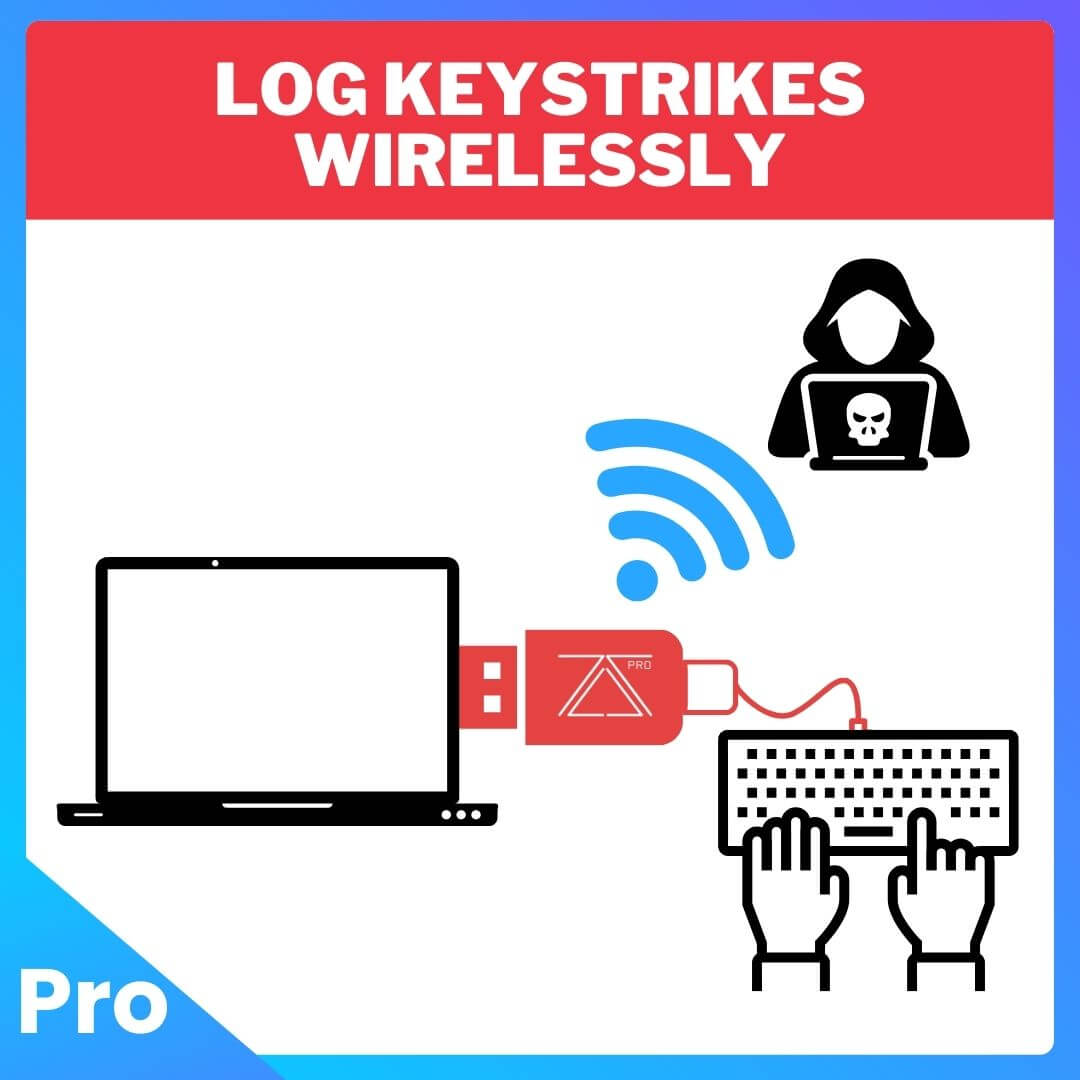
Hardware Keylogger
HID BadUSB Keystroke Injector
Ready Payloads
Wi-Fi Interface
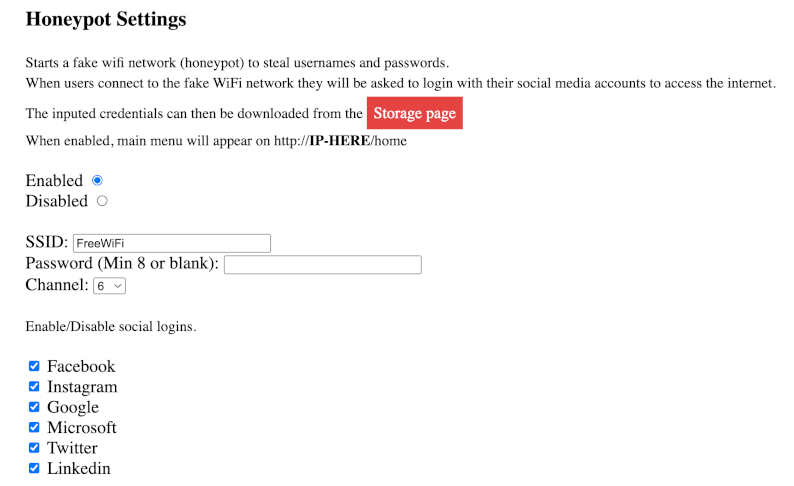
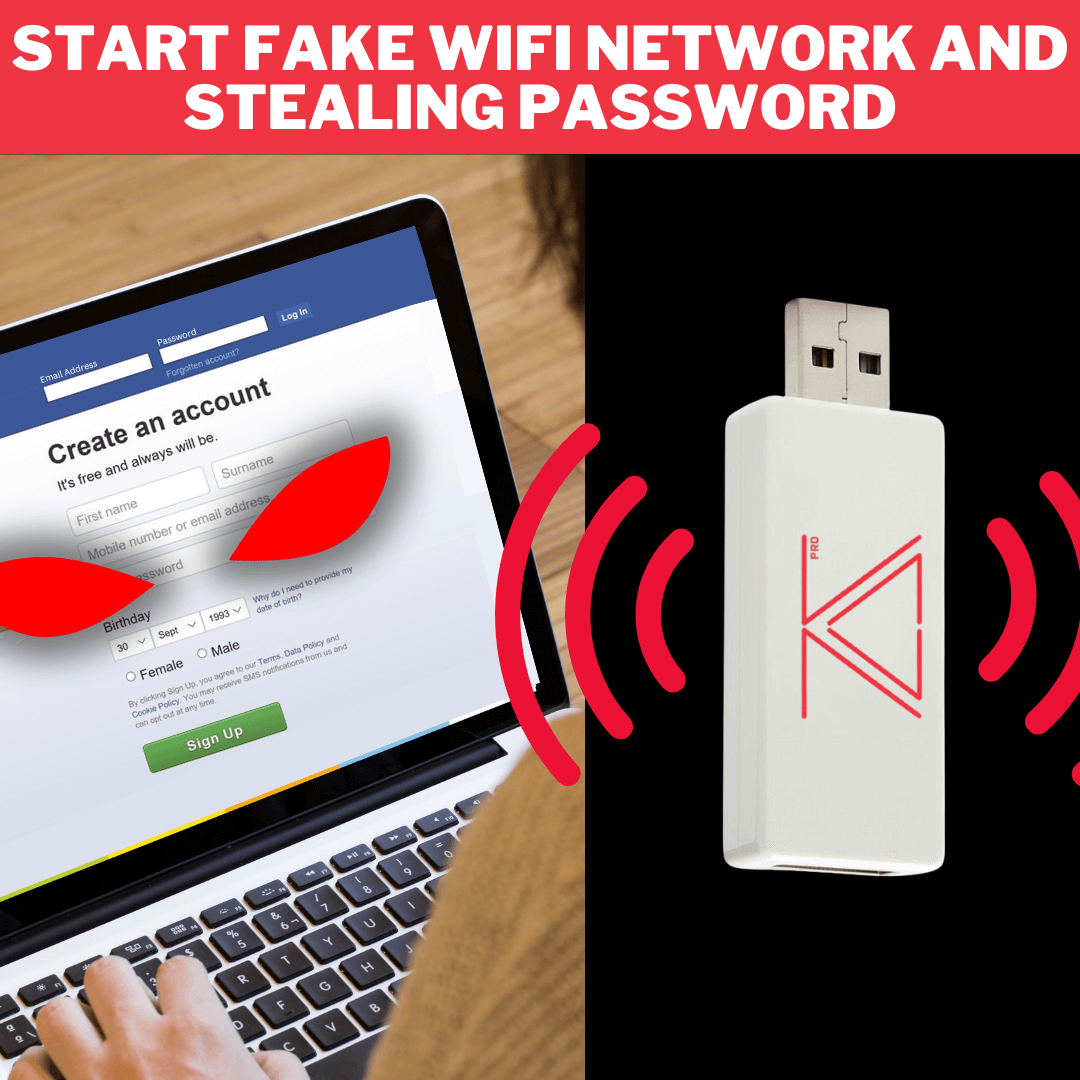
Wi-Fi Honeypot
Cross-Platform Compatibility
ZS CactusPRO BadUSB-C Keystroke Injection Cable
The ZS Cactus PRO is a professional-grade USB device that combines keystroke injection capabilities, hardware keylogging and Wi-Fi phishing with wireless control for comprehensive security assessments.




