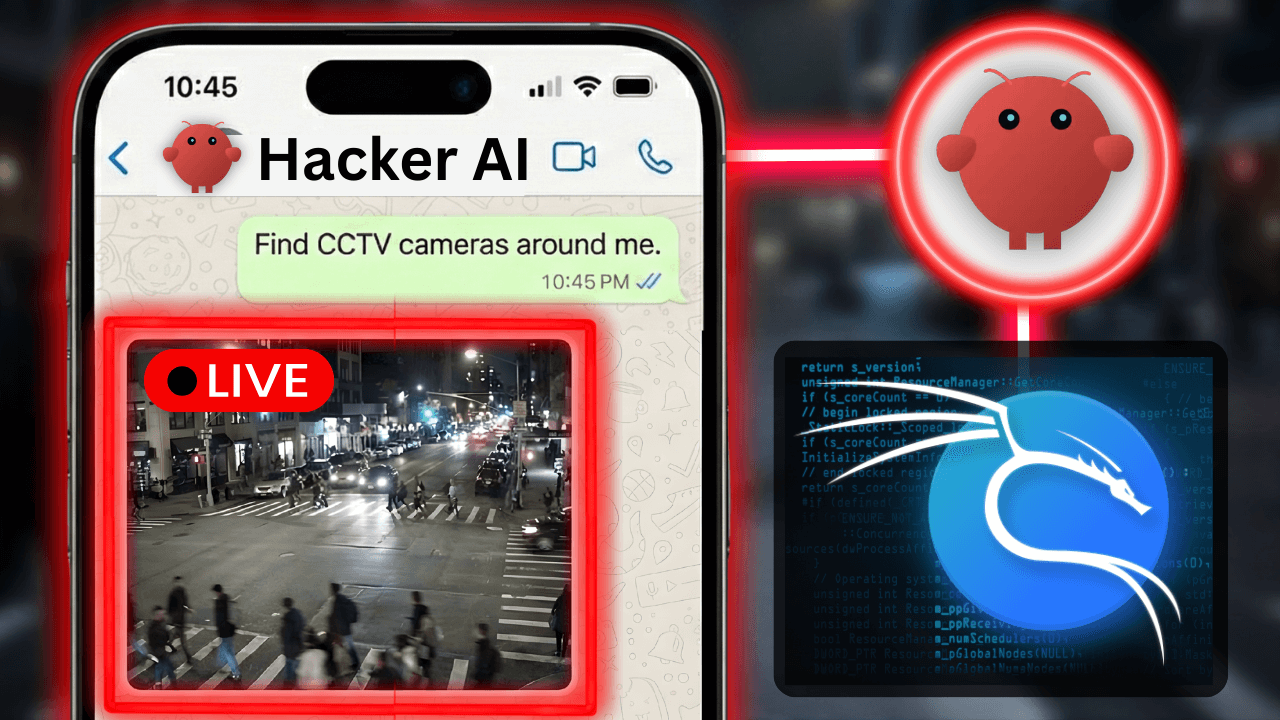
In this video you’ll learn how to build a fully autonomous AI hacking rig using OpenClaw running on a Kali Linux cloud server. Unlike standard AI chatbots, this agent has direct access to tools like Nmap, Metasploit, and the web …
Hack WhatsApp & Gmail of Anyone & Bypass 2FA / MFA This video shows how the Browser in the Browser attack is used by hackers to bypass two factor and multi-factor authentications (2FA / MFA) and one time passwords (OTP). …
Run YOUR own UNCENSORED AI & Use it for Hacking Have you ever tried to use a popular AI for a cybersecurity project, only to be met with: “I’m sorry, I cannot fulfill this request”? Most commercial AI models have …
This video shows how hackers use command and control servers or C2 to manage hacked android devices. Resources:
Most people still trust their antivirus software to keep them safe, but Your Anti-Virus Sucks far more than you think. Attackers bypass traditional detection tools every single day, and the techniques they use are now easier than ever to execute. …
Unlocking AI’s True Power: Jailbreaking ChatGPT 5, Gemini & Claude for Hacking Tired of the “As an AI language model, I cannot…”? Learn how to jailbreak ChatGPT 5, Gemini & Claude and show them who’s the boss! For demonstration and …