How To Use Metasploit Auxiliaries
As we all know Metasploit is a huge framework and can be used to do a lot of tasks. In this article we will see how to use Metasploit’s auxiliary modules. These modules are very helpful in so many scenarios such as scanning, information gathering and much more, in this tutorial I will show you how to use a port scanner but you can follow the same steps to use most auxiliary modules.
So. let’s get started
1. First start the Metasploit framework by just running the command msfconsole on terminal.
2. Now to see all the auxiliary modules available in Metasploit just type command:
show auxiliary
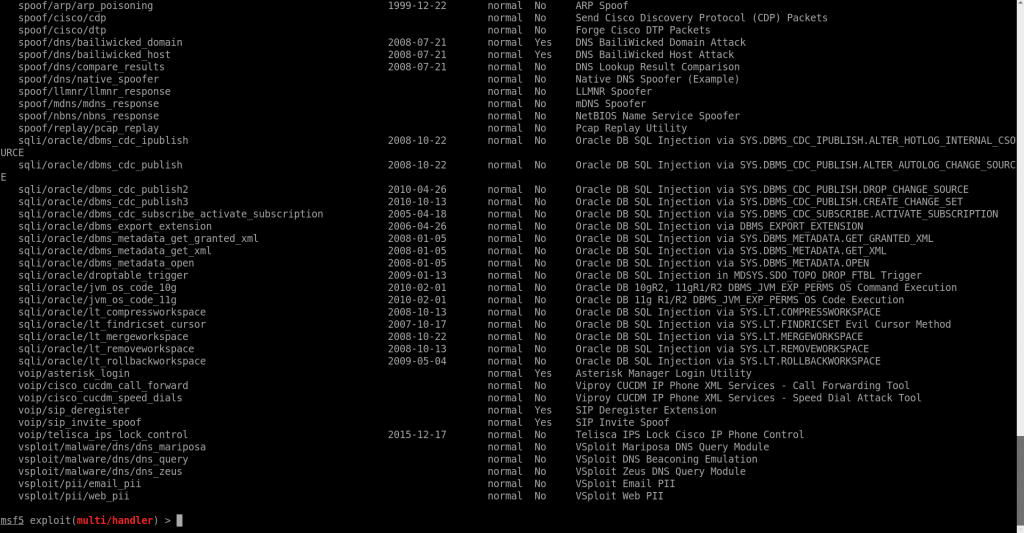
As you see there are a lot of modules, you can see we also have a description of each so just use as per your requirement.
3. I am going to use an auxiliary that does a tcp port scan, so I’m going to use the “use” command followed by the auxiliary that I want to use:
use auxiliary/scanner/portscan/tcp
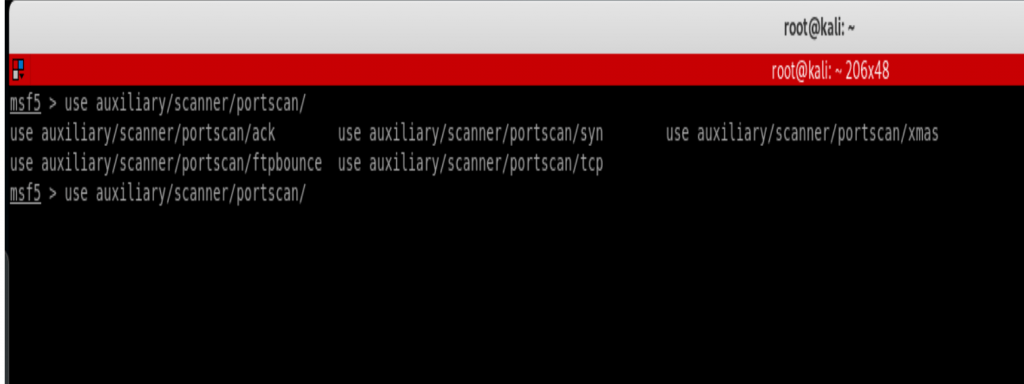
Just like using anything in the Metasploiot framework, if you’re stuck at any point just hit double tab to see all the available modules as shown below
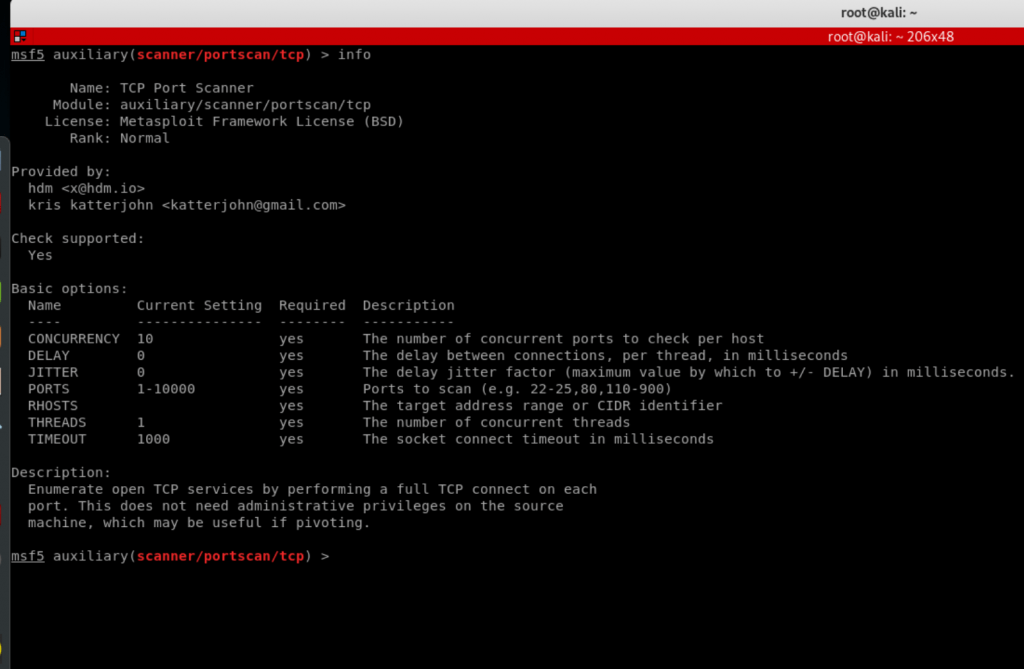
We can also use the “info” command to get more information on a specific module (or auxiliary in this case) and see all the options that we can set:
