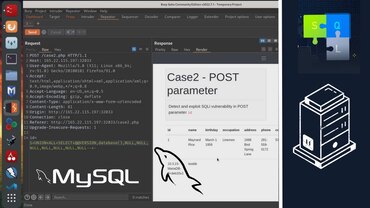
Running Sqlmap against a basic HTTP post
SQLMap is a free and open-source penetration testing tool written in Python that automates the process of detecting and exploiting SQL injection (SQLi) flaws. SQLMap has been continuously developed since 2006 and is still maintained today. SQLMap comes with a powerful detection engine, numerous features, and a broad range of options and switches for fine-tuning the many aspects of it.
Supported SQL Injection Types
SQLMap is the only penetration testing tool that can properly detect and exploit all known SQLi types. We see the types of SQL injections supported by SQLMap with the sqlmap -hh command.
The technique characters BEUSTQ refers to the following:
B: Boolean-based blind
E: Error-based
U: Union query-based
S: Stacked queries
T: Time-based blind
Q: Inline queries
In this Sqlmap tutorial, we will explore how to use Sqlmap, a popular SQL injection testing tool, against a basic HTTP POST request that contains POST data. We will walk through the process of setting up a testing environment, capturing and analyzing the HTTP POST request, and running Sqlmap to automatically detect potential SQL injection vulnerabilities.
But that’s not all! We will also dive into manual payload testing. Once Sqlmap has detected potential vulnerabilities, we will manually test the payloads to understand how they work and how to exploit them effectively. We will analyze the responses from the target web application and understand how to interpret the results provided by Sqlmap.
This tutorial is perfect for ethical hackers, penetration testers, and anyone interested in learning about SQL injection testing and manual payload testing using Sqlmap. Whether you’re a beginner or an experienced professional, this tutorial will provide you with valuable insights and practical knowledge.
Topics covered in this tutorial:
Setting up a testing environment
Capturing and analyzing HTTP POST requests with POST data
Running Sqlmap against a POST request
Understanding Sqlmap results and vulnerabilities detected
Manual payload testing and analyzing responses
Exploiting SQL injection vulnerabilities
If you’re looking to enhance your web application security testing skills or are simply curious about SQL injection testing and manual payload testing, then this tutorial is a must-watch! Don’t miss out on learning how to effectively use Sqlmap to detect and exploit SQL injection vulnerabilities in a basic HTTP POST request. Subscribe now and hit the bell icon to stay updated with our latest tutorials on ethical hacking and cybersecurity!