Intro to Computer Forensic for beginners
In the past, robbers use to rob a bank through physical penetration into the building and get away with money. This would lead to involvement of law enforcement agencies bringing the team of forensic experts to find clues and connect the dots at the sight of the incident. Living in the world of the Internet of everything, these old school robbers have now transformed to the rank of cybercriminals. Cybercriminals carry out different criminal acts such as data breach, identity theft, Denial of Service attack, ransom and phishing attack, all of this is done using digital devices, this lead to the evolution of forensic to digital forensics.
Cybercrime is growing exponentially, according to the latest statistics of data breaches and many other incidents, adding new dimensions to incidents. There comes the role of a digital forensics expert — to investigate digital devices related to crimes. This article will provide you with a basic understanding on forensic analysis and give you a practical glimpse of a typical day in the life of a forensics expert.
Playing a Digital detective involves gathering information from a device related to a crime. This is the first step in forensic analysis. It could be a compromised system, laptop or server related to the crime scene. To know the current state, the volatile data of the suspect system is the first thing to collect from. The information stored in RAM is very useful in the forensic investigation, and it is, in fact, the first most desired acquisition to be made. There are many tools available to forensic analysts to capture the current state of machinery. We would proceed with FTK Imager in this tutorial.
FTK Imager
A very handy tool that is often used to get a snapshots of a system that is subject to forensic analysis. FTK is an open source tool that is available in Lite and full version. It is often a good practice by the forensic analyst to access the suspect machine with Lite version stored in a USB drive and then uses it to acquire the system bitstream copy that gathers all the data bit by bit from a hard disk.