4. Now we need to change the options so the module runs on our target, I am going to run this module against another virtual machine in my network, this virtual machine is running metasploitable so it should have a number of open ports, so the main option that I need to set is the RHOST which is the IP of the machine that I want to run this module against, changing the options here is the same as changing it in any other Metasploit module, it follows the following format
set [option name] [option value]
So in my case [option name] is RHOST and [option value] is 10.0.2.9 which is the IP of the target machine, therefore the command is:
set RHOST 10.0.2.9
I’ll also change the number of threads by running
set THREADS 50
5. And finally we can run “info” again just to make sure that all the options are set as we wish and then use the “run” command to run the module, give it sometime and you’ll get the results in the same window.
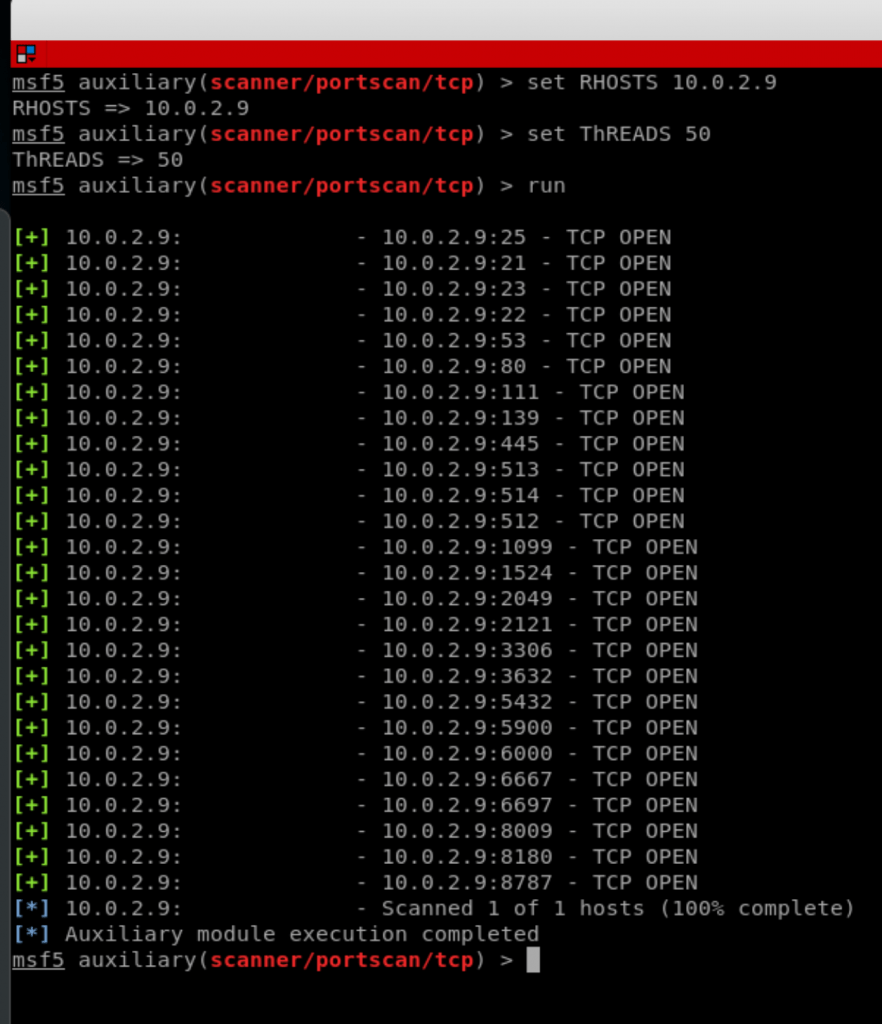
So this is just a simple example of using an auxiliary in Metasploit, in here we used a port scanner but you can use most modules the same way, so the main steps are:
1. List all auxiliaries:
show auxiliary
2. Select an auxiliary.
use [auxiliary name]
3. Get more info about it
info
4. Set options.
set [option name] [option value]
5. Confirm changes.
info
6. Run the module.
run
Leave A Reply
You must be logged in to post a comment.





2 Comments
Thank You bhaji. I was looking for something like this . I am trying to learn Metasploit using payloads and stuff like this . .
Thanks veere