Compare ZS CactusPRO vs ZS Cactus
ZS Cactus PRO = ZS Cactus + Hardware Keylogger
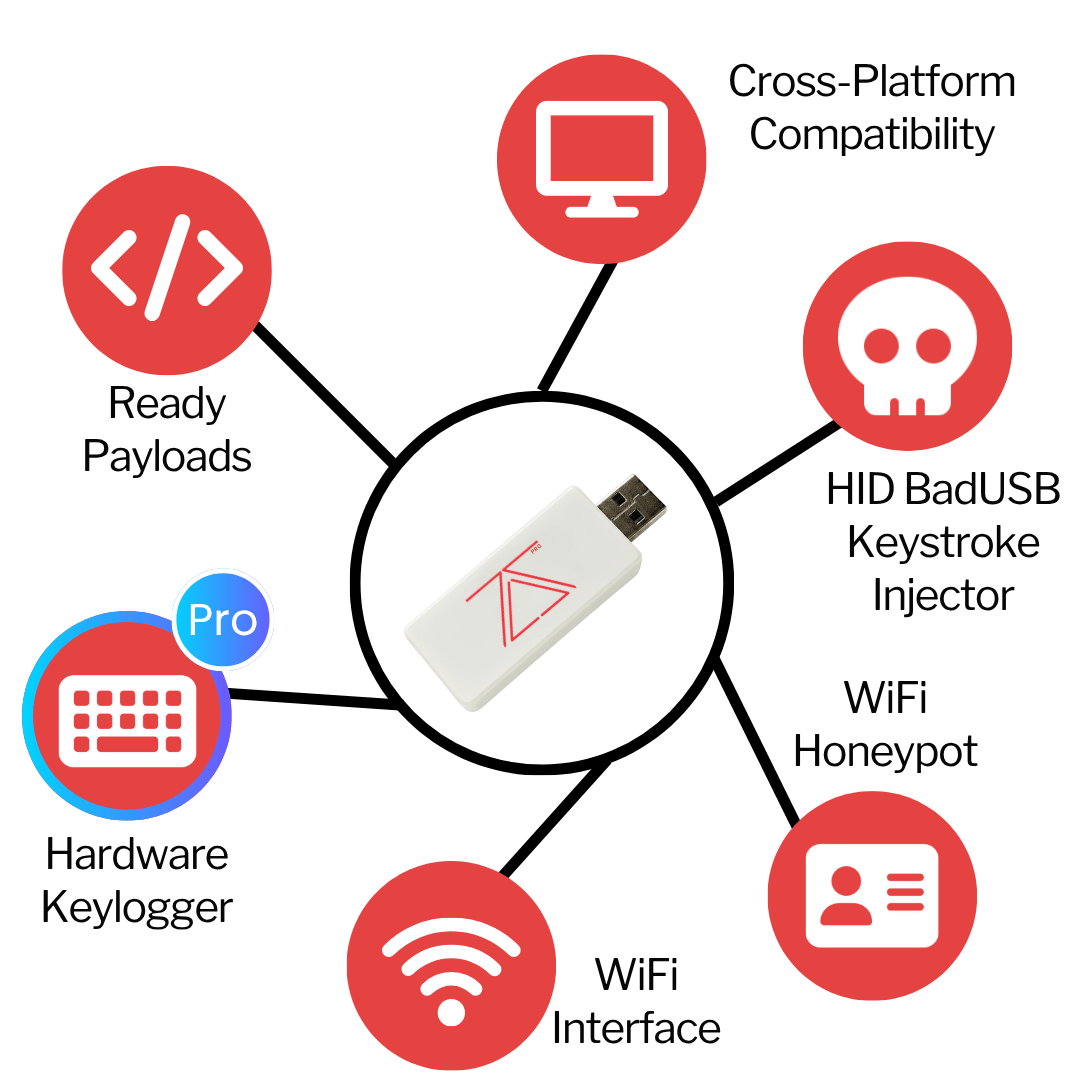
Key Features
- Hardware Keylogging: Spy on the target’s keyboard keystrokes and access it remotely from any device.
