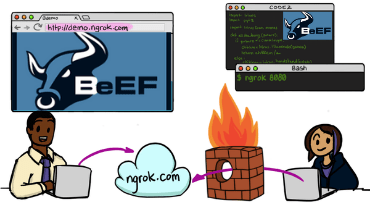
Use BeEF Over The Internet With Ngrok!
BeEF is an amazing Browser Exploitation Framework that can be used to run so many cool attacks.
In the following video I’ll show you how to configure Ngrok properly to expose BeEF to the internet so you can target and run commands on devices outside your network.
https://www.youtube.com/watch?v=LOXfpExInDs&feature=youtu.be
Resources:
Leave A Reply
You must be logged in to post a comment.




31 Comments
Hi Sathvik, it’s informative. I just want to know why we should use both ngrok and BeEF over wan this attack? Only BeEF over wan can’t do this?
Hello!
The application is built in such a way that it needs to integrate with ngrok!
Once check the documentation of beef-over-wan
yes u can use beef without ngrok but u can only use it on lan , but when u use it on wan u have to use ngrok.
i get this error when i visit my pannel every thing i did perfectly.
The connection to http://1b6035fa.ngrok.io was successfully tunneled to your ngrok client, but the client failed to establish a connection to the local address localhost:3000.
Make sure that a web service is running on localhost:3000 and that it is a valid address.
The error encountered was: dial tcp [::1]:3000: connect: connection refused
go to beef –xss folder which is in etc folder and change the username and password and restart beef using service beef –xss restart
when i send the link to victim a really suspicious page loads which clearly states u r hooked to beef as in the video….i wish to inject the url to some webpage so that something interesting like a blog or website loads but i dont know which url to inject next to head tag of html file
so should i paste the link that we r supposed to send to victim http://f67230f8.ngrok.io/beef.html(the link i got to send to victim)
or should it be the example url that loads in terminal but with the global ip
Its simple navigate to the beef.html
File and now replace the code with any other html code of your choice
U can find the source code of any website by right click and then source
Feel free to ask any other questions 😉
Its simple navigate to the beef.html
File and now replace the code with any other html code of your choice
U can find the source code of any website by right click and then source
Also u can shorten the link from bit.ly
Which makes our attack non suspicious
Feel free to ask any other questions 😉
Hello,
I tried things in a simple way: I generated the two links in the same way than on your video. Then I open BeEF with the link provided by BeEF on WAN, which was fine. And then I sent the victim link to another computer which has Windows 10. the other computer is in another country by the way. So when I asked the person to click on the link, he got a blank page and at the same time I check on BeEF page and nothing happened, no connection from the victim’s computer.
Any suggestion to make it sorted ?
Thank you
Best
In case this would help, I don’t have a WIFI adapter, only the integrated wifi card in my laptop. I can’t do port forwarding right now.
hey Sathvik I tried using this tool for a second time (everything worked perfectly first time) but i got an error in browser when i searched url given by beef to access the control panel
the error is:
NOT FOUND
the requested url was not found on this server
apache/2.4.41 debian server at 0d3bc8f6.ngrok.io to port 80
can u pls help me with this??
thank u for ur answer to my previous query
I created another account with ngrok and went through the whole process …everything worked perfectly then i closed all tabs and then started everything again and got the same error
The thing i have noticed is that i am able to use the attack only once with a account ….also I noticed an error in better the process “someone is already using port 3000” i got this when I typed pressed enter after typing 0
I noticed this last time as well when i using my previous account
Kill the process that’s using port 3000
Use netstat command then view the process
hii sathvik bro in your video when you are opening beefoverwan you got automatically opening the webpage in the browser but for me it is directly showing the results like this
All Good So far …
Close The Browser If Prompted ..
