Initial Access Through File Upload Vulnerabilities
We all know the concept of shared hosting (if you don’t know you can read it here) , in this case gaining access to one website could allow us to take control of the complete server and then reach other websites hosted on this server. This clearly means that getting access to the server is even more harmful than getting access to the database of one particular website. But how do we get into a server?
Ways to attack/infect a web server:
1. Uploading a malicious program/script on the server.
2. Injecting commands in the web application software.
3. Cracking the password of remote control services like FTP Telnet SSH RDP etc.
4. Exploding a software running on the server which has a known vulnerability.
5. Finding and exploiting an existing backdoor.
In this article we will look at the 1st method.
DISCLAIMER:
Please note that uploading a shell to any website without valid consent/permission is considered as a crime. It comes under mass cyber-attack as all the websites of that server can be affected if a hacker can access them. Please don’t try it on any servers you don’t have permission to test.
The article is only for educational purposes and the attack is launched on a website that I have permission to test.
Now let’s begin.
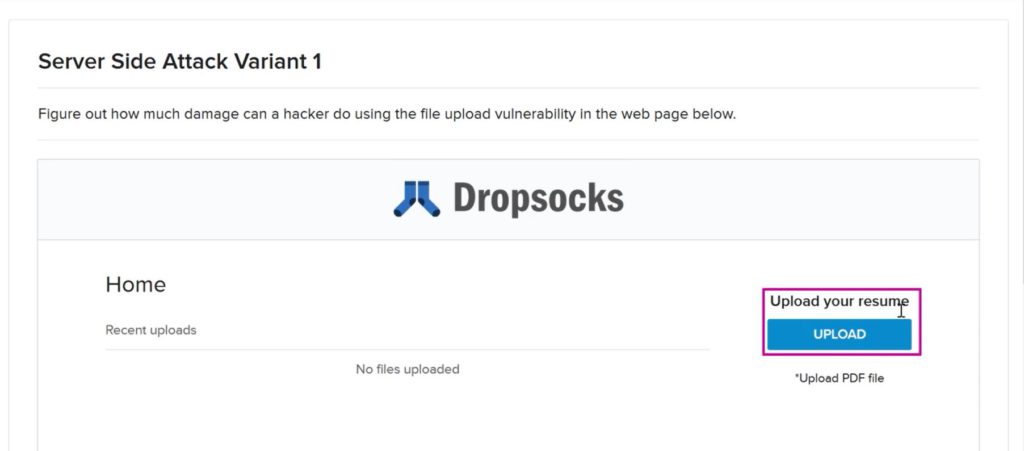
As you can see this website wants us to upload a resume which should be a pdf file.
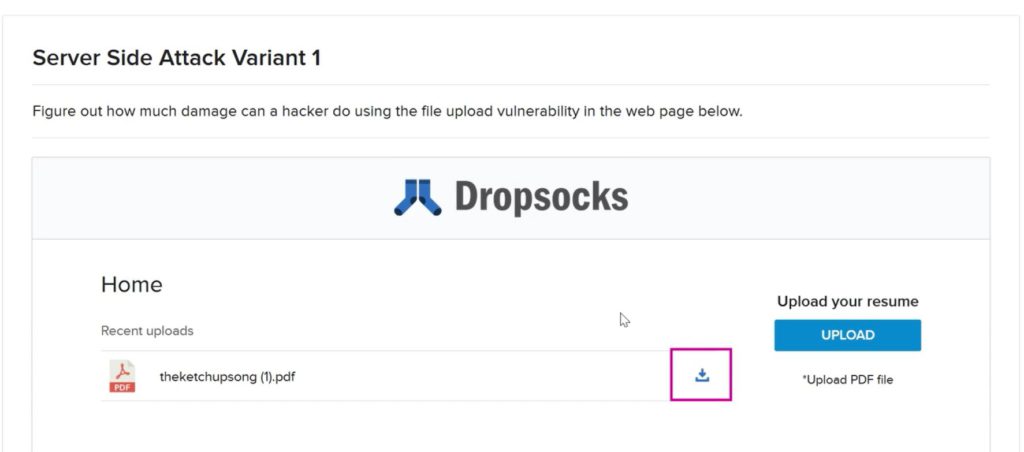
At first a sample PDF file is uploaded to see what happens. And we can see that as soon as a file is uploaded a download option appears against the uploaded file.
