Intercepting HTTPS Requests With Burp Proxy
We all know how burp proxy can be very useful to intercept and modify requests sent from applications to a server or to an API, this of-course is very useful to help understand how a specific application works, how it communicates with its server, and helps test the security of this application to discover vulnerabilities and even exploit them if there are any.
Setting up burp proxy is pretty easy, all you have to do is start it, turn on the proxy, and set your web browser/application to use burp proxy as a proxy server, then all requests sent from that browser will have to go through burp proxy where we can analyse and modify them if we wanted to.
The only challenge you might face is if the target website/application uses HTTPS, in this case you will have to install Burp’s CA certificate in your browser, some people find this a bit tricky so I decided to write this article to help 🙂
Step 1 – Download Burp’s CA certificate, to do this first run burp, open up your web browser, and go to https://burp , you’ll see a link on the top right of the page called “CA Certificate” , click this link to download the certificate.
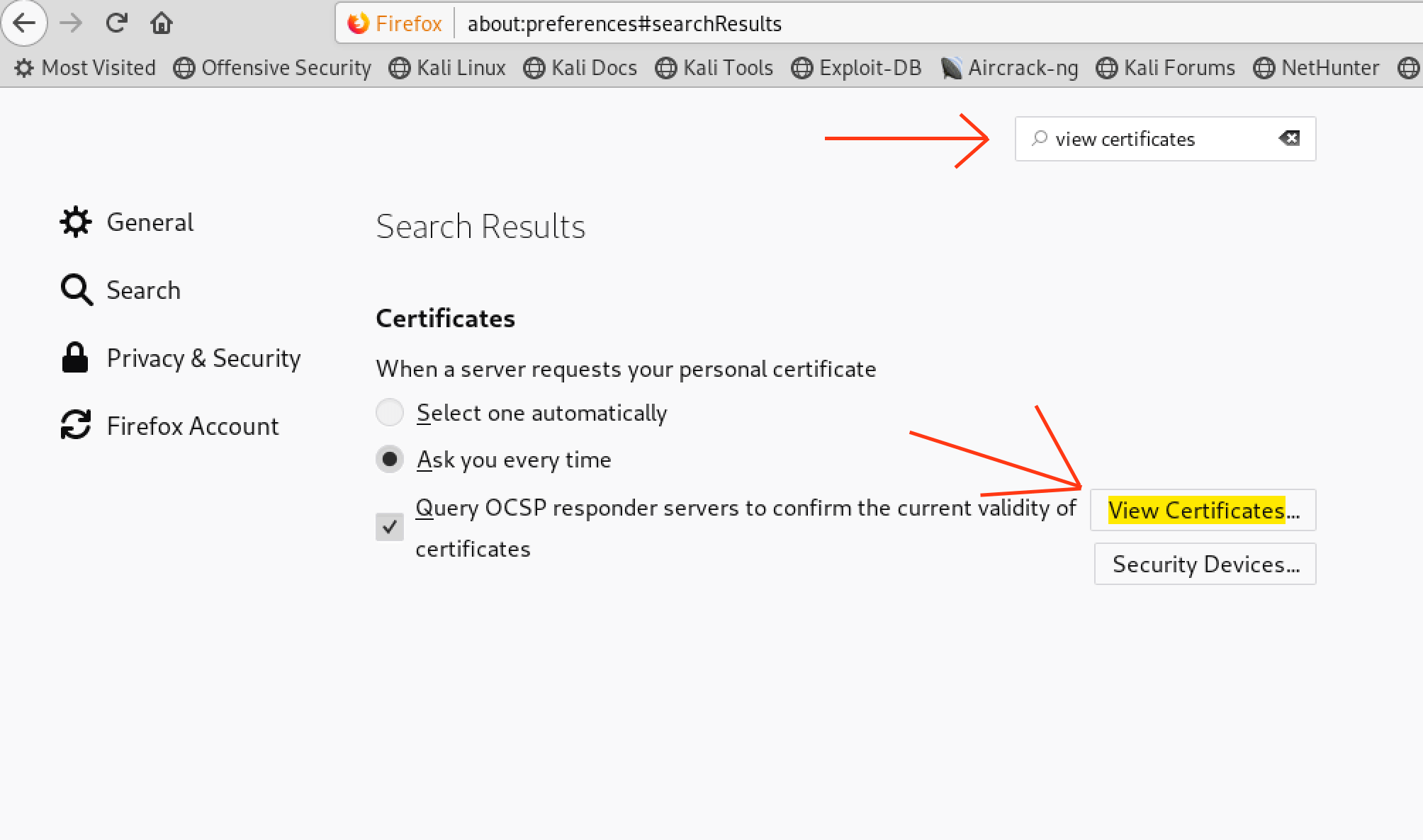
Step 2 – Import the BURP CA certificate fire fox, you’ll need to go to preferences > type “view certificates” in the search bar > click on import > and select the certificate you downloaded in step 1.