____ ______ ____ __ __ _ _
| _ \ | ____| / __ \ \ \ / /\ | \ | |
| |_) | ___ ___| |__ | | | |_ _____ _ __ \ \ /\ / / \ | \| |
| _ < / _ \/ _ \ __| | | | \ \ / / _ \ '__| \ \/ \/ / /\ \ | . ` |
| |_) | __/ __/ | | |__| |\ V / __/ | \ /\ / ____ \| |\ |
|____/ \___|\___|_| \____/ \_/ \___|_| \/ \/_/ \_\_| \_|
BY SKS
https://github.com/stormshadow07
[?] Enter Adress of Link [You are Sending to Victim]: 00655a9c.ngrok.io
[+] Send_To Link : 00655a9c.ngrok.io
[?] Enter Adress of Link [Your Link will be Connecting to..]: 1f8846d1.ngrok.io
[+] Connect_To Link : 1f8846d1.ngrok.io
[✔] Checking directories…
Clean Succesful
[✔] File Changed…
[✔] File Changed…
[✔] File Changed…
==================================== RESULT ====================================
[+] Access The BeeF Control Panel Using : http://1f8846d1.ngrok.io/ui/panel
Username = beef
Password = beef
[+] Hooked Link To Send to Victim : http://00655a9c.ngrok.io/beef.html
[?]
Note : I know few of the Exploits does not work
due to Updated Browsers and stuff…
Tip : Change Payload or Images Address to your Connect_to Address with Port 80
Example :
FROM Image URL : http://0.0.0.0:3000/adobe/flash_update.png
TO Image URL : http://1f8846d1.ngrok.io:80/adobe/flash_update.png
Happy Hacking !!!
Have Problem or Tip ? Contact : https://github.com/stormshadow07
root@kiruthik:~/BeeF-Over-Wan#
iam not getting any url to open so now what can i do for this bro
Click on the link
[+] Access The BeeF Control Panel Using : http://1f8846d1.ngrok.io/ui/panel
Username = beef
Password = beef
bro when i open that link it shows that:
Failed to complete tunnel connection
The connection to http://b2d857e6.ngrok.io was successfully tunneled to your ngrok client, but the client failed to establish a connection to the local address localhost:3000.
Make sure that a web service is running on localhost:3000 and that it is a valid address.
The error encountered was: dial tcp [::1]:3000: connect: connection refused
Having this issue while trying to log in to ui/panel page
Failed to complete tunnel connection
The connection to http://5401c4bc.ngrok.io was successfully tunneled to your ngrok client, but the client failed to establish a connection to the local address localhost:3000.
Make sure that a web service is running on localhost:3000 and that it is a valid address.
The error encountered was: dial tcp [::1]:3000: connect: connection refused
Great tutorial! only issue is that since beEF updated to not allowing beef as the username the beef and beef login doesn’t work. Do you have a fix for changing the username on beef-over-wan?
root@kali:~/Downloads/BeeF-Over-Wan# python BeeFOverWan.py
Traceback (most recent call last):
File “BeeFOverWan.py”, line 8, in
from termcolor import colored
ImportError: No module named termcolor
I got this error. What I should do???
Try “sudo apt-get upgrade” before using “BeeFOverWan.py”
its not working broo
open terminal and type … pip install termcolor…100 percent work
pip install termcolor
When i run ./ngrok start –all, i am getting below error :
raceback (most recent call last):
File “BeeFOverWan.py”, line 8, in
from termcolor import colored
ImportError: No module named termcolor
Hi Sathvik,
When using command “chmod +x BeeFOverWan.py && python3 BeeFOverWan.py”
Showing result :
File “BeeFOverWan.py” line 90
Print ‘“{old_string}” not found in {filename}.’.format(**locals())
SyntaxError: invalid syntax
Hi sathwik,
Login BeEF showing invalid username or password.
I tried username as “beef“ and pass as “beef”
Also username as “beef” pass as “admin “
Hi !!
After i run python Beef-Over-Wan.py it is showing me some error, “no termcolor termcolor error” & “/usr/bin/python : line1 : $’\177ELF\022\011\011′: command not found
python BeeFOverWan.py shows below error :
Traceback (most recent call last):
File “BeeFOverWan.py”, line 8, in
from termcolor import colored
ImportError: No module named termcolor
While running sudo pip3 install termcolor, it shows
Requirement already satisfied: termcolor in /usr/lib/python3/dist-packages (1.1.0)
Let me know how to proceed further?
hi……when i was trying to do this i’m getting errors…….in the module BeeFOverWan.py……it was showing me that was an error in line 8……can u help me plzzz
wats the usename and password
all in one solution…..
for termcolor error type this command on terminal…
pip install termcolor
and for tunnel error go to beef -xss folder and change the username and password