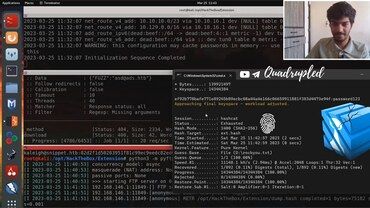
Are you curious about how hackers crack passwords? In this tutorial, we’ll explore one of the most powerful tools for password cracking: Hashcat. Specifically, we’ll show you how to use Hashcat to crack SHA256 password hashes. SHA256 is a commonly …
In the world of cybersecurity, reconnaissance is the first and most crucial step in any security assessment. In this YouTube video, we’ll explore how to perform passive reconnaissance using bash scripting and two powerful reconnaissance tools – the Harvester and …
Hello Everyone, In this video, I will be showing you how to use the harvester to perform passive reconnaissance:
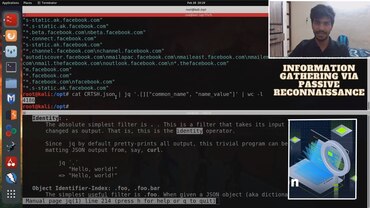
Hello guys, In this video, I will be showing you how to perform passive reconnaissance using curl and other methods!
Phishing Another very common type of XSS attack is a phishing attack. Phishing attacks usually utilize legitimate-looking information to trick the victims into sending their sensitive information to the attacker. A common form of XSS phishing attacks is through injecting …