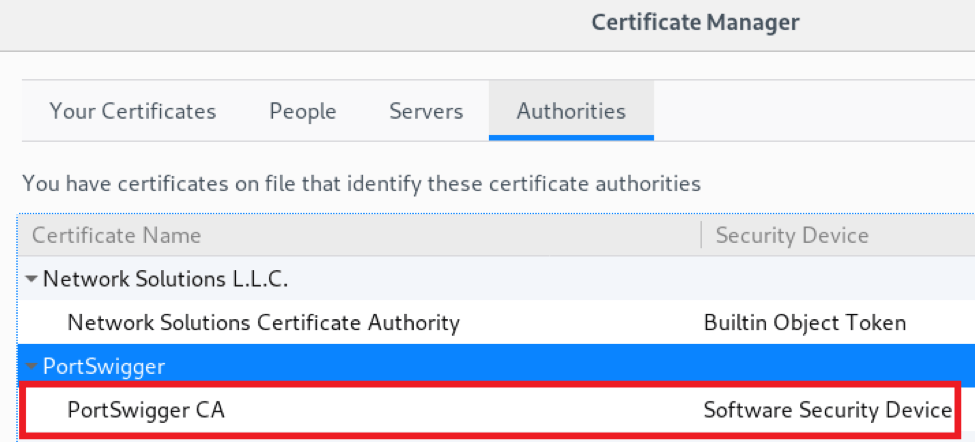
Once done you should see the certificate as shown below
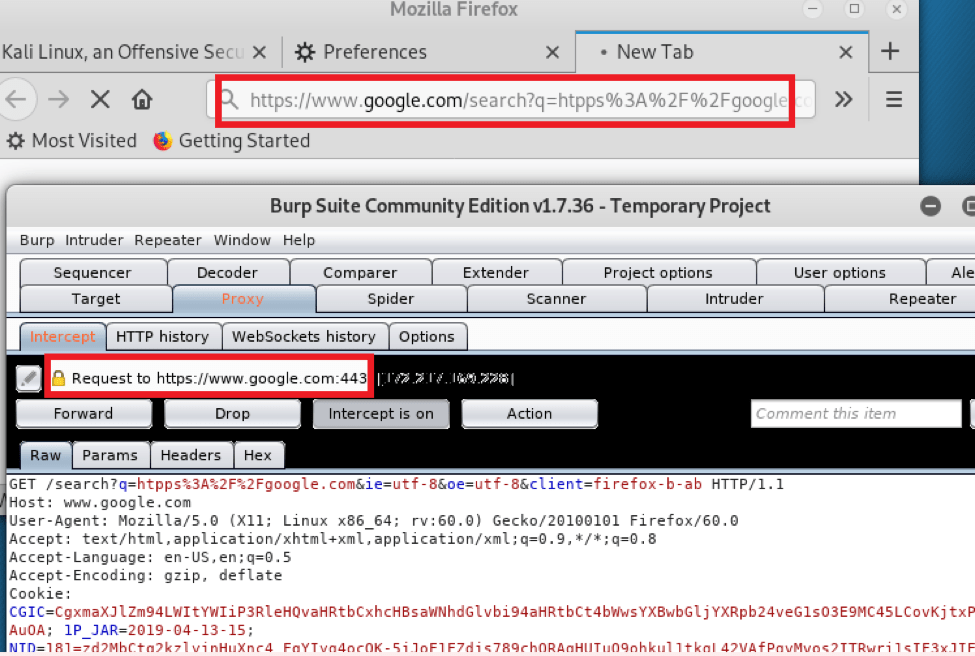
Step 3 – Upon intercepting the HTTPS request (for e.g. browsing google.com) burp shows the following
Step 4 – As I press the forward button in Burp, my browser shows the following error
