A step-by-step guide teaching you how to discover and exploit IDOR vulnerabilities + xp_cmdshell + local buffer overflow to hack a RaaS (Ransomware-as-a-Service) platform and gain full remote control over their servers. Check out the video below: Hacking the Hackers …
This video will show you how hackers can hack cryptocurrency and how to secure your crypto from the mentioned methods.Check out the video below: How Crypto Gets Hacked? ————————————————————————————Resources:How Phishing Links Are Generated: https://www.youtube.com/watch?v=2crXwg-a_SQCrypto scam tracker: https://dfpi.ca.gov/consumers/crypto/crypto-scam-tracker/LaZagne: https://github.com/AlessandroZ/LaZagneMimikatz: https://github.com/gentilkiwi/mimikatz————————————————————————————Maythom social media:Personal Youtube channel: @maythomPatreon: https://patreon.com/MAYTHOMInstagram: https://www.instagram.com/mayth0m Twitter: https://twitter.com/mayth0m————————————————————————————-zSecurity …
This video showcases a tool named Xeuledoc that can extract metadata from publicly shared Google documents such as Docs, Sheets, and Slides.
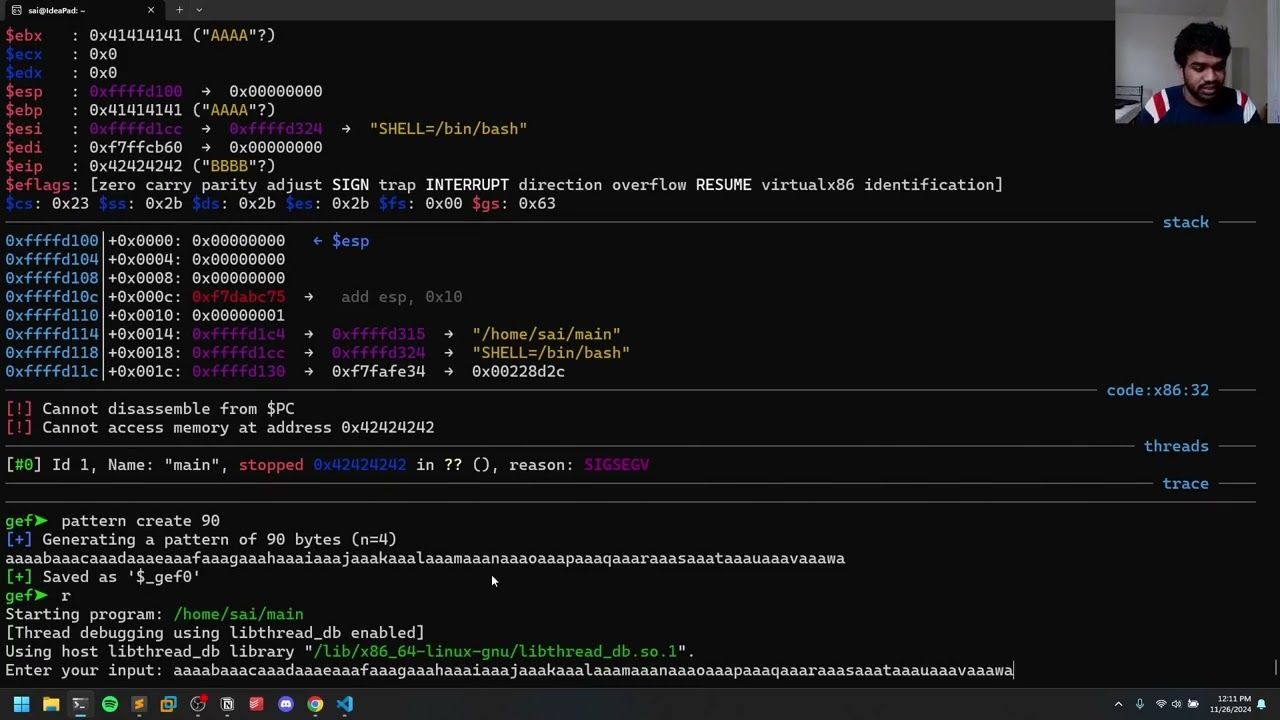
This video explains the concept of return-to-libc attacks in binary exploitation. The discussion focuses on how to exploit a vulnerable program using the ‘libc’ library to execute a shell without directly calling system functions in the code.
This tutorial teaches you how to decrypt SSL/TLS traffic using the SSL key log file environment variable on various operating systems, including Linux, Windows, and Mac. You will learn the significance of decrypting traffic for both attackers and defenders, and …
The advent of Generative AI has revolutionized numerous domains including cybersecurity. Generative AI is a type of artificial intelligence that can create new content, such as text, code, images, and music. It is trained on massive datasets of existing content, …