In this video, I will be showing you an overview of the network attack tool called Fluxion which uses the evil twin attack method to capture the network key. Resources: Fluxion google drive download link: https://drive.google.com/file/d/1Oy2QV8SCAPWxOXSKGotBrc_2oP_LtV34/view
In this video, I will be showing you an overview of the IP location tracker in IPlogger. Enjoy the video 🙂 IP Logger website: https://iplogger.org/
In this video, I will be showing you how hackers use hashcat to crack WiFi networks using PC’s GPU. I’m using my Netgear router as an example since Netgear routers use a weak password combination. The main goal of this …
Hey guys, In this video, I will be showing you how hackers use bettercap to capture traffic and modify them on your local network using a Man in the middle attack terminology. The main goal of this video is how …
This video shows how to increase the probability of cracking WPA and WPA2 networks using wordlist attacks. To achieve that we rely on information gathering or open source intelligence (OSINT) to figure out the format used by our targeting to …
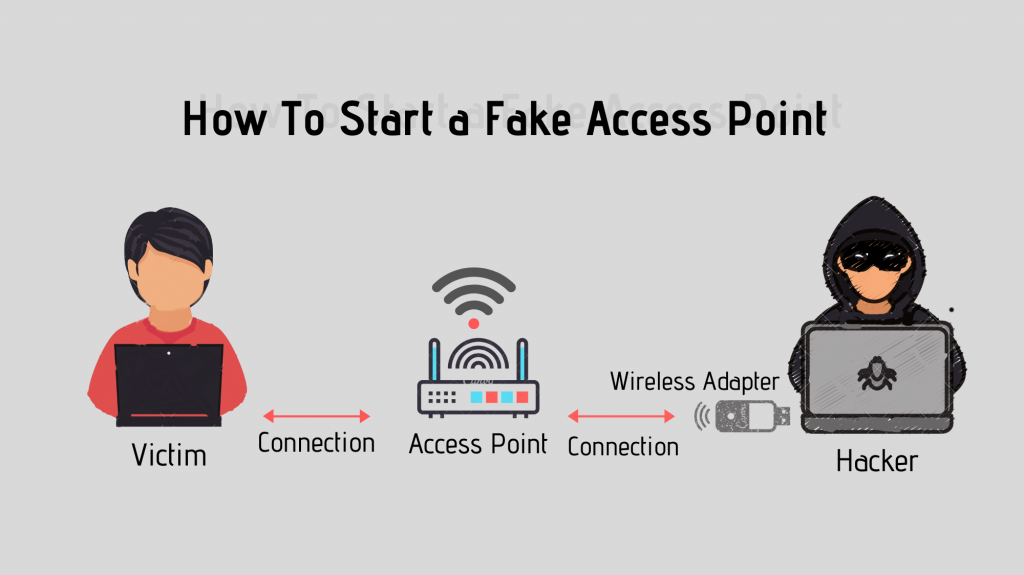
As you might know, untrusted Wifi networks can be extremely dangerous if you happen to be connected to them. In this article I am going to show you how to create a simple yet dangerous access point. We will …