Metasploit is one of the most popular and most used hacking tools, it can be used for exploit development, information gathering, fuzzing, exploitation and more! this video will introduce you to this amazing framework and teach you how to use …
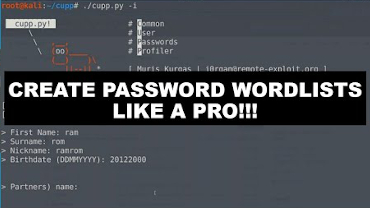
In this video I’m going to show how to create password wordlists that can be used for WiFi password-cracking, Bruteforce login-pages…etc Resources Cupp git repo
What is Wireshark ? How to use it ? Well this video will introduce you to this amazing tool and walk you through its basics. Installation – Linux: To Install Wireshark on Linux apt-get update sudo apt-get install wireshark Installation …
This video will introduce you to Hack The Box which is a platform designed to help you practice hacking legally. It contains a number of machines designed to simulate real life pentest scenarios so you can practice hacking legally.
Hey Guys , I am back , in todays tutorial I’ll be showing you how to crack/brute-force password protected files using a tool called Zydra. Requirements: 1.Python 3.3 or higher 2.Operating System Preferbally Debian Based Installation: 1.sudo apt-get update …
Hey Guys , in this video we’ll be talking about Malware Analysis. We’re gonna introduce you to the basics so you can expand more and learn more about this topic if you’re interested in it. Resources: The Slides Shown : …