Cracking WPA/WPA2 Using the GPU
We all know we can use aircrack-ng to run a wordlist attack to crack WPA/WPA2, in this article I’m going to show you how to do the same using a tool called HashCat, and compare its speed with aircrack-ng.
The advantage of using HashCat is unlike aircrack-ng which uses the CPU to crack the key, HashCat uses the GPU, this makes the cracking process MUCH faster (results below).
Installing & using Hashcat
- First you need to download Hashcat from https://hashcat.net/hashcat/
- Navigate to the location where you downloaded it, and unzip it, personally I like to use 7zip.
- Open the Command Prompt (go to windows search and type cmd).
- Navigate to your Hashcat folder where it’s unzipped.
- Type hashcat32.exe or hashcat64.exe depending on the architecture of your CPU.
- In order to use the GPU, you need to get its id using the following command
hashcat64.exe -I
mine is #3. Then you need to use the hash type which is 2500 for WPA, I do recommend using
hashcat64.exe --help
to get familiar with the tool.
To specify device use the -d argument and the number of your GPU.
The command should look like this in end
hashcat64.exe -m 2500 -d 3 [handshake_file] example: Handshake.hccapx" [worldlist file] "example :eightdigit.txt
Example:
hashcat64.exe -m 2500 -d 3 Handshake.hccapx eightdigit.txt
Where Handshake.hccapx is my handshake file, and eithdigit.txt is my wordlist, you need to convert cap file to hccapx using https://hashcat.net/cap2hccapx/
Results:
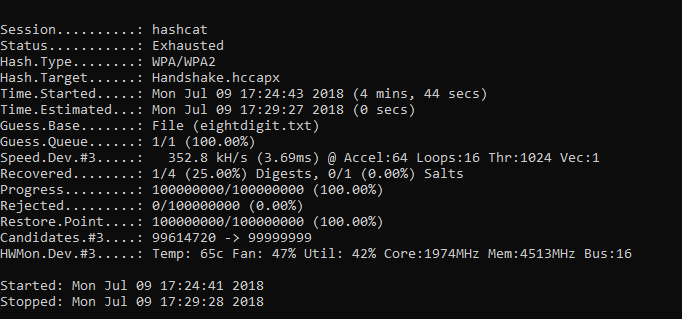
Test1: Using HashCat, with Asus GTX 1080 OC edition which has GPU Boost Clock with 1936 MHz, total GB ram of 8 Gigabytes, and Cuda cores 2560.
CUDA = Computing performance Boost Clock = Increases the Clock speed.
Hashcat took 4 mins, 45 secs to reach the end of the wordlist and crack the handshake with a wordlist of 100,000,000 passwords.
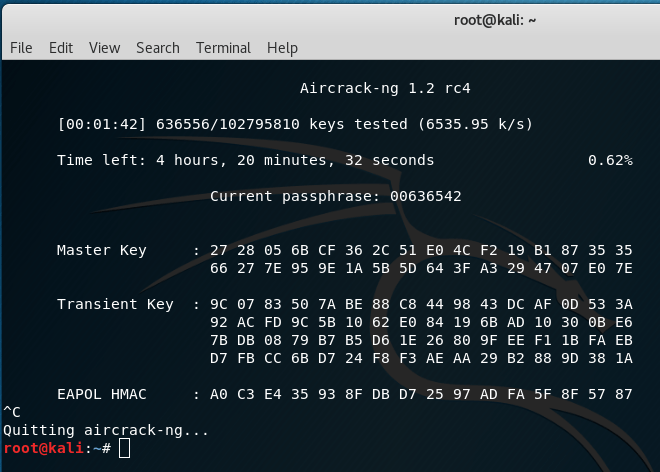
Test 2: Using Aircrack-ng on Kali installed as main operating system with is i7-7700k CPU – base clock of 4.20, turbo clock 4.50Ghz with 4 cores and 8 threads, it would take 4 hours 22 minutes 14 seconds try all the passwords in the wordlist.
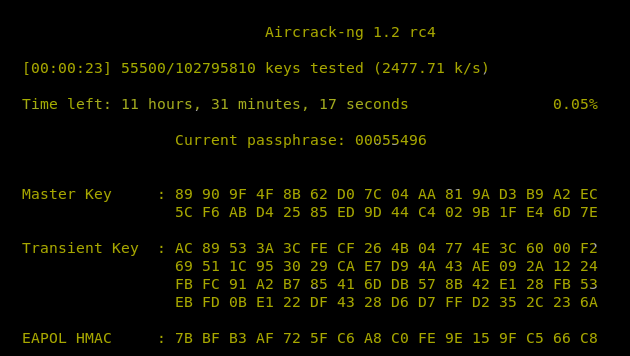
Test 3: Kali installed as a virtual machine, in this case it would take 11 hours, 31 minutes and 40 seconds to try all passwords in the wordlist!

Resources:
Leave A Reply
You must be logged in to post a comment.





1 Comment
What to do to hack WPA/WPA2 when WPS is enabled? I think it will be shorter