Hello Hackers! I hope you all are fine and doing safe in this pandemic! So, I made a framework in Python which can be used to generate malicious payloads and gain remote access to target machines. In this article …
Hello everyone, this article is going to be a very interesting topic not only to the ethical hackers/cybersecurity researchers but also towards the other people as here we will learn how can we make our own search engine. While there …
Hey There! Are you a ethical hacker and you program your own malware? Is it getting detected? Don’t Worry! My tool VySec is going to reduce your detection ratio to 1-3 AVs only! General Info about VySecator: VySec is made …
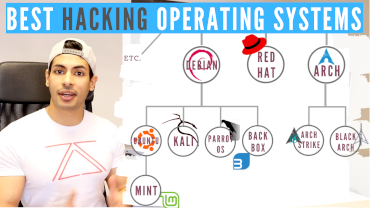
I made this video to answer a very common question that I get: What is the best operating system for hacking? is it Kali Linux? Parrot OS? and do real hackers use these operating systems?
In this article, we will see what is phishing? How dangerous is it? And how to use hidden eye to do phishing. What is Phishing? Phishing is the fraudulent attempt to obtain sensitive information such as usernames, passwords and credit …
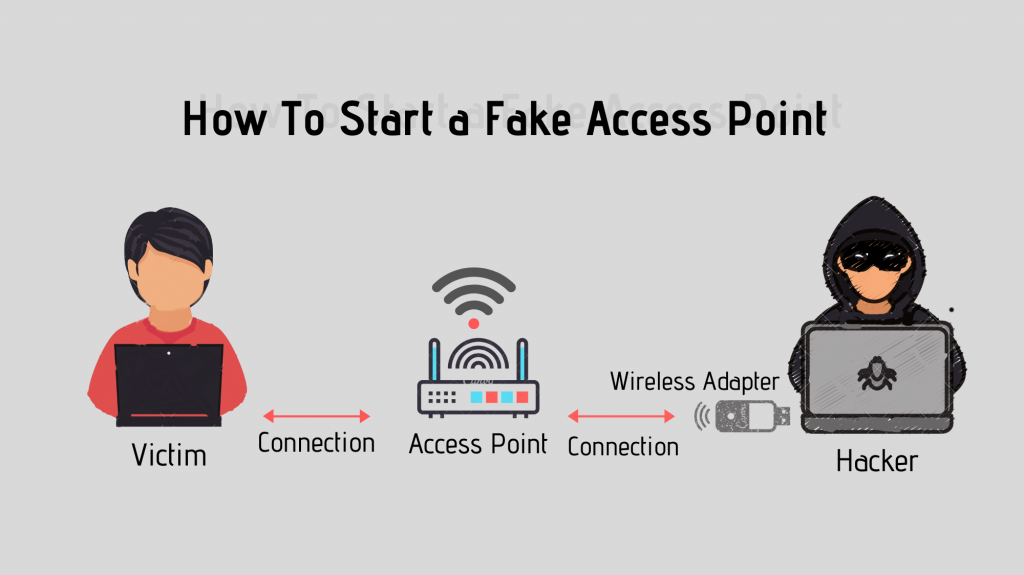
As you might know, untrusted Wifi networks can be extremely dangerous if you happen to be connected to them. In this article I am going to show you how to create a simple yet dangerous access point. We will …