Hydra is one of the most popular tools to run wordlist and brute force attacks, it supports a huge amount of services and can be used on all operating systems. This video will introduce you to this amazing tool, walk …
Most people use Hydra to run wordlist attacks, in this video however I’m going to show you an easier method to do this using burp suite.
Hello guys, In today’s video I will be showcasing a good mass scanner that uses facial recognition to find social accounts associated with a profile picture. This tool is pretty powerful when it comes to information gathering , watch the …
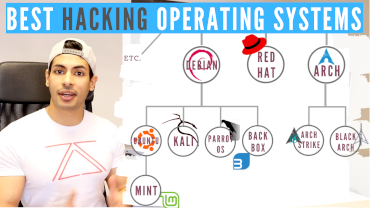
I made this video to answer a very common question that I get: What is the best operating system for hacking? is it Kali Linux? Parrot OS? and do real hackers use these operating systems?
Steganography is the practice of concealing messages or information within other non-secret text or data. In todays video I’m going to show you how to apply this in real life and hide text data inside an image!
In this article, we will see what is phishing? How dangerous is it? And how to use hidden eye to do phishing. What is Phishing? Phishing is the fraudulent attempt to obtain sensitive information such as usernames, passwords and credit …