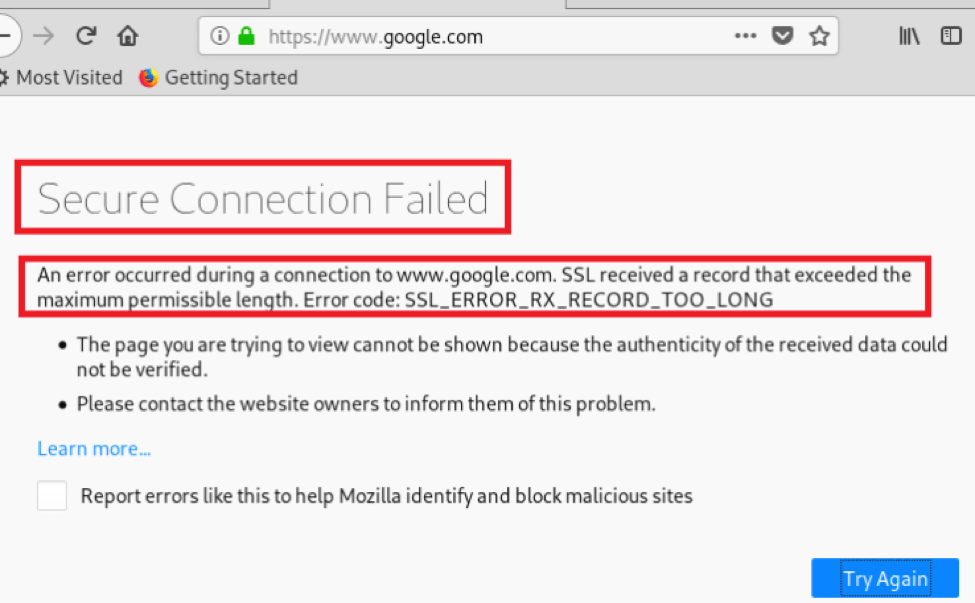
This happens because the browser and burp are still not configured to handle HTTPS properly.
Solution for the above error:
Step 1 – Configure Burp Proxy in your Fire fox as mentioned below (To go access the proxy