- HID Keystroke Injection: Emulates a keyboard and inject automated keystrokes via USB or Wi-Fi to hack the target, steal data from it or remotely control it.
- Ready Payloads: Get instant access, steal credentials, browser data and even Wi-Fi passwords with a few clicks.
- Wi-Fi Honeypot: Create a fake/rogue wireless network to steal login information from connected devices.
- Web Interface: Launch attacks, control and manage everything through a mobile-friendly web interface..
- Remote Mouse & Keyboard Control: Remotely controls cursor movement and keystroke input.
- Wireless Payload Execution: Delivers and triggers payloads over Wi-Fi connections for remote deployment.
- Direct Data Extraction: Retrieves or exfiltrates files and data via URL, FTP, or similar transfer protocols.
- Multi-Platform Compatibility: Works with Windows, Linux, and Apple Mac OS
Applications
- Hack computers using built-in or own payloads using BadUSB attacks.
- Spy on keyboards using the hardware keylogger and access keystrokes remotely.
- Steal login information of Facebook, Instagram, Linkedin and more using the Fake Wi-Fi Honeypot.
- Control everything remotely using a web-interface from any device with a web browser!


Honeypot Mode
This mode can be used to steal login credentials. It creates a fake WiFi network that asks clients to login using their social media account to access the internet. It can also be configured to serve custom HTML pages to hook the connected clients to BeEF or steal other data.
Connect to the fake access point, disregard the login prompt and navigate to http://192.168.1.1/home to access the command center. Navigate to “Storage” and you should have a file named “honeypot-log.txt”.
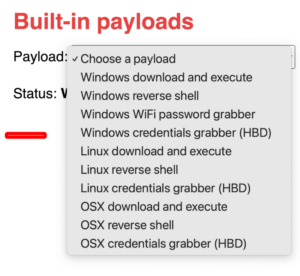
Built-in Payloads
ZS Cactus comes with 10 built-in payloads for Windows, Linux and OSX.
These payloads can be used to gain full control over the target system, steal browser data including saved passwords, steal stored Wi-Fi passwords and even download and execute any file you want!
Wi-Fi Control Center
ZS Cactus can be configured and controlled over Wi-Fi using a mobile-friendly web interface. Simply connect the device to a USB power supply and connect to it’s Wi-Fi network “ZSCactus“. The default password which can be changed from the settings is “zscactus“. Once connected open up a web browser and navigate to http://192.168.1.1/ to access the control center. The default credentials are “admin” / “zscactus”.
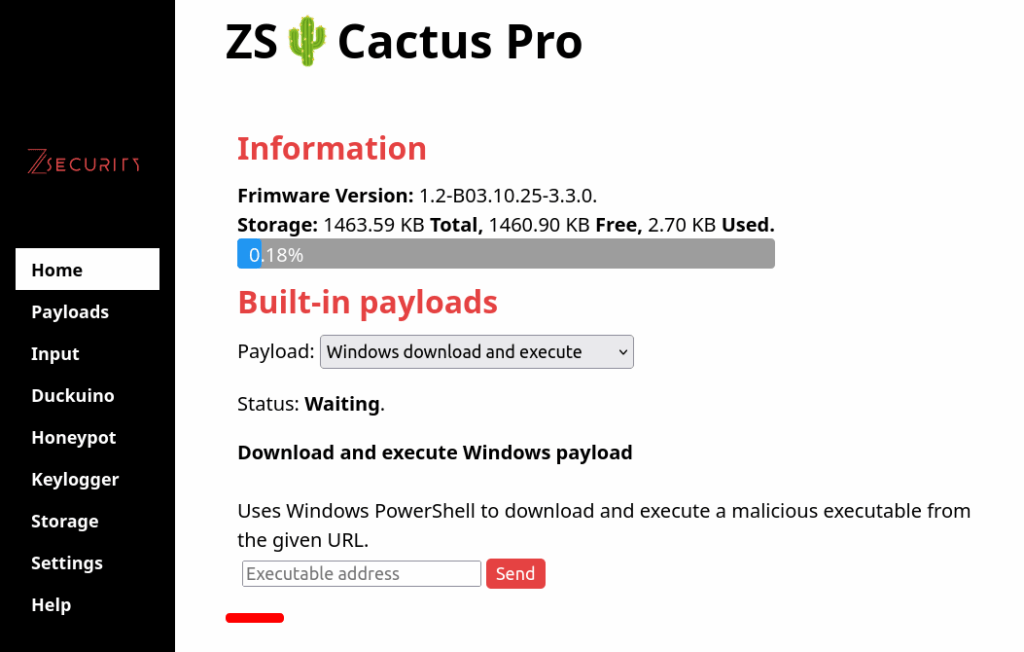
Payloads
This page allows you to manage your payloads, you can upload, run or delete custom payloads.