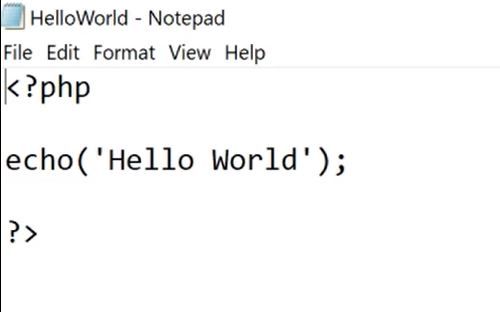
So now we can check if the website allows us to upload any other file extensions (like jpg, txt, PHP). We all know PHP is a server-side language that can be used to run commands on the server.
So a simple Hello World program in PHP is written in any text editor and is uploaded to the website.
And we can see the file is uploaded successfully.
So the first flaw is that despite asking for PDF file the application lets us upload files in other formats.
Here is the download option appears and we know a PHP file always be executed and not download.
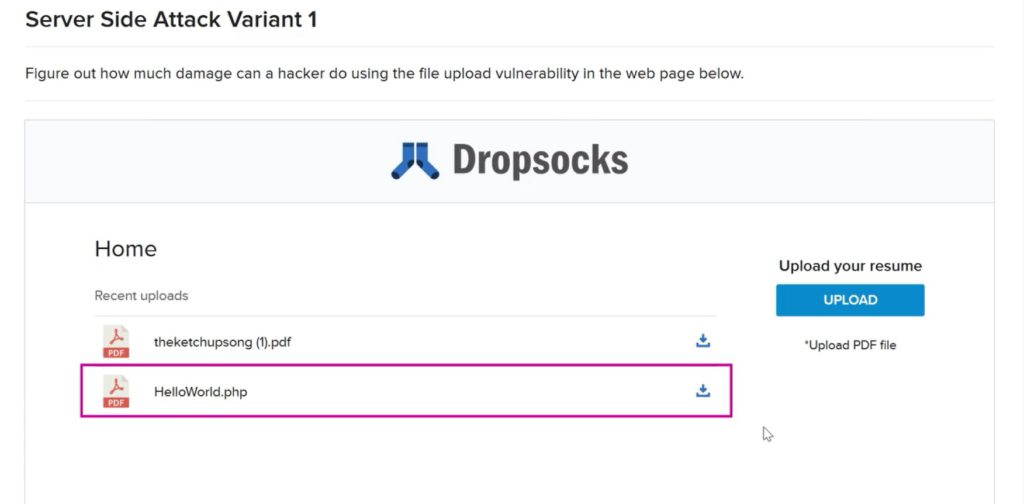
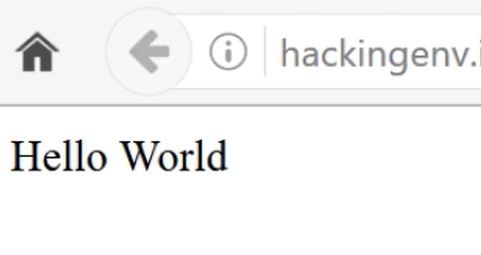
So when we click the download option the code gets executed and prints the output. This means we can upload any kind of PHP file and make the server to do other things right? And it’s definitely aFile Upload vulnerability.
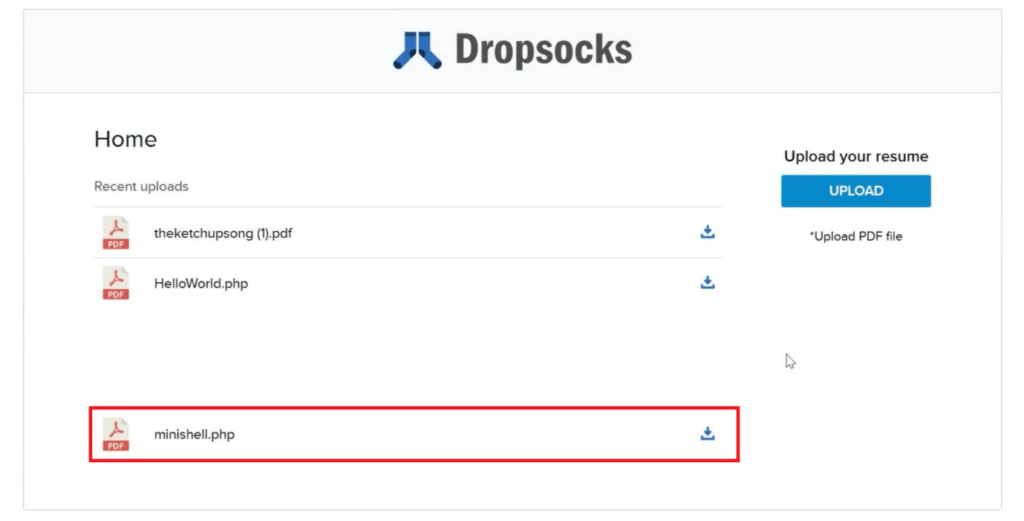
Now let’s see how we can play with this and get full access to the server. At first, we need to download a PHP Web Shell. There are many web shells available on the internet. Here we will use the B374k mini shell.
