and kali 2019.04 vm installed.
What can i do? or how can i set up to capture communication of my IoT devices and the 802.11 communication.
anu
Hi,
Is there any errors showing up when running hostapd?
Alfa AWUS036ACH is known to have some bugs while in monitor mode, have you installed its drivers correctly?
check out this video https://www.youtube.com/watch?v=zZG65GkWGdU
If you have installed everything correctly, try changing the channel number on your hostapd file. Let me know how it goes.
I returned the card and now bought AWUS036NH. The issue with this is that is not capturing 802.11 packets once i changed to
monitor mode. How can i use the fake access point above to capture 802.11 packets between my mobile app and the IoT devices ?
I have exhausted all i know. Any pointer will be greatly appreciated.
Summary of my setup
host
Windows 10
Vmware workstation and kali linux vm with usb adapter connected to kali vm and fake access point created using your seteps above.
Hi,
Try this, once you are finished with step 8, open a new terminal and do:
dnsspoof -i wlan0mon
(or whatever your wireless adapter name is)
i can not access the internet even after 8th step. pls help
Hi,
Can you please copy and paste the output of the command ifconfig in here?
Configuration file hostapd. Confu
nl80211 could not configure driver mode
Nl80211 driver initilization failed
Nl80211 deinit ifname=wlan1 disabled_11b_rates=0
Hi,
Please try out the following commands and let me know how it goes.
airmon-ng check
killall wpa_supplicant
Very interesting
Too bad I do not have my equipment with me to test this 😉
However I have a question in the iptable part
iptables –table nat –append POSTROUTING –out-interface eth0 -j MASQUERADE
Looks like the out going part ?
And
iptables –append FORWARD –in-interface wlan0mon -j ACCEPT
Is the inbound part ?
And your comment says the contrary , I really do not know I am discovering those commands
It is a simple and humble question
In the ‘iptables –table nat –append POSTROUTING –out-interface eth0 -j MASQUERADE’ – part that’s what gives your targets internet connectivity, if you are using a laptop without Ethernet cable please make sure to rename ‘eth0’ to whatever interface has internet connectivity. If not this results in “No internet connection” error when trying to connect to your fake AP.
E.g. on my laptop I use 2 alfa adapters, so it’s wlan0, wlan1, and wlan2, what I done is I put wlan1 into monitor mode and I used wlan0 for internet connectivity for my targets. So my IP tables looked like –
—> iptables –table nat –append POSTROUTING –out-interface wlan0 -j MASQUERADE
–> iptables –append FORWARD –in-interface wlan1mon -j ACCEPT
Hope this helps, it didn’t answer the question but I wanted to address you about this. happy hacking 🙂
Awesome glad you figured it out 🙂
I have followed every step thoroughly multiple times however my target (me) am not able to connect to the internet. The access point does show in the menu of available wifi networks but when trying to connect to it I don’t get any internet connectivity. On iPhone it says “No internet connection” when I click on the network, and on windows and android similar thing happens. I am using a laptop with an alfa adapter.
Same problem
Hi
In kali after
airodump-ng –bssid (Mac Address ) –channel (x) write text wlan0
It dosen’t show the clients connected to the network.
I am using adapter which supports monitor mode and checked that it’s in it.
What the problem I am getting. Please respond
Having the same problem. Wont connect on my android or laptop
Yeah i also try to connect to my devices but it fails to connect!!
Same problem
Hi, sorry but in this article we are not using airodump-ng!
Please ask in the forums here https://zsecurity.org/forums/
Configuration file: hostapd.conf
nl80211: Could not configure driver mode
nl80211: deinit ifname=wlan0 disabled_11b_rates=0
nl80211 driver initialization failed.
wlan0: interface state UNINITIALIZED->DISABLED
wlan0: AP-DISABLED
wlan0: CTRL-EVENT-TERMINATING
hostapd_free_hapd_data: Interface wlan0 wasn’t started
This is my problem ,can u say wjats the solution for it???
Hi,
Please try this command and then run it again:
sudo rfkill unblock wifi
If that didn’t work, what type of adapter are you using?
Having major problems not able to connect the the fake AP wireless network.
*us 001 Device 003: ID 0bda:818b Realtek Semiconductor Corp. RTL8192EU 802.11b/g/n WLAN Adapter*
*configuration: broadcast=yes – driver=rtl8192eu – driverversion=5.7.0-kali1-amd64 – multicast=yes – wireless=unassociated*
I see you are using Realtek. Have you installed the drivers using this video?
https://www.youtube.com/watch?v=zZG65GkWGdU
hey everything was a success but the website doesn’t appear on other devices
perhaps did i have to change the address on step 7 thanks
hi Maythem
when i but in command dnsspoof -i wlan0
root@kali:~/fap# dnsspoof -i wlan0
bash: dnsspoof: command not found
root@kali:~/fap#
thats all i get if connect to the fap att work but well not redirect to my apache server
Hi Mohazab,
Try installing the suite for it using this command:
sudo apt-get install dsniff
Hi Maythem,
There is an issue in the last step the open network is available and is shown in the list but when i click on it. It doesn’t show the upgrade page just connects automatically and in the terminal when i try using the last step again wpa_keys it shows empty set again. where is the issue here .. ?