You can also set a payload to auto run when the device is connected to a computer.

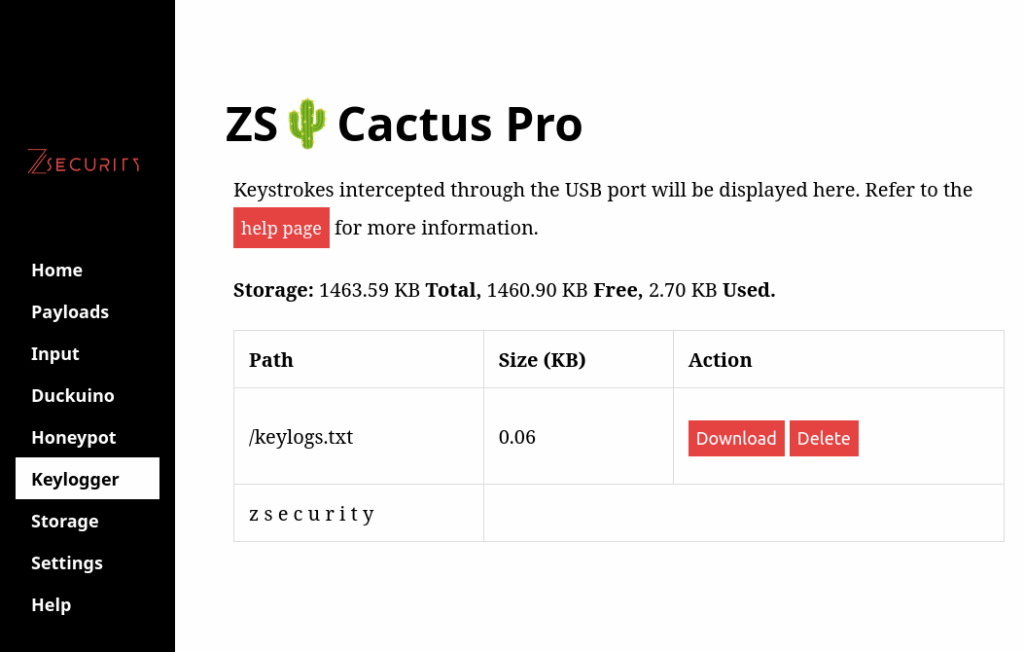
Keylogger
This mode can be used to capture all keys input by the user. With a keyboard connected to the USB port, keystrokes are saved before being sent to the Operating System.
To read the captured keystrokes, access the control center, navigate to “Keylogger” and you should have a file named “keylogs.txt”.
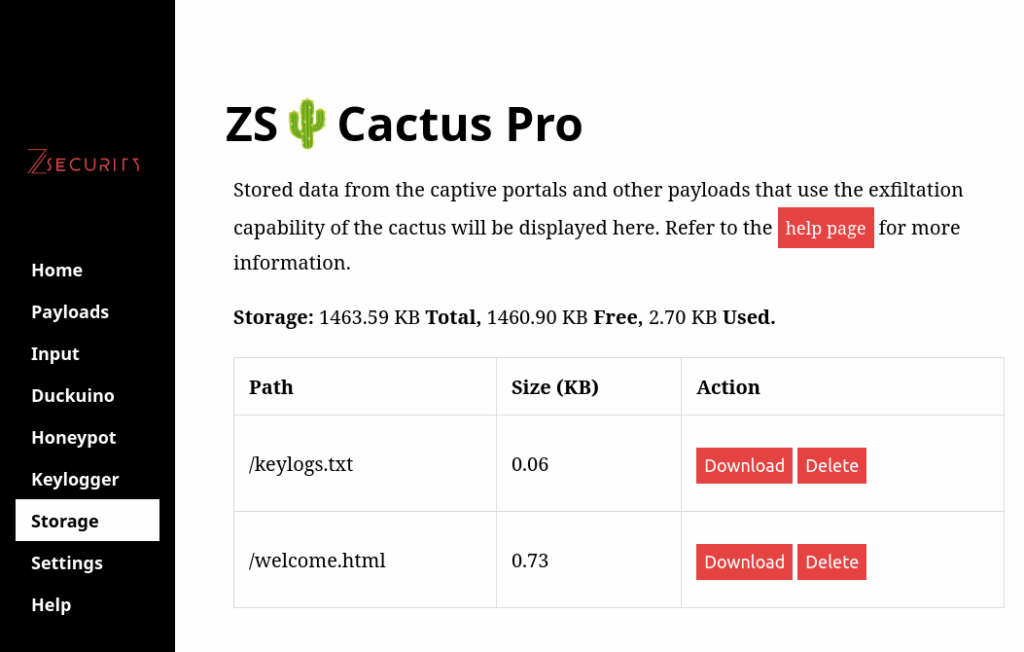
Storage
The built-in storage of the ZS Cactus allows you to store payloads, exfiltrate data, serve honeypot templates and more.