settings in FireFox go to Preferences and Type “proxy” in the search bar)
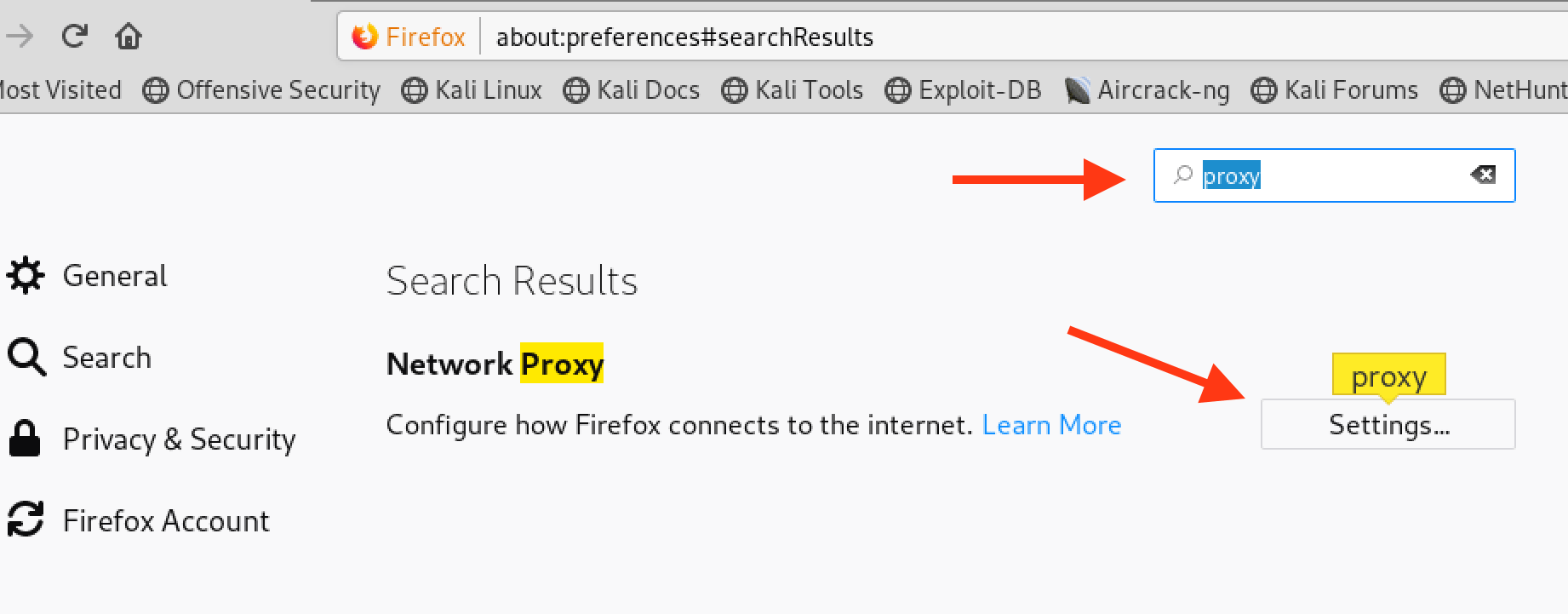
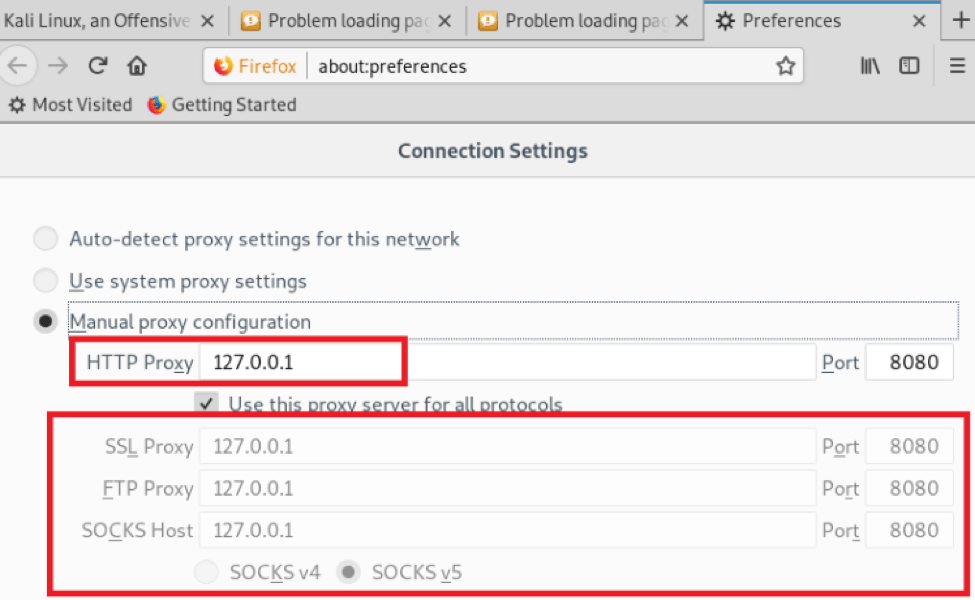
Step 2 – Type about:config in the url bar, hit enter. Search for “security.tls.version.max” and set 3 as the value instead of 4.
