In this article, we will see what is phishing? How dangerous is it? And how to use hidden eye to do phishing. What is Phishing? Phishing is the fraudulent attempt to obtain sensitive information such as usernames, passwords and credit …
As mentioned in my previous video the Bitcoin blockchain is public, therefore it is important to make sure you get it anonymously if you want to protect your privacy and anonymity. This videos shows 4 methods to get bitcoins anonymously, …
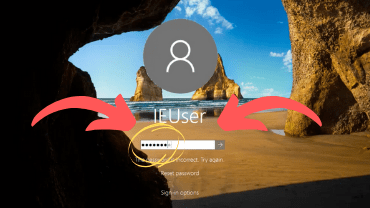
In today’s video i will be showcasing a good method on how to hack any windows 10 and get the user password too ! make sure to follow all the steps shown in the video ! If you have any …
Web app attacks increased by 52% in 2019 — here’s what to know about how web cache poisoning moved from being a theoretical vulnerability to an exploitable one Let’s face it: Nobody likes to wait a million years for a …
There is a lot of miss-conception about cryptocurrencies, this video explains what exactly is cryptocurrency, what is a blockchain and how it works, we’ll mainly talk about bitcoin but the general idea is more or less the same. This video …
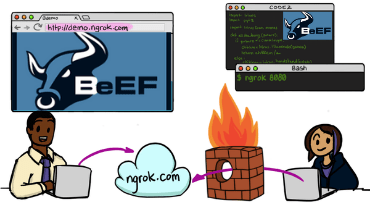
BeEF is an amazing Browser Exploitation Framework that can be used to run so many cool attacks. In the following video I’ll show you how to configure Ngrok properly to expose BeEF to the internet so you can target …