Visit the link to download B374k mini shell here.
After opening the link in the browser we need to right-click on the web page and Save Page As minishell.php in our computer. Then we need to upload the shell on the website.
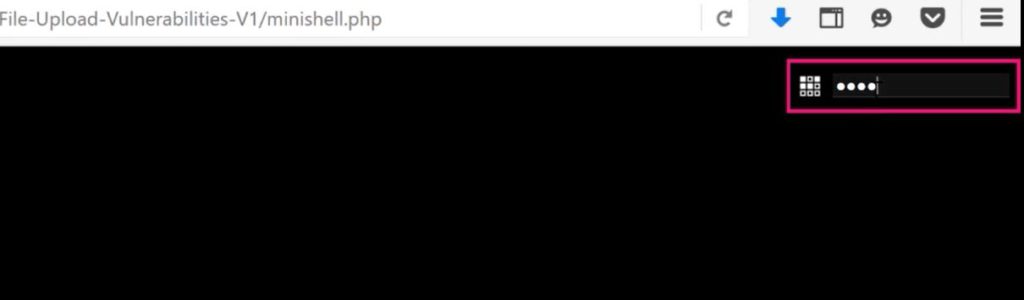
After successfully uploading when we run it i.e. click on the download link a password pop-up window will appear at the top right corner. The password is “root”.
A file browser will open through which we can access any file on the server!
You may also have some restrictions depending on the file and directory permissions. Though you can hunt and explore what you can do with this shell.
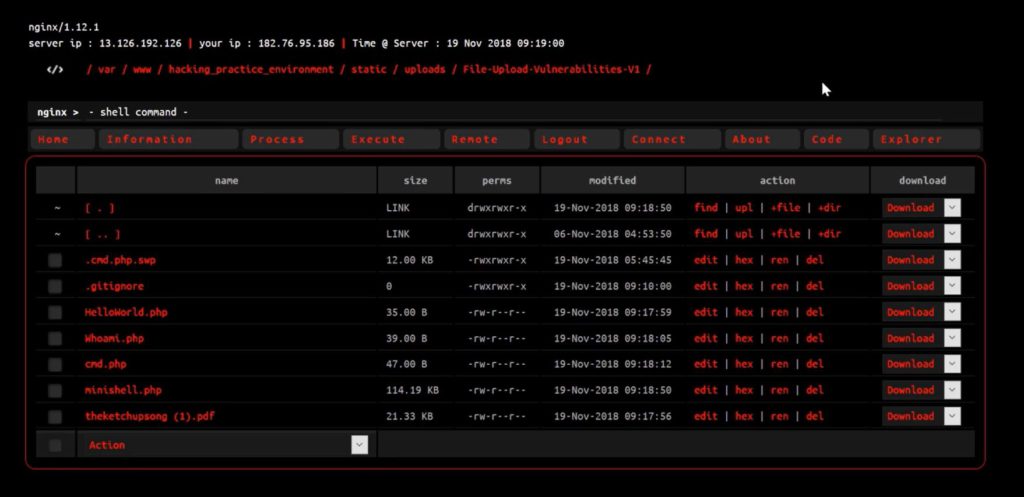
Here is some interesting things can be done –
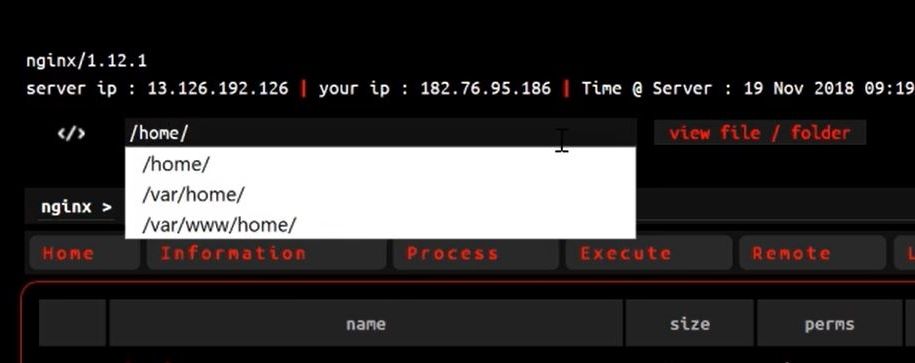
1. You can access critical information of all the server administrator by navigating the “home” folder like this –
