Ninja Spy Framework
Ninja KeyLogger and Analysis Console
Synopsis: This KeyLogger was written as a passive penetration testing tool as a ‘plug and forget payload’. It is used essentially to spy on compromised machines as a part of Post Exploitation attacks. It can also be used with download-and-execute scripts to serve this KeyLogger as an initial attack vector. It logs all Keystrokes, Mouse Clicks and Current Window Names to encrypted log files which are then sent via email to the attacker. The attack would then decrypt these log files and put it through an analysis, which will analyse all Data Packets in the log file to separate them into different attacker specified tags. From there, the attacker can choose what tags he/she is most interested in and see what the victim has typed on that tag (e.g. Login or Whatsapp). Currently it only supports Windows systems , in the near future, there will be a port to Kali Linux where penetration testers can generate this KeyLogger with their desired options.
Contributor(s): Chong Jin Wei (2017)
Tools and Language Used: C++ (KeyLogger), C# (Analyser)
KeyLogger Specifications
Keystroke Logging: Allows the logging of all keys on the modern QWERTY keyboard including system keys such as control, alt, caps lock, shift, function keys, etc.
Mouse Click Logging: Logs ONLY the left mouse button currently, the right mouse button functionality will be adding in the near future with a screenshot functionality together with it. When the user clicks the mouse, it logs the mouse click, as well as the current focused window name (e.g. currently I’m focused on “Add New Post < Reverse That Shell Blog”). The window name will be logged in the log file along with the tags (e.g. Blog). If the logged window is not the same as the previous window, it is then classified as a “new” Data Packet, and strings will be written to the log file to close the current Data Packet and begin a new one with new tags. This is also how I measure user activity.
An example of a data packet (decrypted plain text):

Clipboard Logging: Logs user clipboard when they press the combination of CTRL + C, this is done as I noticed a lot of people copying passwords from a notepad / text file to the password field. This could also be used to see what the users are interested in as they might share links to their friends through the clipboard.
An example of a clipboard log:
Sends File Logs via Email: The tool sends an email when it starts up (when the machine starts up) and every 1 hour (can be changed) through email. It also shows the Host Name, Machine and User.
Analyser Specifications
Server Pinging: When I wrote this tool, I was going to do a penetration testing assignment on my client’s network, so it is important for me to always have port forwarding configured correctly. Unfortunately my wireless card would periodically drop the port-forward and require me to reconnect the wireless card. Sometimes I could go on 30mins-1hour without noticing the drop while researching on an exploit. This tool, allows me to ping my Server to ensure that my port-forwarding is OK. It also gives off an annoying sound when port forwarding is dropped. This tool pings the server every 30 seconds. Watch it in action:
Decryption: The Ninja LS Console tool decrypts logs received by mail and saves them in a folder. It can decrypt a selected folder and output all files to a sub directory.
Analyzing: The Ninja LS Console tool can analyze decrypted logs and ogranize them into tags and individual data packets for easy viewing / analyzing to find the most sensitive information.
Analyzing Filters: There are now very limited filters that you can play around with, e.g. Keystrokes > 5 (detects if there are keystrokes on the data packet), OR Click Count > 5 (to detect which tag/window the victim is more engaged with.
Analyzing Tags: Each Packet has a tag, and the analyzer will count all tags and show a total compiled output which shows the activity of the user, what he is doing most of his time. The attacker could click on a tag to see ALL packets corresponding to that tag, e.g. login or facebook.
Analyzing Packets: The Analyzer allows you to choose an individual packet that you think might be interesting.
The video shows a real attack scenario which I collected a day’s worth of logs and was analyzing them. Note: I do have signed permission to test this network and to censor the information while documenting it.
Web Framework :
*Disclaimer: All test devices and penetration test cases have been approved by participating parties. The key logger was removed after a month of data collection and the cessation of permission by participating parties. No law was broken in the usage/creation of this framework.
Contributor(s): Chong Jin Wei (2017)
Tools and Language Used: C++ (Ninja Keylogger), Angular JS (Framework), Django (Framework), Mongo DB, Cloudinary, Amazon Web Services.
Specifications:
Web Framework:
All data collected from compromised machines are transferred to a web server which inserts them into Mongo DB and the aggregate of which is displayed in the Web Framework:

Accepts Data from Compromised Machines through HTTP: The tool accepts data periodically from the Ninja Keylogger on a 24/7 webserver which provides real time updates to the Web Framework.
Parse Encrypted Data into Database Objects: The data received from the Ninja Keylogger is encrypted with SALTS and once received, it will be reversed to plain text. A series of process then begins to work on breaking the plain text file into smaller, bite size data to be sent to the database.

