How to Spoof SMS Messages
What is SMS Spoofing?
Can These Attacks be Detected?
How to Register With Twilio?
How to Interact With The API?
pip install twilio
#!/usr/bin/env python from twilio.rest import Client account_sid = 'TWILIO_ACCOUNT_SID' auth_token = 'TWILIO_AUTH_TOKEN' client = Client(account_sid, auth_token) message = client.messages.create(body='Message', from_='+15017122661', to='+15558675310') print(message.sid)

python sms_spoof.py
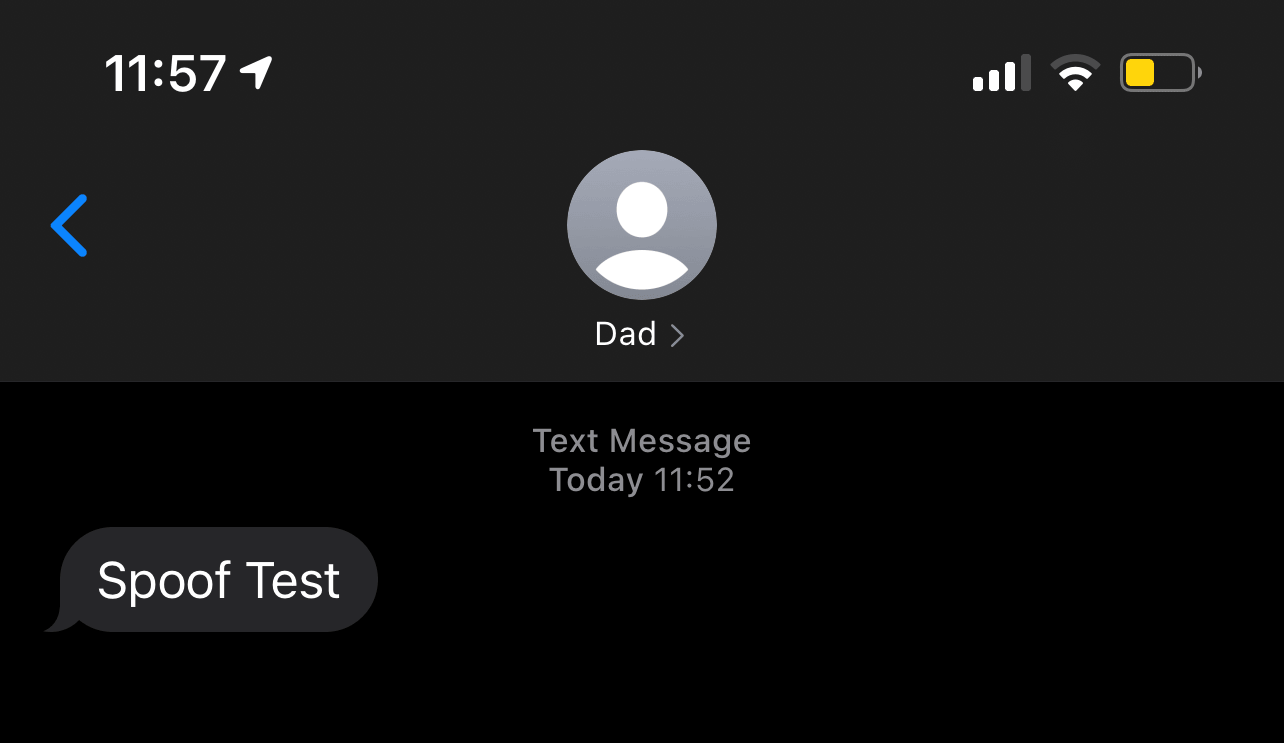
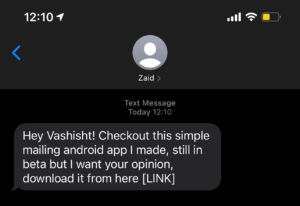
Thanks for Reading 🙂
Resources:
Leave A Reply
You must be logged in to post a comment.




11 Comments
Hi,
On free account Twilio said:
Unable to create record: The From phone number DAD is not a valid, SMS-capable inbound phone number or short code for your account.
More information may be available here:
https://www.twilio.com/docs/errors/21606
Did you buy a number from twilio? If you are using a free account, you will have the use the number itself to send sms from.
i did upgrade the account, i ran the script using the actual twilio number and i received the sms perfectly, when i tried to spoof i got this message::
Unable to create record: The From phone number +1(number) is not a valid, SMS-capable inbound phone number or short code for your account.
More information may be available here:
https://www.twilio.com/docs/errors/21606
any clue?
Does it work with alphanumeric sender id?
It seems like you can only buy random numbers. You can’t, for instance, buy your dad’s number to make the SMS look like it’s actually coming from him. Or am I missing something?
Yes that’s right. Like I said, you should use the script above to specify/change your sender’s ID.
First of all , we need to put our number to get code verify it right sir ?
That’s the limitation while using the trial balance from twilio.
Is there any way you can make a tutorial video or give a link to contact you on the tutorial … Sms spoofing is a handy social engineering tools and I’ve spent alot on Zeid courses…. Please make this tutorial more understanding
I think this article should be enough, you should get into the habit of researching and experimenting if you want to be a good hacker.
If you have any questions, you can send me an email at [email protected] 🙂