To view/download currently stored files, navigate to “Storage” in the control center.
Detailed Specification
| Spec | Detail |
|---|---|
| Brand | Alfa |
| Model | AWUS036ACH |
| Chipset | Realtek RTL8812AU |
| Wi-Fi standards | IEEE 802.11 a/b/g/n/ac |
| Data rates |
|
| Frequency range | 2.4 GHz & 5 GHz |
| Antennas | 2 × 6 dBi dual-band, RP-SMA detachable |
| OS support | Kali Linux (native or VM) |
| Security | WEP 64/128, 802.1X, WPA/WPA2 Personal & Enterprise, WPA-PSK, WPA2-PSK |
| Dimensions | L8.5cm x W6.3cm x H2.0cm |
Looking for something different?
 Alfa AWUS036ACH |  zSecurity RTL8812AU |  zSecurity AR9271 | |
|---|---|---|---|
| Chipset | Realtek RTL8812AU | Realtek RTL8812AU | Atheros AR9271 |
| Wi-Fi Standards | 802.11 a/b/g/n/ac | 802.11 a/b/g/n/ac | 802.11 b/g/n |
| Dual-band | ✅ | ✅ | ❌ |
| Max speed | up to 867 Mbps | up to 867 Mbps | up to 150 Mbps |
| Frequency Range | 2.4 & 5 GHz | 2.4 & 5 GHz | 2.4 GHz only |
| Interface | USB 3.0 | USB 3.0 | USB 2.0 Mini USB |
| Antennas | 2 × 5 dBi | 2 × 5 dBi | 1 × 5 dBi |
| Security Protocols | WEP, WPA/WPA2, WPA-PSK | WEP, WPA/WPA2, WPA-PSK | WEP, WPA/WPA2, WPA-PSK |
| OS Support | Kali Linux (VM & Native) | Kali Linux (VM & Native) | Kali Linux (VM & Native) |
| Monitor & injection | ✔ | ✔ | ✔ |
| Signal Sensitivity | Not specified | Not specified | 11b: -96dBm, 11g/n: -91dBm |
| Price (USD) | $69.99 | $34.99 | $24.99 |
Setting up your ZS Cactus PRO
BadUSB Silent Intrusion Kit PRO
Save $10 with this bundle
►+ Free 1 Month zSecurity Trial VIP membership.
$129.99
BadUSB Silent Intrusion Kit PRO+
Save $10 with this bundle
►+ Free 1 Month zSecurity Trial VIP membership.
$139.99
PRO Hacker Kit
Save $15 with this bundle
►+ Free 1 Month zSecurity Trial VIP membership.
$169.99
Frequently Asked Questions
What makes the ZS Cactus PRO different from the ZSCactus?
The PRO ZSCactus has been upgraded to include Key logging capabilities which will capture every single button / keystrike from the target computer
What is the ZS Cactus PRO Wi-Fi Keystroke Injection BadUSB used for?
It’s designed for ethical hackers and cybersecurity professionals to simulate USB-based attacks, test endpoint and physical security, practice social engineering scenarios, train user awareness, and assess incident response.
Can antivirus software detect and block ZS Cactus PRO WiFi Keystroke Injection BadUSB attacks?
BadUSB attacks operate at the firmware level, which is much harder for standard antivirus software to detect, as the device appears to the operating system as a legitimate keyboard.
How does the ZS Cactus PRO WiFi Keystroke Injection BadUSB attacks differ from traditional USB malware?
Traditional malware relies on infected files. BadUSB exploits device firmware to act as trusted hardware (like a keyboard), allowing it to execute commands silently at the system level. This makes it stealthier and more difficult to defend against.





















Reviews
There are no reviews yet.