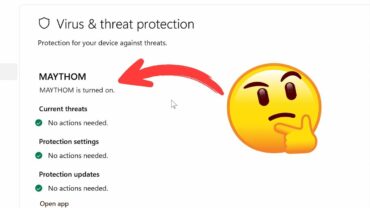
How Hackers Disable Defender With 1 Command Hey guys! In this video, we will discuss how hacker might be able to disable windows defender and how to detect and prevent it. If you’re into bug bounties or just poking around …
In today’s digital landscape, protecting your privacy and bypassing censorship is more critical than ever. While numerous VPN services exist, trusting a third-party provider with your data can be a gamble. What if you could make your own insanely fast …
Hey guys! In this video, I’m gonna show you how to find Hidden Passwords & secrets hiding in web apps like API keys, tokens, and passwords devs accidentally leave behind. I’ll be using Gitleaks, a solid tool that helps dig …
Learn how to find ANYONE’s email associated with Github accounts and Google drive files using two different OSINT techniques. In today’s hyper-connected world, our digital footprints are larger than ever. While we might think certain information like our email address …
Did you know Google once paid nearly $150k to a security researcher for discovering a single SSRF vulnerability? That vulnerability was Server-Side Request Forgery (SSRF), a potentially devastating flaw that can allow attackers to manipulate web servers. If you’re interested …
Hey guys! In this video, we will discuss how to generate a payload and a listener via Empire, and trick users into clicking a .pdf shortcut that has that backdoor. This is How Hackers Take Over Your Device! Empire is a …