Step 3 – Also Add the Rule in Burp to intercept the HTTPS requests
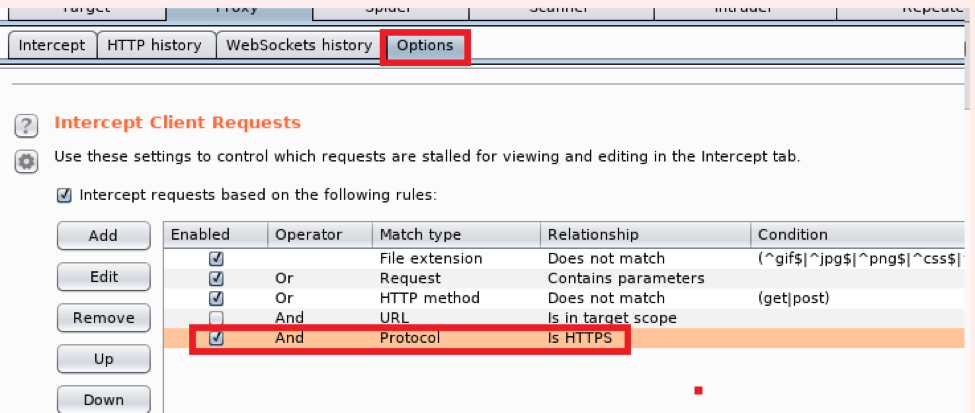
Step 4 – Downgrade the default Java version to Java 8, to do so open your Kali Linux terminal and enter the below highlighted red command as shown in the snap shot
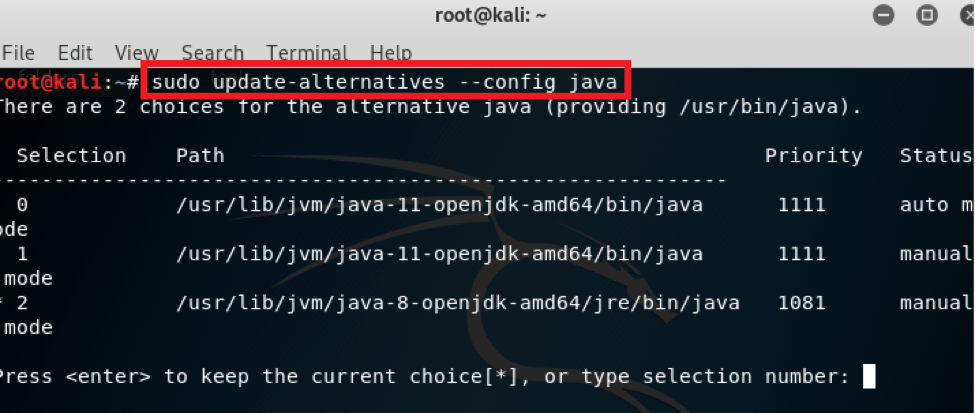
Step 5 – Type number 2 to select Java 8 and just press enter and close the terminal then (you’ll only need to do this once).
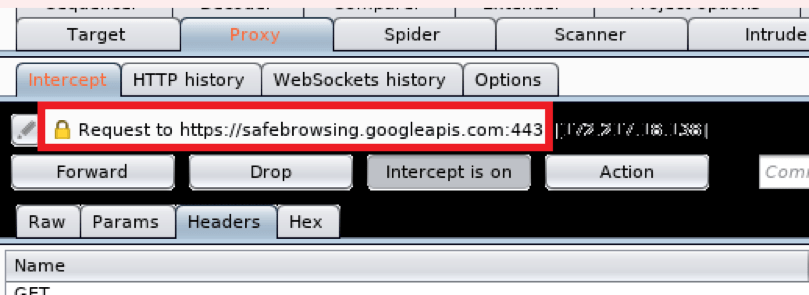
Now go the Burp turn on the Intercept and your browser should be forwarding requests sent from HTTPS pages to burp, and burp should be able to intercept them as shown below: