This video showcases a tool named Xeuledoc that can extract metadata from publicly shared Google documents such as Docs, Sheets, and Slides.
This video explains the concept of return-to-libc attacks in binary exploitation. The discussion focuses on how to exploit a vulnerable program using the ‘libc’ library to execute a shell without directly calling system functions in the code.
This tutorial teaches you how to decrypt SSL/TLS traffic using the SSL key log file environment variable on various operating systems, including Linux, Windows, and Mac. You will learn the significance of decrypting traffic for both attackers and defenders, and …
Introduction to PwnTools. In this video, we’re diving into one of the most powerful tools for exploitation and reverse engineering—PwnTools. We’ll go over everything you need to know to get started—from basic syntax and commands to creating your first exploit. …
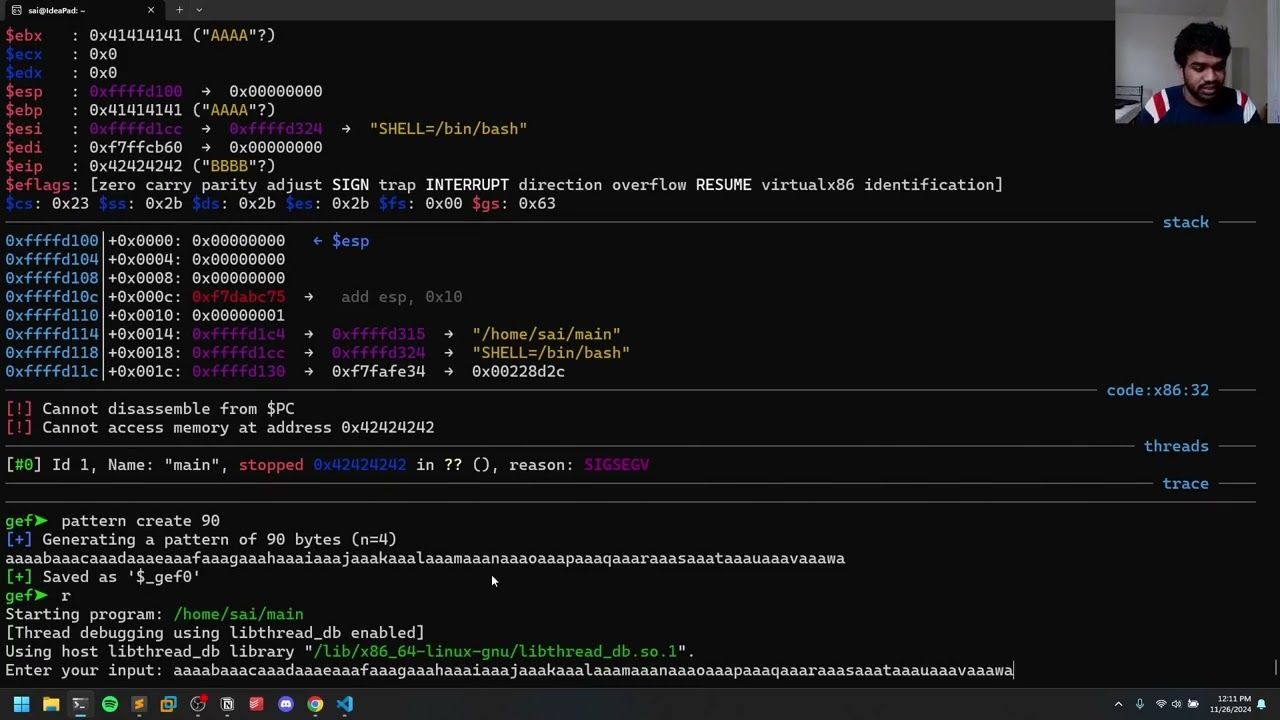
Buffer Overflows: Rewriting EIP. In this video, we will discuss the next topic in our Buffer Overflows episode. The next topic is rewriting your Extended Instruction Pointer (EIP) to control execution. 🎬 Thank you for watching this video! 🙏https://s4thv1k.com/posts/binary-expl… https://github.com/saisathvik1/binary… …
In this video, we will be covering Binary Exploitation: Stack Overflows. The goal here in the Stack Overflow is to demonstrate my code—this is a sample code that I wrote, and I’ll upload this code to my GitHub and point …