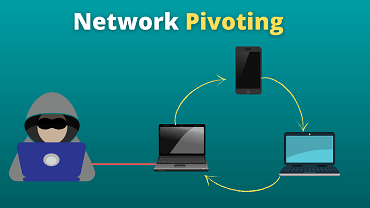
Hey guys, In this video, we are going to see how to pivot between networks using SSH Tunneling and Proxychains.
Hey guys, In this video, we will talk about hashes and hashing, how to generate hashes and how to crack them.
Hello everyone, I am back with another video on OSCP Buffer Overflow Series! In today’s video, we will be solving Brainpan, Brainpan is an intentionally vulnerable binary made for practicing buffer overflows. You can download the binary from the link …
This video shows the most common method that hackers rely on to hack wordpress websites. All of this is done on our lab, the zSecurity Comment CTF which can be accessed at the bottom of this page or from this …
Hey guys, In this video, I will cover how to use Metasploit exploits and how to generate Metasploit payloads. Resources: Official Metasploit website
Hey guys! The following video shows you how to configure Kali Linux to route traffic through the TOR network to improve your privacy and anonymity.