Thanks Aman
Hi Aman,
Please try this:
Edit your dnsmasq.conf by doing nano dnsmasq.conf
Change the last line “listen-address” with “address=/#/192.168.1.1”
Save and exit.
Then restart the attack.
Above matter is working,but access point is created if anybody is not connect ,after 5min its not working it telling failed
if any body connected its working its not disconnect
Try it using a different channel
hello Mayhem Allan,
I need some help,
I am facing some issue, actually, I followed your every step as included in your video but isn’t showing the second twin open wifi connection after complete the last attacking section, is my wifi adapter does not support this actions?
I have been using TPLINK 2.4 GHz adapter(it can support monitor mode and packet injection)
or did I missed something ? but I tried multiple times
kindly help thankyou
Hi, are there any errors showing up?
TPLINK 2.4 GHz adapter can work but its not well supported for these kinds of attacks.
Hello Maythem,
I try to connect the Wifi with two of my android devices but it fails to connect
it only says “saved” so how can i fix this issue??
Hi,
Can you please show me the error you are facing?
i got this message
Configuration file: hostapd.conf
nl80211: Could not configure driver mode
nl80211: deinit ifname=wlan0mon disabled_11b_rates=0
nl80211 driver initialization failed.
wlan0mon: interface state UNINITIALIZED->DISABLED
wlan0mon: AP-DISABLED
wlan0mon: CTRL-EVENT-TERMINATING
can you please help me how to resolve it
hostapd_free_hapd_data: Interface wlan0mon wasn’t started
Hi, please check if the wireless adapter name is the same as the one in hostapd.conf
Hi maythem….i was able to create the fake access point but when i run aireplay-ng to deauth i stopped seeing the opened wifi please help
Hi, you’d need to create another virtual adapter to lunch the deauth with it. Or you can use a different wireless adapter to do that as well
hi good sir
since the video came out i been trying and i am stuck here as it gives me the error
root@kali:~/fap# hostapd hostapd.conf
Configuration file: hostapd.conf
Could not read interface wlan0mon flags: No such device
nl80211: Driver does not support authentication/association or connect commands
nl80211: deinit ifname=wlan0mon disabled_11b_rates=0
Could not read interface wlan0mon flags: No such device
nl80211 driver initialization failed.
wlan0mon : interface state UNINITIALIZED->DISABLED
wlan0mon : AP-DISABLED
wlan0mon : CTRL-EVENT-TERMINATING
hostapd_free_hapd_data: Interface wlan0mon wasn’t started
i seriously need help with this
hoping for your understanding
looking forward for your help
plz help me out
Hi, what adapter are you using?
Also, please check if the wireless adapter name is the same as the one in hostapd.conf
Hello, after running the command apt-get install hostapd dnsmasq apache2 I got this error message
The following packages have unmet dependencies:
gsettings-desktop-schemas : Break: mutter (< 3.31.4) but 3.30.2-8 is to be installed
E: error, pkgProblemResolver::Resolve generated breaks, this may be caused by held packages.
Please help me I tried everything!!!!
Hi,
Please try running this command: sudo apt install gcc-8-base mutter
hostapd hostapd.conf
after typing this the terminal will show bash.
Hi,
Can you please paste the exact error you are having?
yes
and no command will work before typing sudo su
sir please help me
to solve this problem
i will try many time
hostapd hostpad.conf they will show bash.
how to check our network adapter
Hello Maythem, Thanks for great article, it is really very helpfull.
Seems I am missing one last configuration , beause I have successfully configured it as you did it here, except I use airbase-ng for creating Fake Access Point. I can connect to it via mobile , the request is sent and forwarded , but it doesnot get back.
