Hacking Webcams & Microphones
Whether you want to catch criminals in the act, or see what you can gather about them for the cops, one important part of hacking is accessing webcams and microphones. There are so many ways in which you can actually do this, but the easiest of them all is by using Storm-Breaker. Storm breaker can get information of any device without any permissions, it can access smartphone location, grab OS passwords, access webcam, and lastly access microphones. In this tutorial, we’ll learn to access webcams, and microphones, grab smartphone locations, as well as grab OS passwords.
Step #1: Installing Storm Breaker
First, let’s install Storm Breaker.
git clone https://github.com/ultrasecurity/Storm-Breaker cd Storm-Breaker sudo bash install.sh python3 -m pip install -r requirments.txt
Step #2: Installing Ngrok
In order for Storm Breaker to work, we also need to install ngrok. First, you need to sign up for an ngrok account at https://dashboard.ngrok.com/login. Once you sign up for an ngrok account, a dashboard will open up with instructions as well as a download link. Download ngrok, and extract it into the Storm-Breaker folder. Make sure that the ngrok is in the Storm-Breaker folder!!! Now use the terminal to do the following:
cd Storm-Breaker ./ngrok authtoken [token]
Here, replace [token] with the token that the ngrok site gives you. Now you’re ready to start Storm-Breaker.
Step #3: Starting Storm-Breaker
In order to start Storm-Breaker, you must be root. So you might as well login in as root, and then type:
sudo su python3 Storm-Breaker.py
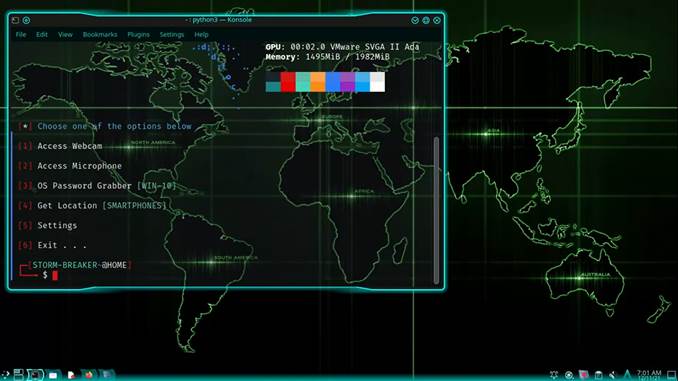
Once Storm-Breaker is started, you’ll have 6 options. The 5th and 6th options are the settings and the exit options, so we’ll omit those. The options are as follows:
- Access Webcam
- Access Microphone
- OS Password Grabber (WIN 10)
- Get Location [Smartphones]
- Settings
- Exit
Accessing the Webcam and microphone
First, let’s access the webcam. In order to access the webcam, you must enter the number 1 into the console, and press enter. You’ll get 3 options, I’m going to try to access the camera of a smartphone so I’ll pick option 2.
- Default
- Mobile Camera
- Avatar X-Men
So, it’ll give you a link. In my case, it looks something like this:
https://6375142-118-155-103.ngrok.io --> https://localhost:4545
Now, the link you want to use is the first one (https://6375142-118-155-103.ngrok.io).
The next line after the link is “Please send link to your target”. So we have to send it to our target! Open gmail, and craft an email and add the link. Or SMS the link to your target. Once they open the link, you’ll get nice photos!
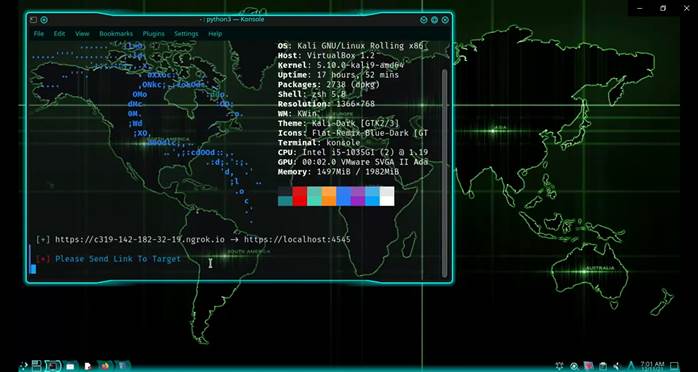
Once they open the link, you’ll get their IP address, their system information, as well as nice photos taken by their camera!! These photos will be stored at /Storm-Breaker/webcam/images.
If you are successful, then you should get a screen like this (I’ve blurred out my IP address, and OS Name)
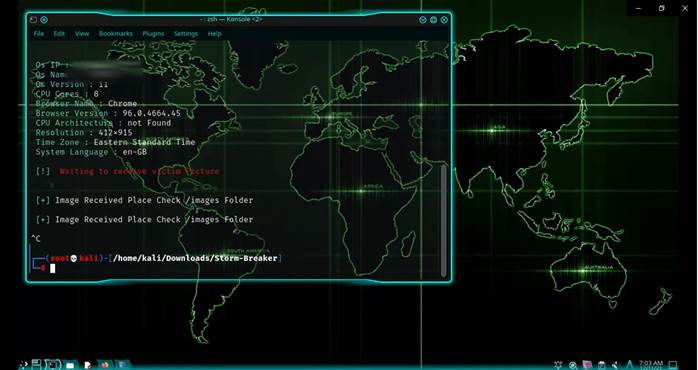
You may notice that it says “Image Received Place Check /images Folder”. This is where it will tell you where to check for the files it has collected!
In order to access the microphone, you’d have chosen option 2, instead of 1, but the rest of the process is still the same. You’ll get to choose a template, and you’ll get a link which you have to send to the target. Here, the data collected will be stored in the /Storm-Breaker/microphone/play folder.
Accessing OS Passwords
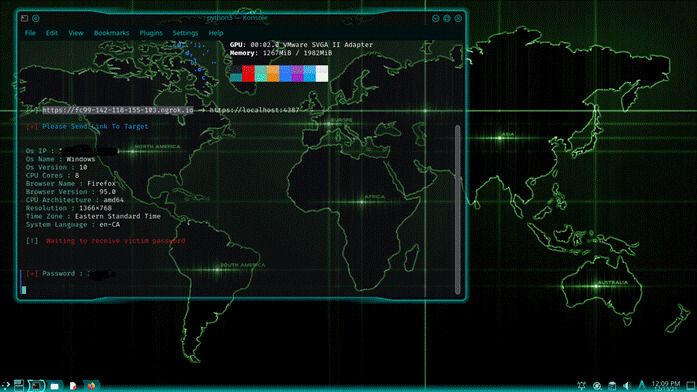
The next thing we’ll be accessing is OS Password. For this, we select option 3. You should immediately get a link much like for the webcam. Send this link to your target.
When the person opens this link, they will be asked to click on another link that will simulate a windows login. It looks real enough, and when they enter their password in order to login, the password will appear on your terminal’s screen.
I have erased the IP and the actual password from the image below:
Accessing Locations
Accessing locations is no different from accessing webcams. We simply choose option number 4. Here, you’ll get two different templates, a nearyou and a weather template. You can pick one. I’ll pick the weather template.
- Nearyou
- Weather
Once again, you’ll get a link that you can send to your target. If they click on it, then you should get location information of your screen.
Hacking is not always easy, it takes time, patience, and knowledge of lots and lots of techniques. However, with Storm-Breaker, hacking has just become simple. It’s as simple as installing a few components, and firing it up. Once it’s up and running, you’ll get the option of hacking into a variety of things including webcams, and microphones. Always remember to work with the force (police, and federal agents), not against.
Happy Hacking!