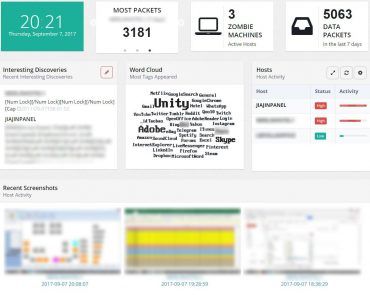
Filters Interesting Information (e.g. Passwords): The web server algorithm also parses data into interesting information based on certain words that appear in packets and displays them conveniently. e.g. In the case of getting a packet under any window that has the word “login” will be displayed here.
 Accessible Screenshots from Compromised Machines: The Ninja Keylogger was updated to include screenshot taking at times where the user activity is high (detected and assessed via mouse clicks). These screenshots are sent to the web server by converting them into text data and reversing it server-side to be inserted into Cloudinary image platform. It comes with a time stamp and the computer name which helps with identifying the machine that sent the screenshot. It also comes high resolution for enlargement.
Accessible Screenshots from Compromised Machines: The Ninja Keylogger was updated to include screenshot taking at times where the user activity is high (detected and assessed via mouse clicks). These screenshots are sent to the web server by converting them into text data and reversing it server-side to be inserted into Cloudinary image platform. It comes with a time stamp and the computer name which helps with identifying the machine that sent the screenshot. It also comes high resolution for enlargement.
Tags Word Clouds to Track Activity: Word clouds uses the tag counts that are collected by the web server to determine the size of the words which in turn would help the attacker understand the user activity to be used against more users in the network and for discovery of potential Social Engineering attack vectors. E.g. If the user likes to use Unity/Netflix, we can use that as a Social Engineering vector for more in-depth attacks.
Hosts Activity Tracking: The Web Framework also parses data into hosts activity, according to the number of packets sent in the last 7 days. This is done to see the most active machines / users.
Image: Sample image from Dashboard to track host activity for the past 7 days.
Future Planned Updates:
Individual Machine Logs: This is done to mimic the Ninja KeyLogger and Analysis Console, but on the Web which provides real time updates. With this, an attacker can click on any hosts, and analyze individual packets through search filter or tag filter.
Ability to Insert Backdoor via Keylogger: The Keylogger current works only as a Keylogger, however, in the future, I am planning to upgrade this Keylogger to be able to function as a Backdoor as well. A general idea for implementation is to have the Keylogger ping the server at fix intervals and if there is a change in the “configuration” (set on the Web Framework), it will initiate a reverse connection to a predefined IP.
Ability to Issue Instruction to Keylogger: This is done by creating a set of variables that the Keylogger can act on, e.g. Screenshot Intervals, or Screenshot Activity Threshold. Or even commands such as, Shutdown Computer, Change Desktop Image, Lock Computer. These options can be configured remotely, and with a push of a button on the Web Framework, the Keylogger will go to work and trigger these commands on the target machine (this is also done by allowing the Keylogger to constantly ping the server)
Resources and Source Code:
*Disclaimer: As with all tools created by myself, I am sharing the code for the framework, however keep in mind that the code was done in a short period of time and there was no cleaning up involved. Also, this tool is meant for educational/penetration testing in a legal capacity only. I am not responsible for any misuse of this tool.
Source Code (NinjaLS Keylogger): [Source Code]
Source Code (Decrypt NinjaLS): [Source Code]
Source Code (without credentials): [Source Code]
*** Let me know if any readers out there have better and more interesting ideas! ?
*Disclaimer: This tool is/was not maliciously used, it should and will only be used on networks that I own or have permission to conduct penetration tests.
Leave A Reply
You must be logged in to post a comment.











1 Comment
Awesome!