I am using kali linux 2020.3 in VirtualBox
This is the output of dnsmasq
dnsmasq: query[type=65] 26-courier.push.apple.com from 192.168.1.10
dnsmasq: forwarded 26-courier.push.apple.com to 8.8.8.8
dnsmasq: forwarded 26-courier.push.apple.com to 10.0.3.3
dnsmasq: reply smp-device-content.apple.com is
dnsmasq: reply smp-device-content.apple.com.edgekey.net is
dnsmasq: reply e9959.e9.akamaiedge.net is 104.111.251.62
dnsmasq: query[type=65] 26-courier.push.apple.com from 192.168.1.10
dnsmasq: forwarded 26-courier.push.apple.com to 8.8.8.8
dnsmasq: query[type=65] 26-courier.push.apple.com from 192.168.1.10
dnsmasq: forwarded 26-courier.push.apple.com to 8.8.8.8
dnsmasq: query[type=65] 26-courier.push.apple.com from 192.168.1.10
dnsmasq: forwarded 26-courier.push.apple.com to 8.8.8.8
dnsmasq: query[A] 26-courier.push.apple.com from 192.168.1.10
dnsmasq: forwarded 26-courier.push.apple.com to 8.8.8.8
dnsmasq: reply 26-courier.push.apple.com is
Hi,
Please try connecting with a different device to make sure that the issue is not from a specific device.
Hello there I have tried to perform the attack but I am having 3 types of issue.
1- fake access point not showing in any device after 30-40 seconds
2- when we connect to fake access point not Opening any Upgrade page where user enters their password.
3- many of the time when dns spoof command perfomed it shows that unknown physical layer type 0*323
I have tried it many of the times please give me the solution .
Configuration file: hostapd.conf
nl80211: Could not configure driver mode
nl80211: deinit ifname=wlan0mon disabled_11b_rates=0
nl80211 driver initialization failed.
wlan0mon: interface state UNINITIALIZED->DISABLED
wlan0mon: AP-DISABLED
wlan0mon: CTRL-EVENT-TERMINATING
I am geting this error,
I tried many thing like airmon-ng check kill,check interface name amd i am using MediaTek 802.11n wlan card.
plz help me how to fix this.even i tried it with many scripts like airgeddon and fluxion it continues with same error.
Hello Maytham very good tut, however when i am trying to access the rogue ap from victim machine, dnsspoof is not redirecting to the phishing page (firmware upgrade) i have accessed/checked 127.0.0.1 from kali machine and it loads the page just fine though, please can you advise?
Many thanks
I am facing the same issue, did you find any solution?
Thank you!
Hello,
Happy new year!
Since few days, I am facing the same problem with different techniques.
I run the commands with errors. I can see the new WIFI network from my phone or computer but when I try to connect to it I receive the message:”Unable to join the network”.
I followed every step of this tutorial, everything is under “wlan0”. I am using the adapter Nation with chipset realtek RTL8811AU for 2.4 &5GHz.
I don’t meet any problem when I spoofed or do MITM attacks.
Stupid question but in the .conf docs, should I change anything else in addition of the “wlan0” and the channel?
Thank you
Hello,
where can i get the link to download fap.zip file?
Help me out!!!
Thank you
Cant run the command
root@kali:~/fap# hostapd hostapd.conf
Configuration file: hostapd.conf
nl80211: Could not configure driver mode
nl80211: deinit ifname=wlan0 disabled_11b_rates=0
nl80211 driver initialization failed.
wlan0: interface state UNINITIALIZED->DISABLED
wlan0: AP-DISABLED
wlan0: CTRL-EVENT-TERMINATING
hostapd_free_hapd_data: Interface wlan0 wasn’t started
adapter – mediatek
I followed each and every steps and have run the commands without errors. I can see the new WIFI network from my phone or computer and I am able to connect to it without getting directed to the phishing page (firmware upgrade). I have accessed/checked 127.0.0.1 from kali machine and it loads the page just fine though, please can you advise?
Hi!
How can we gain access to the victim’s camera using the fake AP we just created??
i am trying to run Mana-Tool “start-nat-simple.sh” i am getting below error, kindly need your support.
Configuration file: /etc/mana-toolkit/hostapd-mana.conf
nl80211: Could not configure driver mode
nl80211: deinit ifname=wlan0 disabled_11b_rates=0
nl80211 driver initialization failed.
wlan0: interface state UNINITIALIZED->DISABLED
wlan0: AP-DISABLED
hostapd_free_hapd_data: Interface wlan0 wasn’t started Hit enter to kill me
Regards,
Great Site ! Good explanations and so: it works after a few alterations for my system. So as a newcomer: what would be the next step on my now beloved ZSecurity to get more out of the data I collect ? I can see the websites I am using on my other device , but not exactly what’s going on or what I am looking for with google.
Which other lessons are there for going further ?
Thanks !
I can not access the wifi network from my windows machine :
in windows machine it says : “Information sent over this network might be visible to others”
Configuration file: hostapd.conf
Using interface wlan0mon with hwaddr 00:0d:b0:01:85:21 and ssid “we”
wlan0mon: interface state UNINITIALIZED->ENABLED
wlan0mon: AP-ENABLED
Ralink 802.11 n WLAN [0101]