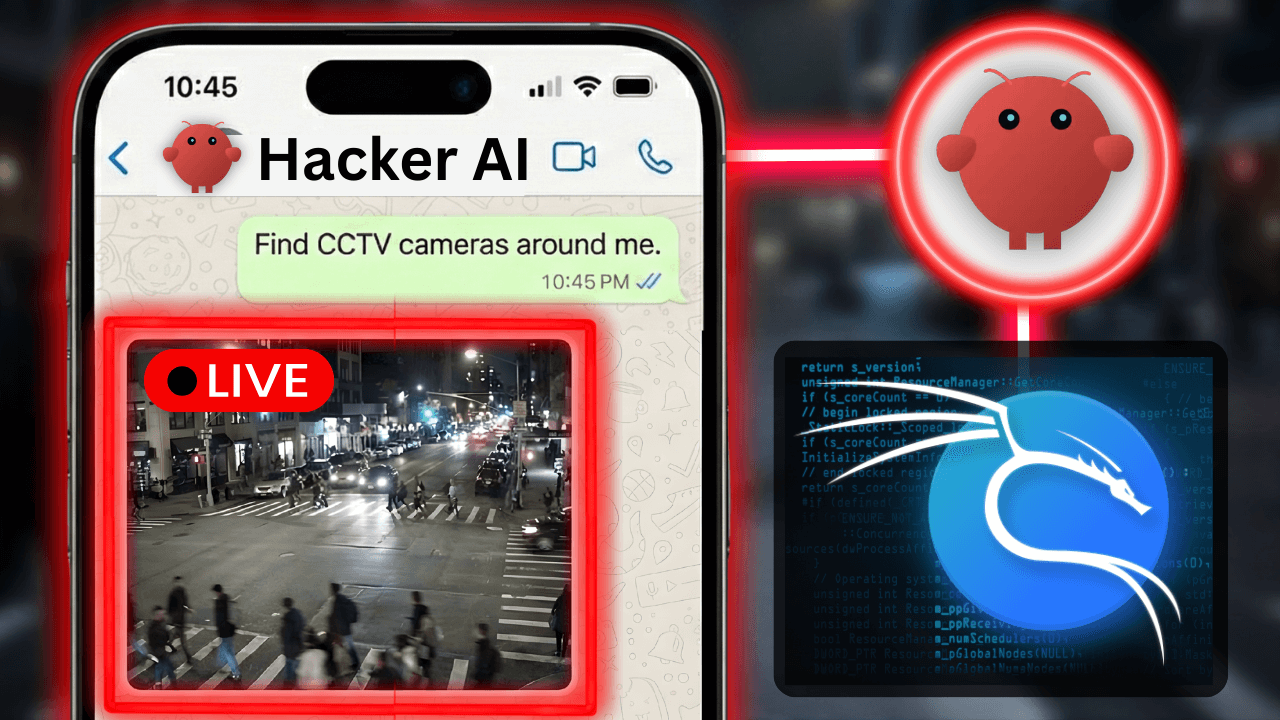
In this video you’ll learn how to build a fully autonomous AI hacking rig using OpenClaw running on a Kali Linux cloud server. Unlike standard AI chatbots, this agent has direct access to tools like Nmap, Metasploit, and the web …
TRACK Instagram Posts – OSINT FREE Tool Hey there, welcome to CyberSudo! I’m Saad Sarraj, and here we break down OSINT and Cyber Security in a simple, beginner-friendly way. In this video, I’ll show you how OSINT investigators can find …
Hackers Can TRACK Emails with this Tool Hey there, welcome to CyberSudo! I’m Saad Sarraj, and here we break down OSINT and Cyber Security in a simple, beginner-friendly way. In this video, I’ll show you how Hackers Can TRACK Emails …
TRACKING a Phone Number Using OSINT Hey there, welcome to CyberSudo! I’m Saad Sarraj, and here we break down OSINT and Cyber Security in a simple, beginner-friendly way. In this video, I’ll show you how your phone number can reveal …
Extract ADMIN Emails with OSINT Hey there, welcome to CyberSudo! I’m Saad Sarraj, and here we break down OSINT and Cyber Security in a simple, beginner-friendly way. In this video, I will share with you how OSINT investigators Extract ADMIN …
Reverse Image Search EXPOSES You Hey there, welcome to CyberSudo! I’m Saad Sarraj, and here we break down OSINT and Cyber Security in a simple, beginner-friendly way. In this video, I’ll show you how something as innocent as uploading a …