Demo
From the site below, you can get the download file. Proceed with the installation if you want to install it on your system. Make sure you download it on a virtual machine isolated as a suspect machine.
To generate some data in memory, you can start doing different tasks on the VM such as creating word file, searching on google for something, or alternatively search for some credit card info to pretend a malicious computer holding some sensitive data.
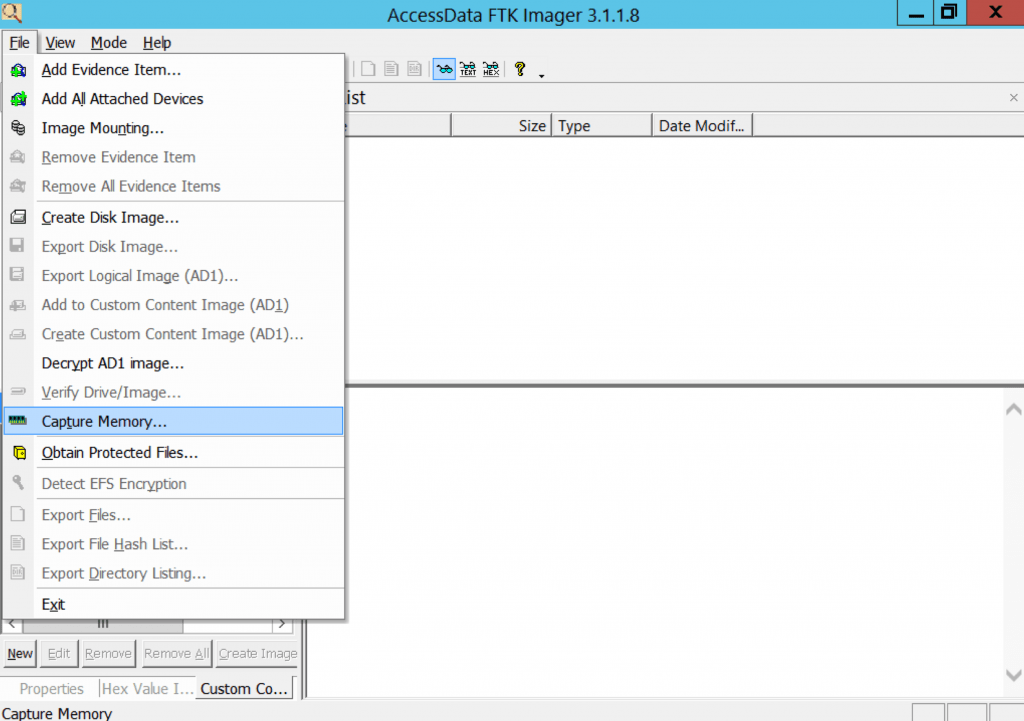
Now start FTK images and capture the memory as shown below:
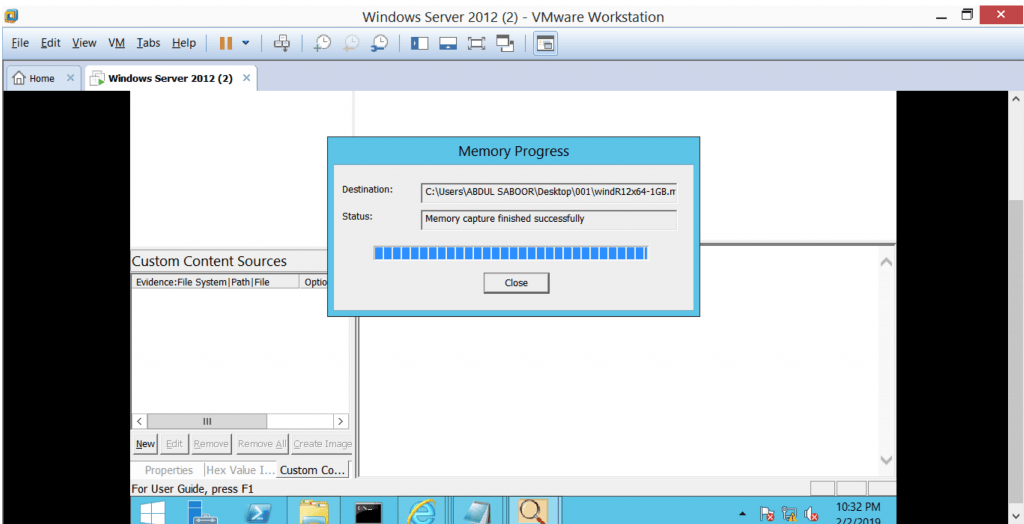
You will get a .mem file as your suspect image snapshot. Assign a suitable name to it and then open the image. By going through the memory, you can search for various items present in the memory. It would have those secret data which you recently loaded into your memory, as described in figure below.
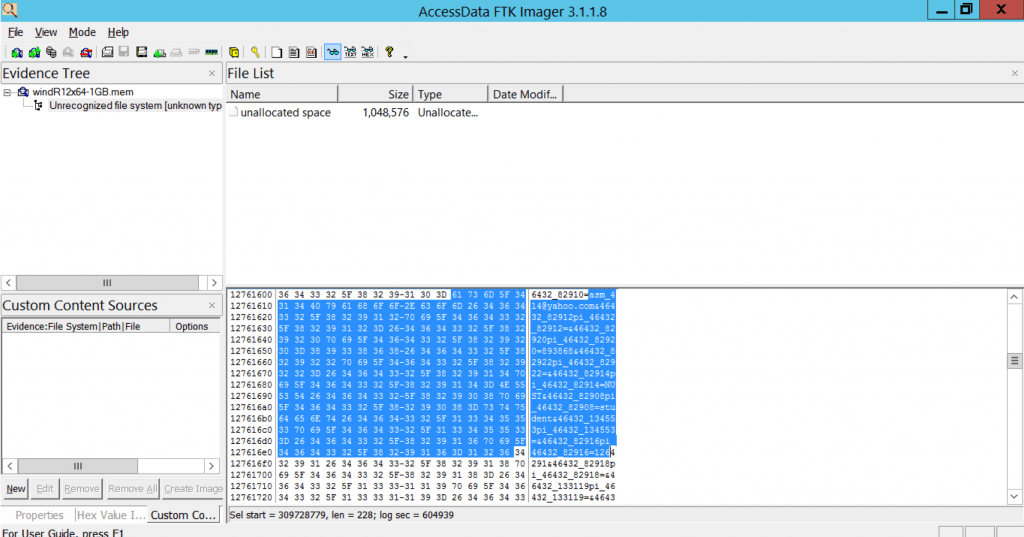
Well done. Now you have learned to create a forensic image of RAM, which is crucial forensic task.
Resources:
FTK Imger: https://marketing.accessdata.com/ftk-imager-3.4.3-download
Leave A Reply
You must be logged in to post a comment.





4 Comments
I need this real bad. I wish I’d known about this website sooner. I have been hacked by my exboyfriend for 3years now. Although the activity has slowed down now, or so I think, I can tell that he still hacks me. I have many, many devices that he’s shut down. iPhones, iPads, droids, 2 laptops. He’s relentless. Not only am I interested in taking courses, but I absolutely need the help to rid my devices and my future of this monster.
Its a good step to get aware of your digital identity.
Thats the only way to maximize our security in cyberspace.
While cybercrime helplines are also helpful.
Your next step will have to be using Autopsy to investigate the image further.
https://www.sleuthkit.org/autopsy/
works on linux and windows, is built into Kali
I find the Windows GUI easier to work with for large images
Great article Malik, thanks for sharing.