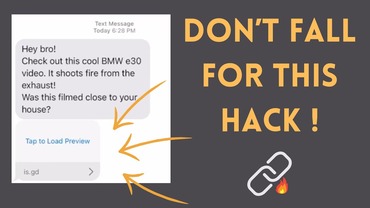
This video is designed to raise awareness on why not to click on suspicious links being sent to you as you can get hacked pretty easily as a result of that. I have discussed how to use beef and …
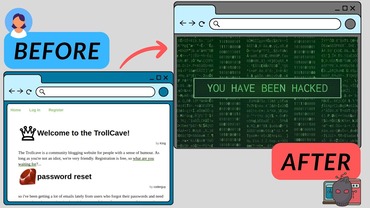
This video is designed to help developers build their websites with security in mind, and it’s also designed for ethical hackers to learn some web enumeration and exploitation techniques to secure online websites better. I showed how to deface a …
In this video, I will be showing you behind the scenes of how a malicious link may be created and sent to you. That’s why you shouldn’t click any link that looks suspicious and follow the security recommendations at the …
In this video, I will be showing you how hackers use Burpsuite to bruteforce an account password via a password change vulnerability. Once again, the devices I used strictly belong to me and this video is for educational purposes only! …
In this video, I will be showing you how hackers use Hydra to bruteforce a login page using php post method running on an http service. Once again, the devices I used strictly belong to me and this video is …
In this video, I will be showing you how hackers use image open source intelligence (OSINT) to get access to a target’s sensitive information. I will cover three main tools: exiftool, yandex, and pimeyes. Each tool has its own strengths …