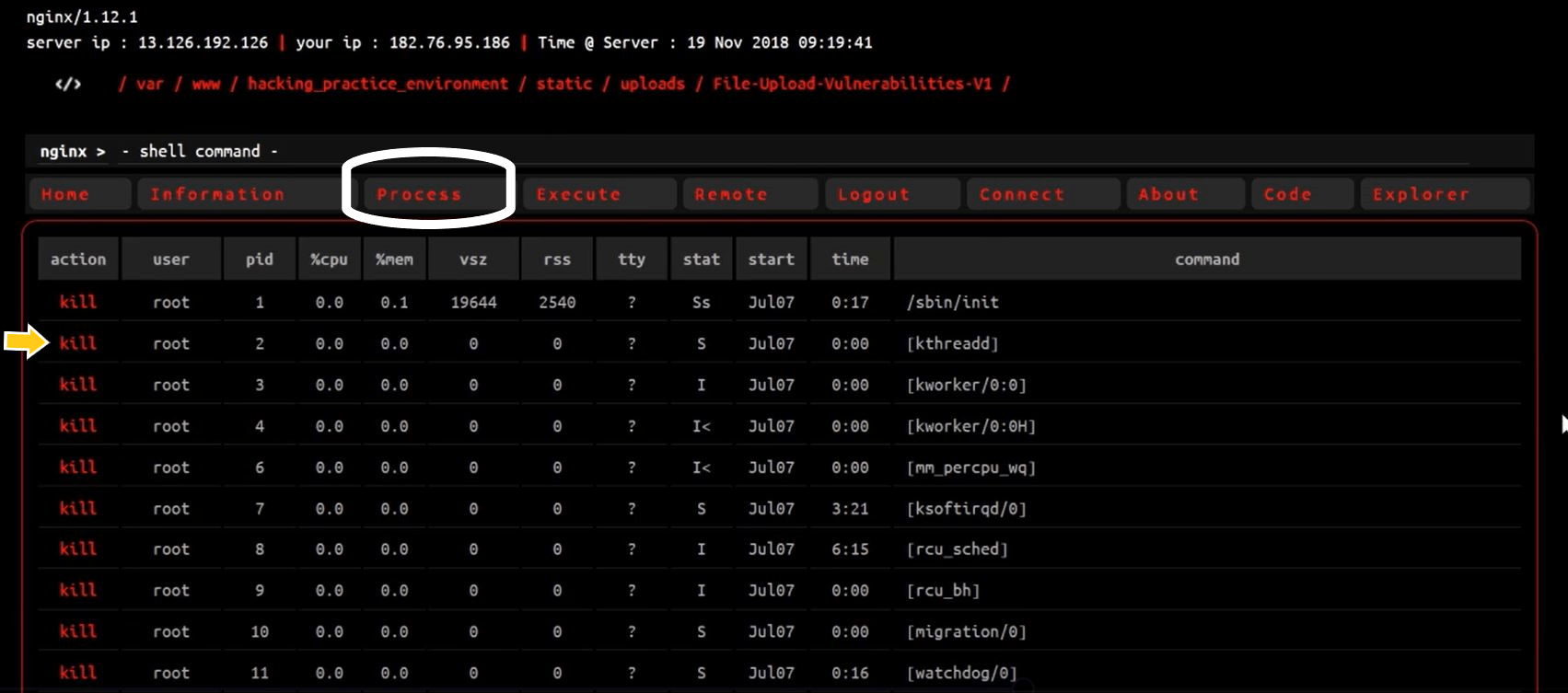
2. You can see all the running processes of the server under the “process” tab and can kill them also.
3. You can run Linux command in “ – shell command – “ section.
4. You can search for config.php file in the shell as it may contain the database name and password.
Hope you can see how a simple file upload vulnerability can give a hacker complete access to the database without an SQL injection vulnerability.
NOTE:
In real life, finding file upload vulnerabilities are not that easy, most of the time you have to play with requests using Burp Suite. Here I took a very simple example as the purpose of the article is not to teach finding arbitrary file upload vulnerability but to make you aware of how much harm a hacker can perform after finding it. Checkout the website hacking course on the courses section for detailed info on finding these type of vulnerabilities and much more.